Booting Into Writable Filesystem Using Grub

0. Preface
This is a very different post than the usual HackTheBox/VulnHub write-ups on this site. I managed to brick my Kali VM while testing out an exploit locally, which unfortunately, involves manually editing /etc/sudoers.
I realised I done goofed when I couldn’t run sudo, and I also didn’t set a password for the root user.
…and the last snapshot of the VM was taken a month ago.
Note that there will be some swearing involved.
1. How to Goof
Simply (and stupidly), editing your /etc/sudoers file without testing it out using visudo first.
If you edit /etc/sudoers via visudo, it will warn you if you made a mistake, and will ask you what to do next.
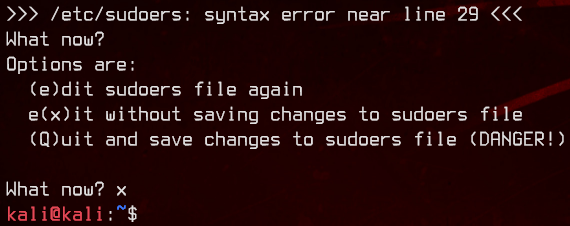
Stupidly, I just ran the following:
sudo sed -i -e '$akali ALL=[ALL:ALL] NOPASSWD:ALL' /etc/sudoers
Notice the mistake?
It’s supposed to be ( ) instead of [ ].
And this is when you know you’ve fucked up.
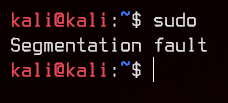
Now you can P A N I C.
2. The Fix
I desperately tried to su root with every password I can think of, but of course, it doesn’t work because there’s no password set in the first place.
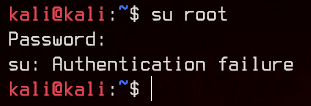
So, I tried to boot into single user mode in the hopes that I can edit /etc/sudoers with the root user.
To do so, I had to edit the bootloader script.
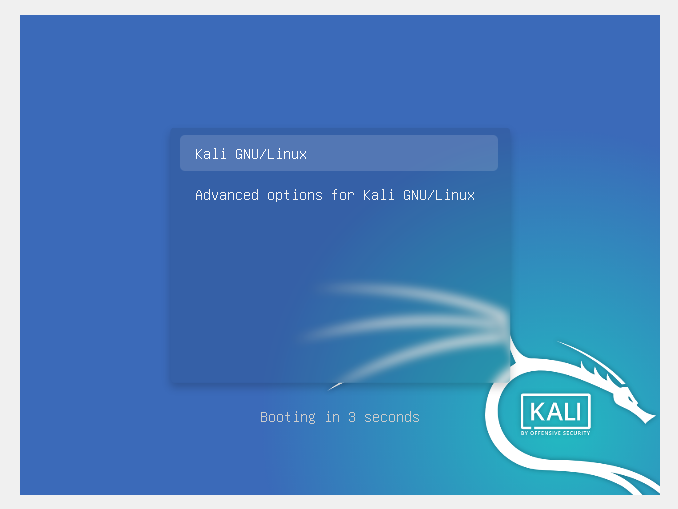
Press e to edit.
Find the following line and add a 1 behind it.
linux /boot/vmlinuz-5.7.0-kali3-amd64 root=UUID=114c498f-de75-44bb-a5ec-6339282d4171 ro quiet splash
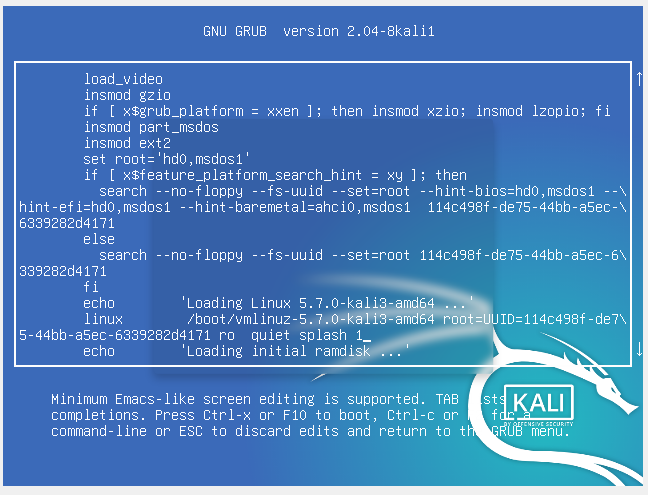
Press Ctrl+X to boot.
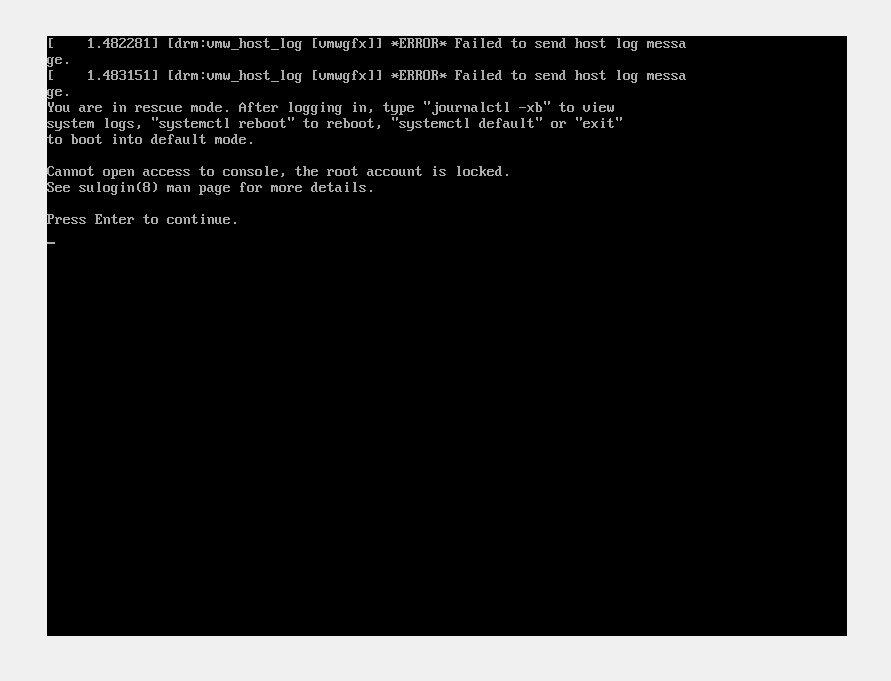
F u c k.
Cue more P A N I C.
After some research, I found that you could append init=/bin/bash instead, and change ro to rw to boot into bash directly with a writable filesystem.
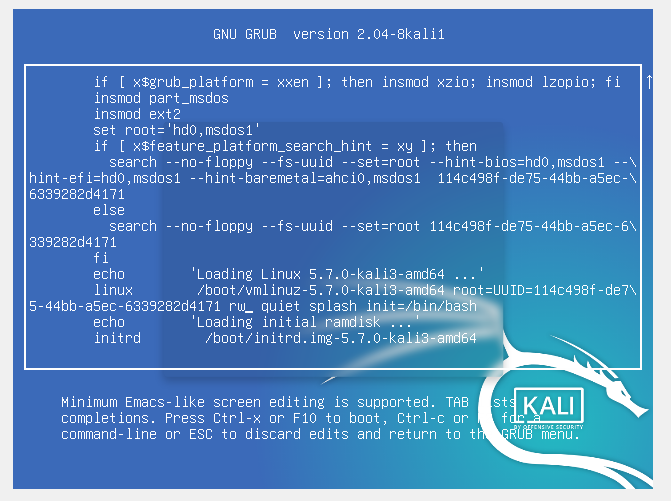
Ctrl+X.
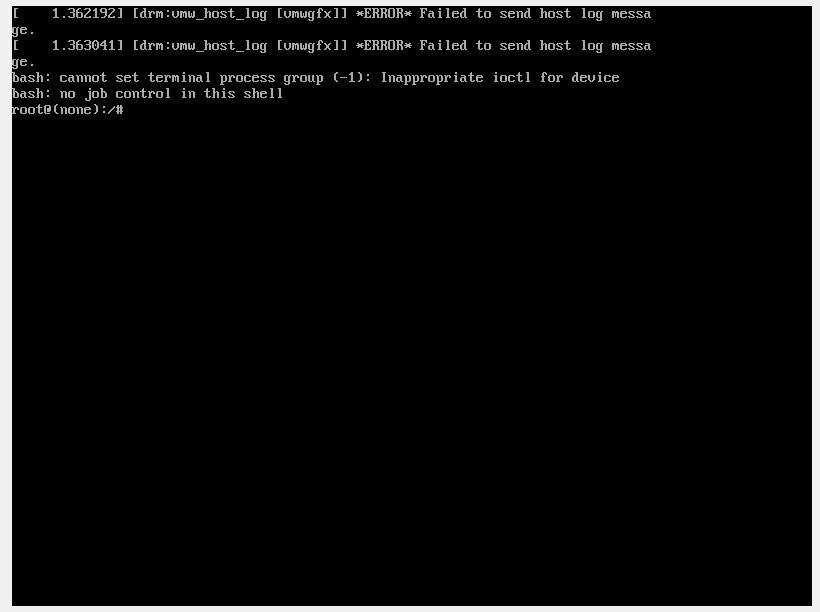

Now to revert the sudoers file, this time using visudo.
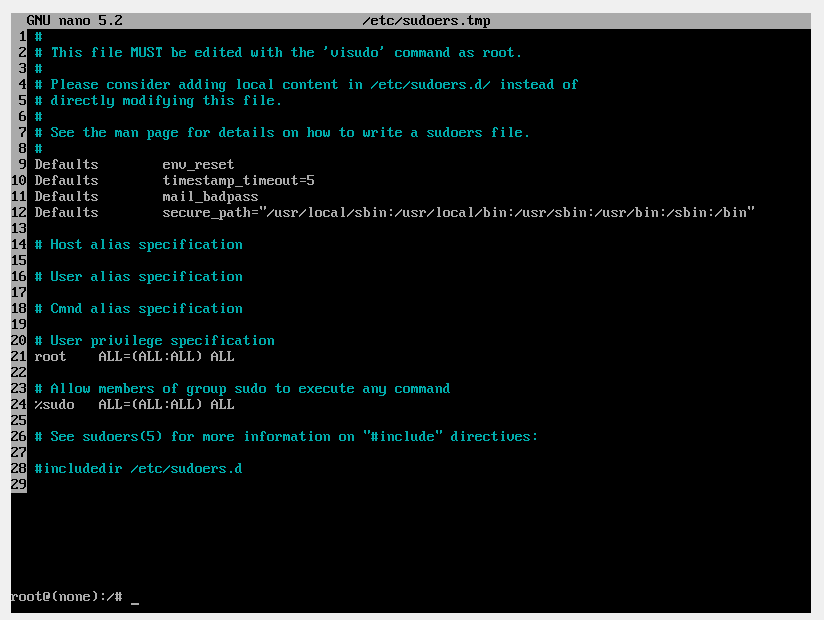
Next to power off the machine and boot it again normally.
Lesson learnt.